* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download What is network management?
Survey
Document related concepts
Transcript
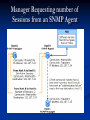
SIMPLE NETWORK MANAGEMENT PROTOCOL (SNMP) VIJAY CHAND UYYURU VENKAT KANCHERLA PRATEEK ARORA What is network management? Network management includes deployment, integration, and coordination of the hardware, software, and human elements to monitor, test, poll, configure, analyze, and control the network and element resources to meet the real-time , operational performance, and quality of service requirements at a reasonable cost. Five areas of network management Performance management : to quantify, measure, report, analyze and control the performance of network components. Fault management : to log, detect, and respond to fault conditions in the network. Configuration management : allows a network manager to track which devices are on the managed network and the hardware and software configurations of these devices. Accounting management : allows the network manager to specify, log, and control user and devices access to network resources. Security management : to control access to network resources according to some well defined policy. Protocols for Network management 1. 2. 3. 1. CMISE/CMIP (the Common Management Information Services Element/Common Management Information Protocol ) SNMP (Simple Network Management Protocol) Disadvantages of CMIP over SNMP the CMIP protocol takes more system resources than SNMP by a factor of ten CMIP is large and complete management system that only the best equipped networks can afford to run it. advantage of SNMP over CMIP is that its design is simple Disadvantages of SNMP Because it is so simple, the information it deals with is neither detailed, nor well organized enough to deal with the growing networks (corrected in later versions). Evolution of SNMP In early days of the ARPANET, they used ping to detect the problem. When ARPANET turned into WWW, better tools to network management are needed. SNMP provided a systematic way of monitoring and managing a computer network. Three versions in SNMP SNMPv1 : The initial implementation of the SNMP protocol, which is described in RFC 1098 and RFC 1157 SNMPv2 : An improved version of SNMPv1 that includes additional protocol operations for the SNMPv2 Structure of Management Information (SMI) (RFC 1441-1452) SNMPv3 : SNMPv3 has yet to be standardized What is SNMP? The Simple Network Management Protocol (SNMP) is an application-layer protocol that facilitates the exchange of management information between a network management system (NMS), agents, and managed devices. SNMP uses the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite. SNMP is a part of Internet network Architecture SNMP enables network administrators to manage network performance, find and solve network problems, and plan for network growth. Purpose of SNMP Although the original purpose of SNMP was to let network administrators remotely manage an Internet system, the design of SNMP lets network administrators manage applications as well as systems. Lets you manage and monitor all network components from one console Network management architecture Components of a managed network Managed nodes Agent Management stations Management Information Base (MIB) A management protocol Management stations General-purpose computers running special software The management station contain one or more processes that communicate with agents over the network, issuing commands and getting responses An NMS (network management station) executes applications that monitor and control managed devices. It controls the collection, processing, analysis, and display of network management information NMSs provide the bulk of the processing and memory resources required for network management. Managed device A managed device is a network node that contains an SNMP agent and that resides on a managed network Managed devices collect and store management information and make this information available to NMSs using SNMP A managed device might be a host, router, bridge, hub, printer, or modem. Agent a network-management software module that resides in a managed device that communicates with management stations. An agent has local knowledge of management information and translates that information into a form compatible with SNMP. SNMP Management information base Each device maintains one or more variables that describes its state. These variables are called objects. The collection of all objects in a network is given in a datastructure called MIB (management information base) MIBs are accessed using a network-management protocol such as SNMP and identified by object identifiers. The MIB hierarchy can be depicted as a tree with a nameless root, the levels of which are assigned by different organizations. When an SNMP manger requests information from an SNMP agent, the SNMP agent retrieves the current value of the requested information from the Management Information Base (MIB). Network management protocol The protocol runs between the managing entity and managed device. Allows managing entity to query the status of managed device Agents use it to inform the managing entity of exceptional events. Data are sent using the ASN.1(abstract syntax notation one) transfer syntax. The structure of management information, SMI, is the language used to define the management information residing in a managed-network entity. SMI is used to ensure that the syntax and semantics of the network management data are well defined. Windows Server 2003 SNMP Components at Each TCP/IP Layer Windows Server 2003 SNMP Components Component Name Associated Programs Component Type Description Microsoft SNMP Service Snmp.exe Agent Receives SNMP requests and delivers them to the appropriate SNMP subagent DLL for processing. The service is also responsible for intercepting events (traps) from the SNMP subagents and forwarding trap messages to the appropriate management systems. SNMP Subagents Inetmib1.dll, Hostmib.dll, Lmmib2.dll, and others Agent Provides a set of entry points. When an SNMP request is received, the SNMP service delivers it to the appropriate subagent by calling one of these entry points. After the subagent processes the message, it passes the information back to the SNMP service, which then forwards the message to the SNMP manager. SNMP Utility API Snmpapi.dll Both Agent and Manager Provides utilities that the SNMP service uses for memory management operations, address-decoding routines, object identifier handling routines, and so forth. Provides a set of routines that SNMP subagents use to handle and order SNMP objects. Although use of the Snmpapi.dll is not required, the framework defined by this tool greatly facilitates the development of new SNMP subagents. SNMP Trap Service Snmptrap.exe Manager Uses the WinSNMP API to forward a trap message sent by an SNMP agent to the appropriate SNMP manager application Windows Server 2003 SNMP Components Component Name Associated Programs Component Type Description WinSNMP API -andManagement API Wsnmp32.dll -andMgmtapi.dll Manager Helps develop SNMP management software applications: •The WinSNMP API provides a set of functions for encoding, decoding, sending, and receiving SNMP messages .