Configuring Security Access Control Lists
... All ACLs have an implicit deny entry at the end of the ACL, so, unless you explicitly permit it, traffic cannot pass. For example, if you want to allow all users to access a network through the ACE except for those users with particular IP addresses, then you must deny the particular IP addresses in ...
... All ACLs have an implicit deny entry at the end of the ACL, so, unless you explicitly permit it, traffic cannot pass. For example, if you want to allow all users to access a network through the ACE except for those users with particular IP addresses, then you must deny the particular IP addresses in ...
Mesaje de eroare
... Network Address Translation (NAT) is currently installed as a 782 N/A routing protocol, and must be removed before enabling Internet Connection Sharing Internet Connection Sharing cannot be enabled. The LAN connection selected as the private network is either not 783 N/A present, or is disc ...
... Network Address Translation (NAT) is currently installed as a 782 N/A routing protocol, and must be removed before enabling Internet Connection Sharing Internet Connection Sharing cannot be enabled. The LAN connection selected as the private network is either not 783 N/A present, or is disc ...
What is network management?
... to either upgrade to version 0.10.5 or later, or to disable SNMP protocol dissector. Vulnerability Note VU#329230: A vulnerability exists in multiple Symantec security appliances that could allow a remote attacker to bypass the firewall using a source port of 53/udp. Solution according to the Symant ...
... to either upgrade to version 0.10.5 or later, or to disable SNMP protocol dissector. Vulnerability Note VU#329230: A vulnerability exists in multiple Symantec security appliances that could allow a remote attacker to bypass the firewall using a source port of 53/udp. Solution according to the Symant ...
staff symposium series
... Surfing the Web: Don’ts Don't download data from doubtful sources Don't visit untrustworthy sites out of curiosity, or access the URLs provided in those websites Don't use illegal software and programs Don't download programs without permission of the copyright owner or licensee (e.g. Torrent ...
... Surfing the Web: Don’ts Don't download data from doubtful sources Don't visit untrustworthy sites out of curiosity, or access the URLs provided in those websites Don't use illegal software and programs Don't download programs without permission of the copyright owner or licensee (e.g. Torrent ...
EC Council CHFI Certification: Course CF220
... • A three-homed firewall DMZ handles the traffic between the internal network and firewall, as well as the traffic between the firewall and DMZ • A site survey can be conducted to determine the proper number of access points needed based on the expected number of users and the specific environment f ...
... • A three-homed firewall DMZ handles the traffic between the internal network and firewall, as well as the traffic between the firewall and DMZ • A site survey can be conducted to determine the proper number of access points needed based on the expected number of users and the specific environment f ...
Distilling Data in a SIM: A Strategy for the Analysis
... vulnerabilities. Relevance depends on whether the asset has been scanned or not and whether the target has the targeted port open or is vulnerable to the attack shown by the event. Asset criticality depends on whatever criticality was assigned when the asset was modeled. Severity depends on what is ...
... vulnerabilities. Relevance depends on whether the asset has been scanned or not and whether the target has the targeted port open or is vulnerable to the attack shown by the event. Asset criticality depends on whatever criticality was assigned when the asset was modeled. Severity depends on what is ...
F5 Silverline Protect Your Business and Stay Online
... to protect organizations against the full spectrum of modern DDoS attacks. This hybrid DDoS protection solution from F5 combines industry-leading DDoS protection solutions on premises for detecting and mitigating mid-volume, SSL, or application-targeted attacks— with the high-capacity Silverline DDo ...
... to protect organizations against the full spectrum of modern DDoS attacks. This hybrid DDoS protection solution from F5 combines industry-leading DDoS protection solutions on premises for detecting and mitigating mid-volume, SSL, or application-targeted attacks— with the high-capacity Silverline DDo ...
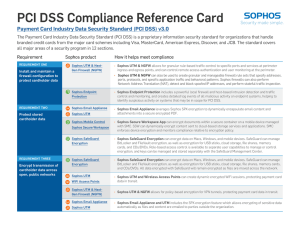
PCI DSS Compliance Reference Card
... ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, and perform stateful traffic inspection. ...
... ports, protocols, and specific application traffic and behavioral patterns. Sophos firewalls can also perform Network Address Translation (NAT), detect and block spoofed IP addresses, and perform stateful traffic inspection. ...
