* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Network Security For Distributed Simulation Systems
Access control wikipedia , lookup
One-time pad wikipedia , lookup
Quantum key distribution wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Information privacy law wikipedia , lookup
Web of trust wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Authentication wikipedia , lookup
Unix security wikipedia , lookup
Certificate authority wikipedia , lookup
Wireless security wikipedia , lookup
Cryptanalysis wikipedia , lookup
Electronic authentication wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Diffie–Hellman key exchange wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer security wikipedia , lookup
Cryptography wikipedia , lookup
Mobile security wikipedia , lookup
History of cryptography wikipedia , lookup
Digital signature wikipedia , lookup
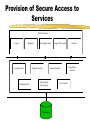
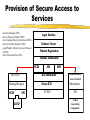
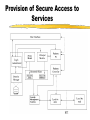
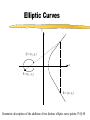
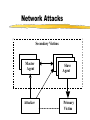
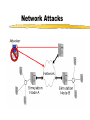
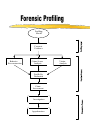
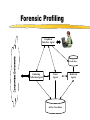
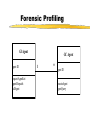
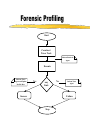
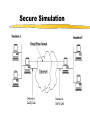
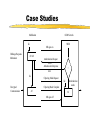
Security for Internet and Web Based Application Richard N. Zobel Department of Computer Science University of Manchester Oxford Road Manchester, M13 9PL, UK Email: [email protected] For The 4th International Conference on Information Integration and Web-based Applications and Services September 10-12, 2002 Outline Introduction. Provision of Secure Access to Services. Encryption and Decryption of Messages. Current System Technical Problems. Security Issues. Digital Signatures. Digital Watermarks. Network Attacks. Case Studies. Introduction WWW Provides Easy Access and Communication Requires Responsibility Mischief and Criminal Activities Opportunities and Problems of Provision of Security Compromise between Privacy and (Inter)National Interests Private Security and National Security Conflicts Human Rights Issues, Data Protection E-Business Emphasis on Communicating Users - Initially for Simulators Provision of Secure Access to Services Initial Login and Password Only Allows Access to the Registration Process Further Security Required for Various Activities Related to Required Services 3 - Tiered Process GUI - the Interface Servlets for User Choices Security DataBase Access Provision of Secure Access to Services GUI Interfaces Login Register LoginServlet ExRegServlet Ex. Registration Option1Servlet Forgot Password Option2Servlet Encryption/ Decryption Database User Token Visitors ForgotPass Servlet Provision of Secure Access to Services The following figures illustrate the Authentication Process: The Secure Federate Architecture The Software Implementation of the Architecture The Principle Concerns the Provision and Acceptance of Personal Details: E.g. Those used by Current Banking Systems or their Equivalent Short Cuts, Through PIN Codes are Allowed unless Compromised Authentication May also be through Digital Signatures, Authentication and Digital Certificates Provision of Secure Access to Services -Security Manager (SM) -Secure Protocol Handle (SPH) -Java Naming Directory Interface (JNDI) -Service Provider Interface (SPI) -Light Weight Directory Access Protocol (LDAP) -Java Native Interface (JNI) Login Interface Federate Viewer Federate Registration Federate Ambassador JNDI JNDI API Naming Manager JNDI SPI LDAP SM SPH RTIAmbassador Authentication / Access Control Secure RTI Mechanism TCP/IP JNI Token Generating Component Provision of Secure Access to Services Encryption and Decryption of Messages Symmetric Keys Problems - Use Fast Computers to Crack Codes Asymmetric Keys Public and Private Keys RSA (Rivest-Shamir-Adleman) - Uses Integer Factorisation Given Public (Encryption) Key - Difficult to Determine Private (Decryption) Key Degree of Difficulty relates to Number of Bits 1024 bits gives a Reasonable Degree of Security RSA Algorithm Two distinct primes pi and qi are selected then φ(pi)= pi-1, and φ(qi)= qi-1 if gcd(pi, qi )=1 then φ(pi qi)=φ(pi)•φ(qi) where φ(n) is called the Euler phi function, gcd is the greatest common divisor If pi and qi are each 1024 bit long, it is almost impossible, given present technology, to factor the modulus into pi and qi . The sender chooses: Public key ei such that ei ≤ pi • qi where ei and φ(pi• qi) are relatively prime. Private key di is computed such that ei ∙di=1(mod(pi -1)•(qi -1)). The encryption function is e(pt)=pt^di mod pi• qi where pt is the plaintext and pt< pi • qi. The decryption function d(ct)=ct ^ ei mod pi • qi where ct is the cipher text. The sender has public key pair (pi • qi , ei) and private key di The receiver has access to the public key of the sender Elliptic Curves An elliptic curve is defined by an equation of the form: 2 3 y = x + ax + b Elliptic Curves y Q = (x 2 , y2 ) x P = (x 1 , y1 ) R = (x 3 , y3 ) Geometric description of the addition of two distinct elliptic curve points: P+Q=R Current System Technical Problems Security Level and Cost Balance No guarantee Clever Mathematics Privacy and the Security Services Criminal and Law Enforcement Conflict between private individuals/organisations and security services Human rights, data protection, computer firewalls, private protection Expect criminals to be detected and punished Security, Secrecy and Confidentiality National and Cultural Differences Digital Signatures Equivalent to hand written signature ( but more repeatable !) More secure and useful: Non-repudiation Guarantees of Authenticity and Integrity of data Signature Derived from both the data and the signer, who has the public key Does not guarantee the signer is the owner of the public key This can be guaranteed by the use of Digital Certificates Identity Certificates (eg X.509) - public key and sufficient data to identify the key holder Accreditation - Identifies key holder as a group holder eg Doctor Authorisation – Used for delegation of authority Digital Signatures Certification Authority (CA) – An agent of trust in a Public Key Infrastructure (PKI) Verifies user’s identities Issues keys to users Certifies users public keys Publishes users Certificates Issues Certificates revocation lists Digital Signatures Private Key Public Key Message Hash Algorithm Message Digest Asymmetric Cipher Digital Signature Asymmetric Cipher Compare Hash Algorithm Digital Signature Creation Digital Signature Verification Digital Watermarks New area - ~ 7 years old Original watermark use – prevention of copying of bank notes and legal documents Digital watermarks now have wider applications Copyright protection images, text, multimedia data Identification of data ownership Identification of those who handle or receive it Tracing and proof of ownership Guaranteeing that images and data have not been tampered with Proliferation of the use of “invisible” watermarking Identification and protection against attack Digital Watermarks Initial Applications in imaging Systematically modifying and image in minor ways imperceptible to the eye Geometric modifications Stochastic modifications Spatial or frequency domain modifications Example of bank notes Limitations Capacity to discretely contain the watermark Open to attack by use of image processing techniques Identify presence of watermark Attempt to remove watermark Digital Watermarks Applications Images Sequence of images (subliminal !) Any data, including text and figures (.ps, .pdf .doc, .rtf, etc) Map Errors Deliberate Identification for Copyright O.S. (Ordnance Survey) Maps Euro currency notes - map of Europe Network Attacks Disclosure of data, mis-use of data Intruder attack More common - credit card details, use of private email Any data, including text and figures (.ps, .pdf .doc, .rtf, etc) Corruption of data - Virus attack Destruction Modification Interception Denial of Service Attack Network Attacks Secondary Victims Master Agent Attacker Slave Agent Primary Victim Network Attacks Forensic Profiling Involves identifying, preserving and analysing digital evidence In a way which could lead to the profiling and conviction of offenders Profiling gives a general biographical description of the most likely type of unknown offender Two types of profiling Inductive - scientific approach using experimental, statistical, correlation analysis Deductive - based on forensic evidence pointing to a particular crimescene and the behavioral reconstruction of the possible offender Problems Lack of standards, poor analysis techniques, lack of specialists and inadequate training. Forensic Profiling Profiling Model Forensic Evidence Behavior Reconstruction Crime Scene Analysis Profile By Deduction Crime Assessment Investigation Apprehension Victim Analysis Forensic Profiling Graphical Interface Agent Profile -Bas e Gathering Collection Agent Trace Agent Active Case-Base Retrieval Agent Forensic Profiling GI Agent agent ID requestAgentList agentDispatch killAgent GC Agent 1 * agent ID executeAgent agentQuery Forensic Profiling GI Age nt GC Age nt est ablish connect ion() [if connect ed] get Agent List () select Agent (), configureAgent () disp at chAgent (agent ID,configInfo) act ivat eAgent (), st art Execut ion() , get Result t () st op Agent () Forensic Profiling Start Construct Trace Task Inform Retrieval Agent Execute Informs Trace Agent and Update Profile-Base Yes any Link Success No Inform Trace Agent Failure Stop Secure Simulation Secure Simulation Case Studies 1. Mobile Phones Analog phones had little or no security Digital phones offer much better prospects Current GSM phones offer some relatively unsophisticated protocol and encryption standards As shown in the following figures Ki is the subscriber’s authentication key A3 Algorithm is the signal response calculation (SRES) A5 Algorithm is the keystream generation calculation A8 Algorithm is the cyphering key calculation (Kc) Case Studies Mobilisation Ki Challenge Response Mechanism GSM Network SRES MS signs on A3+A8 Authentication Request RAND Authentication Response = SRES Kc Ciphering Mode Request Kc Encrypted Communication Ciphering Mode Complete A5 Authentication results A5 MS signs off Case Studies Plaintext Asymmetric Cipher Public Key Ciphertext Asymmetric Cipher Private Key Plaintext Case Studies Mobile Station GSM Network 1: MS request access to GSM network 2: GSM network generates data for MS to encrypt 3: MS encrypts data with its private key and returns data to network 4: GSM network decrypts data using the public key in the certificate 5: If data is the same as the original then authentication is successful Case Studies 2. Distributed Interactive Simulation Involves real-time interconnection of simulations and simulators on the network Initially developed for military systems - use ATM private networks Many civil applications - use Internet, lack security Use Internet Protocol Security (IPSEC) end-to-end mechanism for protecting data using tunneling Alternatively use a virtual private network (simulates a private network over a public network such as the Internet) VPN, which can be enhanced through use of encryption and firewall and tunneling mechanisms Case Studies 3. Distance Learning New research at Manchester (Computer Science) Employs a remote and powerful simulation tool, which acts as a server, spawning simulations for use by course developers and students Local use of an animator, which provides for interactive use of simulations running elsewhere in the network Can be used for diverse dynamic systems simulation for continuous, discrete event or mixed systems in fields as diverse as mechanical engineering, finance and scheduling. Conclusions Security for Internet and Web based systems and users is now a major priority issue Two Central Issues Achieving Secure Access to Systems Achieving Secure Access to Data Four Central Facilities Authentication Certification Digital Certificates Trusted Certification Authority Conclusions All of these are needed for support of secure e-business and ecommerce. Digital watermarks are of increasing importance Attack problems Standards are needed Some widely differing case studies have been presented. These illustrate the importance of networking and associated security issues.