•The Management API is a simple API that resides on top of the WinSNMP and SNMP Utility APIs. It provides a limited set of functions that you can use to develop basic SNMP management applications quickly. SNMP Manager Application Snmputil.exe Manager Provides a basic command-line utility with which to retrieve information from any SNMP agent in your network. This example of a management application was developed using the Management API. SNMP Protocol Basics SNMP does not manage the network by itself but instead provides a tool for the manager to manage the corresponding devices. The preferred transport protocol for carrying SNMP messages is UDP and the preferred port number for the SNMP is port 161. Port 162 is used for trap messages. SNMP Management Systems and Agents SNMP manager: An SNMP manager, also known as an SNMP management system or a management console, is any computer that sends queries for IP-related information to a managed computer, known as an SNMP agent. SNMP agent: An SNMP agent is any computer or other network device that monitors and responds to queries from SNMP manager. The SNMP manager displays the information it receives. The SNMP agent does not display the information that it sends to an SNMP manager. SNMP Community To enable SNMP communications between an SNMP manager and SNMP agents, we configure the SNMP manager and the SNMP agents that it manages as members of an SNMP community. The community name functions like a password to authenticate communications between the SNMP manager and agent. The SNMP community is an SNMP-defined group. SNMP Community A community name acts as a password that is shared, typically by multiple SNMP agents and one or more SNMP managers. We configure the SNMP manager and the computers or devices that it manages as members of a single SNMP community. An SNMP agent only accepts requests from SNMP managers that are on the agents list of acceptable community names. Understanding the Management Information Base (MIB) When an SNMP manager requests information from an SNMP agent, the SNMP agent retrieves the current value of the requested information from the Management Information Base (MIB). The MIB defines the managed objects that an SNMP manager monitors on an SNMP agent. Each system in a network maintains a MIB that reflects the status of the managed resources on that system, such as the version of the software, amount of free hard drive space etc. Manager Requesting number of Sessions from an SNMP Agent Manager Requesting number of Sessions from an SNMP Agent 1. 2. The SNMP manager, Host A, forms an SNMP message that contains an information request(Get) for the number of active sessions, the name of the community to which the SNMP manager belongs, and the destination of the message – the IP address of the SNMP agent, Host B. The SNMP manager sends the information request to Host B by using the SNMP service libraries. Manager Requesting number of Sessions from an SNMP Agent 3. 4. When Host B receives the message, it verifies that the community name contained in the packet is on its list of acceptable community names, evaluates the request against the agents list of access permissions for that community, and verifies the source IP address. If the information is incorrect then the agent sends a trap message “authentication failure” to the specified trap destination, Host C. The master agent component of the SNMP agent calls the appropriate extension agent to retrieve the requested session information from the MIB. Manager Requesting number of Sessions from an SNMP Agent 5. 6. Using the session information that it retrieved from the extension agent, the SNMP service forms a return SNMP message that contains the number of active sessions and the destination – the IP address of the SNMP manager, Host A. Host B sends the response to Host A. Information Types An SNMP manager can request the following types of information from the SNMP agents that it monitors: Network protocol identification and statistics. Dynamic identification of devices attached to the network. Hardware and software configuration data. Device error and event messages. Program and application usage statistics. SNMP Messages 1. 2. SNMP sends operation requests and responses as SNMP messages. An SNMP message consists of an SNMP protocol data unit (PDU) plus additional message header elements defined by the relevant RFC. An SNMP agent sends information in two situations: When it responds to a request from an SNMP manager and When a trap event occurs. SNMP Message Types Get: Accesses and retrieves the current value of one or more MIB objects on an SNMP agent. GetResponse: Replies to a Get, GetNext, or Set operation. GetNext: Obtains the information from selected columns from one or more rows of a table. GetBulk: Accesses multiple values at one time without using GetNext message. Set: Changes the current value of an MIB object. Trap: Notifies the SNMP manager when an unexpected event occurs locally on the managed host. All the above messages except Trap and GetResponse are from Manager to Host. SNMP Message Types Message Sent Between an SNMP Manager and its Managed Devices SNMP Basic Message Format SNMP Message Header SNMPv2 message headers contain two fields: Version Number and Community Name. The following descriptions summarize these fields: Version number—Specifies the version of SNMP that is being used. Community name—Defines an access environment for a group of NMSs. NMSs within the community are said to exist within the same administrative domain. Community names serve as a weak form of authentication because devices that do not know