Configuring Security Access Control Lists
... All ACLs have an implicit deny entry at the end of the ACL, so, unless you explicitly permit it, traffic cannot pass. For example, if you want to allow all users to access a network through the ACE except for those users with particular IP addresses, then you must deny the particular IP addresses in ...
... All ACLs have an implicit deny entry at the end of the ACL, so, unless you explicitly permit it, traffic cannot pass. For example, if you want to allow all users to access a network through the ACE except for those users with particular IP addresses, then you must deny the particular IP addresses in ...
Mesaje de eroare
... Internet Connection Sharing cannot be enabled. The LAN connection selected as the private network is either not 783 N/A present, or is disconnected from the network. Please ensure that the LAN adapter is connected before enabling Internet Connection Sharing You cannot dial using this connecti ...
... Internet Connection Sharing cannot be enabled. The LAN connection selected as the private network is either not 783 N/A present, or is disconnected from the network. Please ensure that the LAN adapter is connected before enabling Internet Connection Sharing You cannot dial using this connecti ...
IPsec – An Introduction
... creating the IPsec SAs used to encrypt (for ESP) the data between the 2 peers If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
... creating the IPsec SAs used to encrypt (for ESP) the data between the 2 peers If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
Firewalls - Andrew.cmu.edu - Carnegie Mellon University
... Violations are activities or behaviors not permitted in the policy • these can be either explicit or implied ...
... Violations are activities or behaviors not permitted in the policy • these can be either explicit or implied ...
What is network management?
... Vulnerability Note VU#4923: The Microsoft SNMP agent, prior to Windows NT 4.0 Service Pack 4.0, will leak memory. An intruder can craft a malicious SNMP packet and consume memory on a victim host. Solution is to upgrade to Windows NT service pack 4 or later. Vulnerability Note VU#173910: A vulnerabi ...
... Vulnerability Note VU#4923: The Microsoft SNMP agent, prior to Windows NT 4.0 Service Pack 4.0, will leak memory. An intruder can craft a malicious SNMP packet and consume memory on a victim host. Solution is to upgrade to Windows NT service pack 4 or later. Vulnerability Note VU#173910: A vulnerabi ...
Open_Id
... Limitation of OpenID & Possible Solutions. • Phishing • A distrusted site redirects you to your trusted provider through a proxy. Possible Solutions • Trusted and Security features by OpenID provider • Jabber • Microsoft card space • DynDNS ...
... Limitation of OpenID & Possible Solutions. • Phishing • A distrusted site redirects you to your trusted provider through a proxy. Possible Solutions • Trusted and Security features by OpenID provider • Jabber • Microsoft card space • DynDNS ...
MIS9eCC08
... your own personal possessions, and not to be observed without your consent Dimensions of privacy ...
... your own personal possessions, and not to be observed without your consent Dimensions of privacy ...
RADIUS Implementation and Deployment Best Practices
... If it is not possible to use the Message-Authenticator attribute for all Access-Request messages, then use an authentication counting and lockout mechanism. An example is remote access account lockout in Windows 2000, which prevents a user from making remote access connections after a specified numb ...
... If it is not possible to use the Message-Authenticator attribute for all Access-Request messages, then use an authentication counting and lockout mechanism. An example is remote access account lockout in Windows 2000, which prevents a user from making remote access connections after a specified numb ...
Ingate Firewall & SIParator Training
... The popularity of SIP Trunks is due primarily to the cost savings; due to a true convergence of voice and data infrastructure, Increased ROI, the maximizing of bandwidth utilization, open source protocol standards, and more. ...
... The popularity of SIP Trunks is due primarily to the cost savings; due to a true convergence of voice and data infrastructure, Increased ROI, the maximizing of bandwidth utilization, open source protocol standards, and more. ...
Technical Presentation
... The popularity of SIP Trunks is due primarily to the cost savings; due to a true convergence of voice and data infrastructure, Increased ROI, the maximizing of bandwidth utilization, open source protocol standards, and more. ...
... The popularity of SIP Trunks is due primarily to the cost savings; due to a true convergence of voice and data infrastructure, Increased ROI, the maximizing of bandwidth utilization, open source protocol standards, and more. ...
DNS Security Considerations and the Alternatives to BIND
... The entire Internet depends on Domain Name System (DNS). Without DNS, the Internet users cannot access the Internet without resolving all the hostname into IP address while at the same time other external networks also cannot access your public servers. If the web server becomes inaccessible, people ...
... The entire Internet depends on Domain Name System (DNS). Without DNS, the Internet users cannot access the Internet without resolving all the hostname into IP address while at the same time other external networks also cannot access your public servers. If the web server becomes inaccessible, people ...
