* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Computer Systems Security
Security-focused operating system wikipedia , lookup
Trusted Computing wikipedia , lookup
Microsoft Security Essentials wikipedia , lookup
Computer security wikipedia , lookup
Cyberattack wikipedia , lookup
Unix security wikipedia , lookup
Computer virus wikipedia , lookup
Antivirus software wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
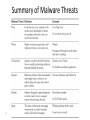
Computer Systems Security Part I ET4085 Keamanan Jaringan Telekomunikasi Tutun Juhana School of Electrical Engineering and Informatics Institut Teknologi Bandung Computer systems security is all about the security threats that can compromise an operating system and the data held within Threats: viruses, Trojans, and spyware are 2 COMPUTER SYSTEMS SECURITY THREATS 3 Malicious Software • Malicious software, or malware, is software designed to infiltrate a computer system and possibly damage it without the user’s knowledge or consent – – – – – – – 4 Viruses Worms Trojan horses Spyware Rootkits Adware and other types of undesirable software. Viruses • A virus is code that runs on a computer without the user’s knowledge; it infects the computer when the code is accessed and executed • For viruses to do their dirty work, they first need to be executed by the user in some way – A virus needs some sort of carrier • A virus also has reproductive capability and can spread copies of itself throughout the computer if it is first executed by the user • By infecting files accessed by other computers, the virus can spread to those other systems as well 5 • Viruses types – Boot sector - Initially loads into the first sector of the hard drive; when the computer boots, the virus then loads into memory. – Macro - Usually placed in documents and e-mailed to users in the hopes that the user will open the document, thus executing the virus. – Program - Infects executable files 6 • Viruses types (2) – Polymorphic - Can change every time is it executed in an attempt to avoid antivirus detection. – Stealth - Uses various techniques to go unnoticed by antivirus programs. – Armored - These protect themselves from antivirus programs by tricking the program into thinking that it is located in a different place from where it actually resides • Essentially, it has a layer of protection that it can use against the person who tries to analyze it; it will thwart attempts by analysts to examine its code. – Multipartite - A hybrid of boot and program viruses that attacks the boot sector or system files first and then attacks the other 7 Worms • Worms are much like viruses except they self-replicate whereas a virus does not • With worms, the user doesn’t need to access and execute the malware • Worms take advantage of backdoors and security holes in operating systems and applications – They look for other systems on the network or through the Internet that are running the same applications and replicate to those other systems 8 Trojan Horses 9 • Trojan horses, or simply Trojans, appear to perform wanted functions but are actually performing malicious functions behind the scenes • These are not technically viruses and can easily be downloaded without noticing them 10 • Remote access Trojans (RATs) are the most common type of Trojan (ex: Back Orifice or NetBus) – their capability to allow an attacker higher administration privileges than the owner • When a target computer is controlled by an attacker, it could easily become a robot (or simply a bot), carrying out the plans of the attackers at their command 11 Spyware • Spyware is a type of malicious software either downloaded unwittingly from a website or installed along with some other third-party software • Usually, this malware collects information about the user without the user’s consent. • Spyware is also associated with advertising (those pop-ups that just won’t go away!) and could possibly change the computer configuration – Adware usually falls into the realm of spyware because it pops up advertisements based on what it has learned from spying on the user • Grayware is another general term that describes applications that are behaving improperly but without serious consequences – It is associated with spyware, adware, and joke programs 12 Rootkits • A rootkit is a type of software designed to gain administrator-level control over a computer system without being detected – The term is a combination of the words “root” (meaning the root user in a UNIX/Linux system or administrator in a Windows system) and “kit” (meaning software kit) – Usually, the purpose is to perform malicious operations on a target computer at a later date without the knowledge of the administrators or users of that computer 13 • Rootkits are difficult to detect because they are activated before the operating system has fully booted • A rootkit might install hidden files, processes, and hidden user accounts. • Because rootkits can be installed in hardware or software, they can intercept data from network connections, keyboards, and so on 14 • Rootkits can target the BIOS, boot loader, kernel, and more • Example: Evil Maid 15 Spam • Spam is the abuse of electronic messaging systems such as e-mail, broadcast media, instant messaging, and so on • Spammers send unsolicited bulk messages indiscriminately, usually without benefit to the actual spammer, because the majority of spam is either deflected or ignored • The bulk of network-based viruses are transferred through spam emails 16 Summary of Malware Threats 17 WAYS TO DELIVER MALICIOUS SOFTWARE 18 • Malware is not sentient (...not yet) and can’t just appear out of thin air • it needs to be transported and delivered to a computer or installed on a computer system in some manner 19 – Direct physical access – Via Software, Messaging, and Media – Active Interception – Privilege Escalation – Backdoors – Logic Bombs – Botnets and Zombies 20 21 Direct physical access 22 Via Software, Messaging, and Media 23 Active Interception (inception) the act of exploiting a bug or design flaw in a software or firmware application to gain access to resources that normally would’ve been protected from an application or user 24 Privilege Escalation Backdoors are used in computer programs to bypass normal authentication and other security mechanisms in place Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse Example: Back Orifice (completely new application that would act as a backdoor), which enables a user to control a Windows computer from a remote location. 25 Backdoors Logic bombs are code that has, in some way, been inserted into software to initiate one of many types of malicious functions when specific criteria are met malware delivery system malware 26 Logic Bombs malware can be distributed throughout the Internet by a group of compromised computers known as a botnet (controlled by a master computer (where the attacker resides)) The individual compromised computers in the botnet are called zombies Leads to distributed denial of service (DDoS) 27 Botnets and Zombies Columbo is an American detective mystery television film series, starring Peter Falk as Columbo, a homicide detective with the LAPD (wikipedia) 28