the proper community name are precluded from SNMP operations. PDU Formats Get, GetNext, Response, Set, and Trap PDUs Contain the Same Fields. SNMP Protocol Data Unit (PDU) The following descriptions summarize the fields illustrated in Figure: PDU type—Identifies the type of PDU transmitted (Get, GetNext, Inform, Response, Set, or Trap). Request ID—Associates SNMP requests with responses. SNMP Protocol Data Unit (PDU) Error status—Indicates one of a number of errors and error types. Only the response operation sets this field. Other operations set this field to zero. Error index—Associates an error with a particular object instance. Only the response operation sets this field. Other operations set this field to zero. Variable bindings—Serves as the data field of the SNMPv2 PDU. Each variable binding associates a particular object instance with its current value (with the exception of Get and GetNext requests, for which the value is ignored). SNMP Applications Command generator: The command generator generates the GetRequest, GetNextRequest, GetBulkRequest, and SetRequest PDUs and handles the received responses to these PDUs. The command responder executes in an agent and receives, processes, and replies to received GetRequest, GetNextRequest, GetBulkRequest, and SetRequest PDUs. SNMP Applications Notification originator: The notification originator application in an agent generates Trap PDUs; these PDUs are eventually received and processed in a notification receiver application at a managing entity. Proxy forwarder: The proxy forwarder application forwards request, notification, and response PDUs. SNMP Vulnerability and Security WHAT ARE THE THREATS? Modification of Information The modification threat is the danger that some unauthorized entity may alter in-transit SNMP messages generated on behalf of an authorized principal in such a way as to effect unauthorized management operations, including falsifying the value of an object. WHAT ARE THE THREATS? (contd.) Masquerade The masquerade threat is the danger that management operations not authorized for some user may be attempted by assuming the identity of another user that has the appropriate authorizations. WHAT ARE THE THREATS? (contd.) Disclosure The disclosure threat is the danger of eavesdropping on the exchanges between managed agents and a management station. Protecting against this threat may be required as a matter of local policy. WHAT ARE THE THREATS? (contd.) Message Stream Modification The SNMP protocol is typically based upon a connection-less transport service which may operate over any sub-network service. The re-ordering, delay or replay of messages can and does occur through the natural operation of many such sub-network services. The message stream modification threat is the danger that messages may altered, in order to effect unauthorized management operations. WHAT IS NOT A THREAT? Denial of Service The current SNMP security model does not attempt to address the broad range of attacks by which service on behalf of authorized users is denied. Indeed, such denial-of-service attacks are in many cases in distinguishable from the type of network failures with which any viable network management protocol must cope up with. WHAT IS NOT A THREAT? (contd.) Traffic Analysis The current SNMP security model does not attempt to address traffic analysis attacks. Indeed, many traffic patterns are predictable – devices may be managed on a regular basis by a relatively small number of management applications – and therefore there is no significant advantage afforded by protecting against traffic analysis. GOALS AND CONSTRAINTS Based on the foregoing account of threats in the SNMP network management environment, the goals of a SNMP security model are as follows: Provide for verification that each received SNMP message has not been modified during its transmission through the network. Provide for verification of the identity of the user on whose behalf a received SNMP message claims to have been generated. GOALS AND CONSTRAINTS (contd.) Provide for detection of received SNMP messages, which request or contain management information, whose time of generation was not recent. Provide, when necessary, that the contents of each received SNMP message are protected from disclosure. SECURITY SERVICES Data Integrity is provision of the property that data or data sequences has not been altered or destroyed in an unauthorized manner. Data Origin Authentication is the provision of the property that the claimed identity of the user on whose behalf received data was originated is corroborated. SECURITY SERVICES (contd.) Data Confidentiality is the provision of the property that information is not made available or disclosed to unauthorized individuals, entities, entities, or processes. Message timeliness and limited replay protection is the provision of the property that a message whose generation time is outside of a specified time window is not accepted. VULNERABILITY Following are some of the SNMP vulnerabilities with reference to CERT database. Vulnerability Note VU#4923: The Microsoft SNMP agent, prior to Windows NT 4.0 Service Pack 4.0, will leak memory. An intruder can craft a malicious SNMP packet and consume memory on a victim host. Solution is to upgrade to Windows NT service pack 4 or later. Vulnerability Note VU#173910: A vulnerability exists in multiple Symantec security appliances that could allow a remote attacker to modify the configuration of the device using SNMP. Solution according to the Symantec Advisory is to update the firmware from Symantec enterprise website. VULNERABILITY (contd.) Vulnerability Note VU#835846: Ethereal contains a vulnerability in the way it processes that fails to properly handle malformed SNMP packets. Solution is to either upgrade to version 0.10.5 or later, or to disable SNMP protocol dissector. Vulnerability Note VU#329230: A vulnerability exists in multiple Symantec security appliances that could allow a remote attacker to bypass the firewall using a source port of 53/udp. Solution according to the Symantec Advisory, is to upgrade the product specific firmware and hot fixes are available via the Symantec Enterprise Support site. Review questions 1. 2. 3. 4. What are the five areas of network management and explain them? What is the purpose of SNMP? What are the components in network management architecture and define them? What are the types of messages between SNMP manager and agent?