JTC 1 Security and Privacy
... (including evaluation criteria for IT security, framework for IT security assurance, methodology for IT security evaluation, cryptographic algorithms and security mechanisms conformance testing, security assessment of operational systems, SSECMM, vulnerability disclosure, vulnerability handling proc ...
... (including evaluation criteria for IT security, framework for IT security assurance, methodology for IT security evaluation, cryptographic algorithms and security mechanisms conformance testing, security assessment of operational systems, SSECMM, vulnerability disclosure, vulnerability handling proc ...
Distilling Data in a SIM: A Strategy for the Analysis
... passing events along to the Manager, connectors aggregate some events and filter out others. These settings are set on the connectors themselves during installation. They can be changed from the Console (by those with the proper permissions). ...
... passing events along to the Manager, connectors aggregate some events and filter out others. These settings are set on the connectors themselves during installation. They can be changed from the Console (by those with the proper permissions). ...
Network Security (Firewall)
... layer and ensures that these contents match the rules in company's network security policy. A stateful inspection firewall allows a direct connection between a trusted client and an untrusted host. And it relies on algorithms to recognize and process application-layer data. These algorithms compare ...
... layer and ensures that these contents match the rules in company's network security policy. A stateful inspection firewall allows a direct connection between a trusted client and an untrusted host. And it relies on algorithms to recognize and process application-layer data. These algorithms compare ...
Unraveling the B2B Process
... This will include acquiring and maintaining the circuit to the B2B gateway and acquiring a Virtual Private Network (VPN) deice compatible with the MHS VPN device. 3. Contractors will comply with DoD guidance regarding allowable ports, protocols and risk mitigation strategies. 4. All cost for VPN har ...
... This will include acquiring and maintaining the circuit to the B2B gateway and acquiring a Virtual Private Network (VPN) deice compatible with the MHS VPN device. 3. Contractors will comply with DoD guidance regarding allowable ports, protocols and risk mitigation strategies. 4. All cost for VPN har ...
Slide 1
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
EE579T-Class 4
... • All cryptosystems depend on the security of the key for their security – If a symmetric system, he who has the key reads the mail – Asymmetric systems rely on the private remaining private. How good an assumption is this? ...
... • All cryptosystems depend on the security of the key for their security – If a symmetric system, he who has the key reads the mail – Asymmetric systems rely on the private remaining private. How good an assumption is this? ...
Slide 1
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
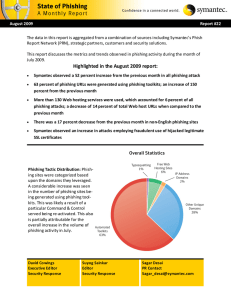
Highlighted in the August 2009 report
... Unique Phishing Web site: The phishing Websites that have a unique Web page are classified as “Unique Phishing Websites”. URLs from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites ...
... Unique Phishing Web site: The phishing Websites that have a unique Web page are classified as “Unique Phishing Websites”. URLs from phishing toolkits that randomize their URL string are observed to point to the same Web page and do not contain a unique Web page in each URL. Unique Phishing websites ...
Why write exploits?
... dll.BaseAddress = 0x77f00000 dll.Address['JMP ESP'] = 0x77F32836 dll.Address['JMP EDI'] = 0x77F2D148 dll.Address['CALL EAX'] = 0x77F1A9DD dll.Address['JMP [EBX]'] = 0x77F0174A dll.Address['CALL EBX'] = 0x77F01089 dll.Address['JMP ECX'] = 0x77F05372 dll.Address['JMP [EAX]'] = 0x77F08070 dll.Address[' ...
... dll.BaseAddress = 0x77f00000 dll.Address['JMP ESP'] = 0x77F32836 dll.Address['JMP EDI'] = 0x77F2D148 dll.Address['CALL EAX'] = 0x77F1A9DD dll.Address['JMP [EBX]'] = 0x77F0174A dll.Address['CALL EBX'] = 0x77F01089 dll.Address['JMP ECX'] = 0x77F05372 dll.Address['JMP [EAX]'] = 0x77F08070 dll.Address[' ...
Reed - Virtual Local Area Networks in Security
... enterprise. It is common for different departments or groups to work together in organizations on certain projects that may last only a small amount of time. In order to reduce the amount of multicast and broadcast packets being sent over the network these users can be added to a VLAN which will dec ...
... enterprise. It is common for different departments or groups to work together in organizations on certain projects that may last only a small amount of time. In order to reduce the amount of multicast and broadcast packets being sent over the network these users can be added to a VLAN which will dec ...
PLCsecurity_@_ABT-ABOC_20070122 - Indico
... Control-System Cyber-Security (CS)2 ― [email protected] (CERN IT/CO) ― ATC/ABOC Days ─ 2007/1/22 ...
... Control-System Cyber-Security (CS)2 ― [email protected] (CERN IT/CO) ― ATC/ABOC Days ─ 2007/1/22 ...