Computer Systems Security
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
Emerging Threats to Business Security
... file sharing, however, may carry productivity costs. Installing antivirus on every computer which shares files (be it a desktop or a fileserver) is highly recommended Spam is diversifying and evolving, in hopes of avoiding spam filters by constant variation coupled with heavy obfuscation of both con ...
... file sharing, however, may carry productivity costs. Installing antivirus on every computer which shares files (be it a desktop or a fileserver) is highly recommended Spam is diversifying and evolving, in hopes of avoiding spam filters by constant variation coupled with heavy obfuscation of both con ...
Overview of Operating Systems Security Features
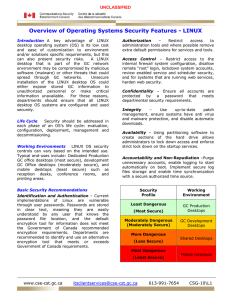
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
Security Resume - Kirubha Shankar Murugesan
... Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 Ornamented both the RSA and MD5 algorithm with optimum speed and efficiency. Studied various Penetration testing techniques using Kali OS that can be applied to any n ...
... Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 Ornamented both the RSA and MD5 algorithm with optimum speed and efficiency. Studied various Penetration testing techniques using Kali OS that can be applied to any n ...
slides - University of Cambridge Computer Laboratory
... – pattern of activity from China much more complex than needed for deniability – pattern of intelligence priorities disclosed by Canadian compromise of the Chinese control server ...
... – pattern of activity from China much more complex than needed for deniability – pattern of intelligence priorities disclosed by Canadian compromise of the Chinese control server ...
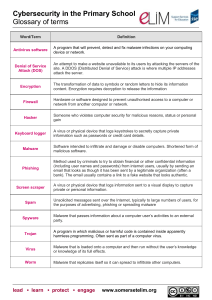
ITS_8_Security Vocab Answers
... of data into a secret code. Encryption is the most effective way to accomplish data security. If one wants to read an encrypted file, they must have access to the key or password that enables them to decrypt the file. Unencrypted data is often called plain text. Once encrypted it is referred to as c ...
... of data into a secret code. Encryption is the most effective way to accomplish data security. If one wants to read an encrypted file, they must have access to the key or password that enables them to decrypt the file. Unencrypted data is often called plain text. Once encrypted it is referred to as c ...
How mobile communications work
... Logs are displayed by categories and sorted for easy browsing. ...
... Logs are displayed by categories and sorted for easy browsing. ...
Do you know someone may be watching you?
... ◦ networking and system techniques ◦ applied cryptography ◦ machine learning ◦ probability/statistics ◦ information theory ◦ graph theory ...
... ◦ networking and system techniques ◦ applied cryptography ◦ machine learning ◦ probability/statistics ◦ information theory ◦ graph theory ...
Section for introduction % \section{Introduction} Over the last several
... threat into our approach as well. As with kernel-mode rootkits, a onetime physical access installation or remote exploit could be leveraged to install this user-mode malware. The exploit would then be capable of modifying the startup configuration file to persist execution across reboots of the Andr ...
... threat into our approach as well. As with kernel-mode rootkits, a onetime physical access installation or remote exploit could be leveraged to install this user-mode malware. The exploit would then be capable of modifying the startup configuration file to persist execution across reboots of the Andr ...
CH 8 – Review - WordPress.com
... Botnet is short for robot network – True A person who runs a botnet is called a – botmaster Botnets are created using self-propagating software, which means that the software can – reproduce itself A good defense to prevent your computer from becoming a zombie is to – install and run antivirus softw ...
... Botnet is short for robot network – True A person who runs a botnet is called a – botmaster Botnets are created using self-propagating software, which means that the software can – reproduce itself A good defense to prevent your computer from becoming a zombie is to – install and run antivirus softw ...
Dan A CSC 345 Term Paper
... run. Viruses and worms can have a variety of effects, including deleting files, corrupting data, accessing private information, and sending spam. A Trojan horse is a program that is disguised as being benign, but allows other users to connect without being detected. The cost of having an infected o ...
... run. Viruses and worms can have a variety of effects, including deleting files, corrupting data, accessing private information, and sending spam. A Trojan horse is a program that is disguised as being benign, but allows other users to connect without being detected. The cost of having an infected o ...
Open ended challenge rationale
... A virus or physical device that logs keystrokes to secretly capture private information such as passwords or credit card details. ...
... A virus or physical device that logs keystrokes to secretly capture private information such as passwords or credit card details. ...