The Internet and Its Uses
... • Each vulnerability is given an ID and can be reviewed by network security professionals over the Internet. • The common vulnerability exposure (CVE) list also publishes ways to prevent the vulnerability from being ...
... • Each vulnerability is given an ID and can be reviewed by network security professionals over the Internet. • The common vulnerability exposure (CVE) list also publishes ways to prevent the vulnerability from being ...
Chapter 02: The Need for Security
... 7. Hackers are “people who use and create computer software to gain access to information illegally.” _________________________ ANS: T ...
... 7. Hackers are “people who use and create computer software to gain access to information illegally.” _________________________ ANS: T ...
Junos Pulse Access Control Service
... Network Security and Application Access Control Integration The Junos Pulse Access Control Service leverages additional network components to ensure secure context aware network and application access control, address specific use cases, and centralize network policy management. It integrates with ...
... Network Security and Application Access Control Integration The Junos Pulse Access Control Service leverages additional network components to ensure secure context aware network and application access control, address specific use cases, and centralize network policy management. It integrates with ...
Era of Spybots - A Secure Design Solution Using
... functioning workstation, suggested the possibility of a ...
... functioning workstation, suggested the possibility of a ...
Easy Steps to Cisco Extended Access List
... a recommended port block, monitor the port in your Intrusion Detection System at the DMZ to ensure that the port is not use by legitimate services. Permitting only allowed services and denying all others will be better practice for network security. Recommend frequently visiting security websites, s ...
... a recommended port block, monitor the port in your Intrusion Detection System at the DMZ to ensure that the port is not use by legitimate services. Permitting only allowed services and denying all others will be better practice for network security. Recommend frequently visiting security websites, s ...
M3AAWG Anti-Abuse Best Common Practices for Hosting and Cloud
... support. The customer controls administrative and end-user access. ● Reseller Hosting An arrangement under which the hosting company provides space to a customer who acts as an independent hosting company. The business arrangement can be either unmanaged or dedicated hosting, as detailed above. Cust ...
... support. The customer controls administrative and end-user access. ● Reseller Hosting An arrangement under which the hosting company provides space to a customer who acts as an independent hosting company. The business arrangement can be either unmanaged or dedicated hosting, as detailed above. Cust ...
CSCE 790 – Secure Database Systems
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
... against a Member of the United Nations, until the Security Council has taken measures necessary to maintain international peace and security. Measures taken by Members in the exercise of this right of self-defense shall be immediately reported to the Security Council and shall not in any way affect ...
How to Detect Mainframe Intrusion Attempts
... Most of the users are oblivious to the design of the Internet and its components and only use the services provided by their operating system or applications. However, there is a small minority of advanced users who use their knowledge to exploit potential system vulnerabilities. With time and adequ ...
... Most of the users are oblivious to the design of the Internet and its components and only use the services provided by their operating system or applications. However, there is a small minority of advanced users who use their knowledge to exploit potential system vulnerabilities. With time and adequ ...
SNMP (Simple Network Management Protocol)
... •Traps are unrequested event reports that are sent to a management system by an SNMP agent process •When a trappable event occurs, a trap message is generated by the agent and is sent to a trap destination (a specific, configured network address) •Many events can be configured to signal a trap, like ...
... •Traps are unrequested event reports that are sent to a management system by an SNMP agent process •When a trappable event occurs, a trap message is generated by the agent and is sent to a trap destination (a specific, configured network address) •Many events can be configured to signal a trap, like ...
PPT - Communications
... • Security model of SNMPv3 has two components: 1.Instead of granting access rights to a community, SNMPv3 grants access to users. 2. Access can be restricted to sections of the MIB (Versionbased Access Control Module (VACM). Access rights can be limited • by specifying a range of valid IP addresses ...
... • Security model of SNMPv3 has two components: 1.Instead of granting access rights to a community, SNMPv3 grants access to users. 2. Access can be restricted to sections of the MIB (Versionbased Access Control Module (VACM). Access rights can be limited • by specifying a range of valid IP addresses ...
Waukesha County Technical College
... You have decided to implement biometrics as part of your security system. Before purchasing a locking system that uses biometrics to control access to secure areas, you need to decide what will be used to authenticate users. What types rely solely on biometric authentication? ...
... You have decided to implement biometrics as part of your security system. Before purchasing a locking system that uses biometrics to control access to secure areas, you need to decide what will be used to authenticate users. What types rely solely on biometric authentication? ...