BrainDumps.CISA_1178.QA Isaca CISA Certified
... A compliance test determines if controls are operating as designed and are being applied in a manner that complies with management policies and procedures. For example, if the IS auditor is concerned whether program library controls are working properly, the IS auditor might select a sample of progr ...
... A compliance test determines if controls are operating as designed and are being applied in a manner that complies with management policies and procedures. For example, if the IS auditor is concerned whether program library controls are working properly, the IS auditor might select a sample of progr ...
Practice Test - GCA Consultants
... A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users of other networks. An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its ...
... A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users of other networks. An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its ...
Technical Reference Model for the Government Procurement
... This Technical Reference Model provides the technical information to implement the principles of the following guidelines recommended in the Guidelines for Optimizing Operation and Systems: [Guideline 4-1] As for the computerization of the whole or a part of job-operations, if such operations are si ...
... This Technical Reference Model provides the technical information to implement the principles of the following guidelines recommended in the Guidelines for Optimizing Operation and Systems: [Guideline 4-1] As for the computerization of the whole or a part of job-operations, if such operations are si ...
What is network management?
... Vulnerability Note VU#4923: The Microsoft SNMP agent, prior to Windows NT 4.0 Service Pack 4.0, will leak memory. An intruder can craft a malicious SNMP packet and consume memory on a victim host. Solution is to upgrade to Windows NT service pack 4 or later. Vulnerability Note VU#173910: A vulnerabi ...
... Vulnerability Note VU#4923: The Microsoft SNMP agent, prior to Windows NT 4.0 Service Pack 4.0, will leak memory. An intruder can craft a malicious SNMP packet and consume memory on a victim host. Solution is to upgrade to Windows NT service pack 4 or later. Vulnerability Note VU#173910: A vulnerabi ...
Chapter 02: The Need for Security
... propagate and attack. The code attaches itself to the existing program and takes control of that program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program tha ...
... propagate and attack. The code attaches itself to the existing program and takes control of that program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program tha ...
International Technical Support Organization Enterprise
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1995. All rights reserved. Note to U.S. Government Users — Do ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1995. All rights reserved. Note to U.S. Government Users — Do ...
PPT - Communications
... • SNMPv1 uses plain text community strings for authentication as plain text without encryption • SNMPv2 was supposed to fix security problems, but effort derailed (The “c” in SNMPv2c stands for “community”). ...
... • SNMPv1 uses plain text community strings for authentication as plain text without encryption • SNMPv2 was supposed to fix security problems, but effort derailed (The “c” in SNMPv2c stands for “community”). ...
A Reference Security Management Plan for Energy
... This Reference Security Management Plan is written in the form of a guidebook and has a single goal: To provide a practical methodology to help an owner/operator of an energy infrastructure Asset create and embed a robust and appropriate security framework around an Asset that can be adapted and upd ...
... This Reference Security Management Plan is written in the form of a guidebook and has a single goal: To provide a practical methodology to help an owner/operator of an energy infrastructure Asset create and embed a robust and appropriate security framework around an Asset that can be adapted and upd ...
Building a Secure Computer System
... impediment to the growth of the field. Removing this obstacle required an author thoroughly conversant with the technology, skilled in writing, and fully dedicated to completion of a most difficult undertaking. Mr. Gasser has accepted this formidable challenge and has succeeded beyond what even we o ...
... impediment to the growth of the field. Removing this obstacle required an author thoroughly conversant with the technology, skilled in writing, and fully dedicated to completion of a most difficult undertaking. Mr. Gasser has accepted this formidable challenge and has succeeded beyond what even we o ...
Easy Steps to Cisco Extended Access List
... before implementing it. Monitor the CPU and Memory usage of the router before and after applying the access list. After applying the access list on the router, recommend reviewing the access list you just applied by doing a “show access-list”. Before denying a recommended port block, monitor the por ...
... before implementing it. Monitor the CPU and Memory usage of the router before and after applying the access list. After applying the access list on the router, recommend reviewing the access list you just applied by doing a “show access-list”. Before denying a recommended port block, monitor the por ...
Unraveling the B2B Process
... Since the events of 9/11, the computer security requirements for DOD facilities has intensified and has had an impact on laboratories and their networked instrumentation/devices. The Business to Business Gateway is how laboratories obtain remote connectivity with commercial vendors. TIMPO, DISA, MTF ...
... Since the events of 9/11, the computer security requirements for DOD facilities has intensified and has had an impact on laboratories and their networked instrumentation/devices. The Business to Business Gateway is how laboratories obtain remote connectivity with commercial vendors. TIMPO, DISA, MTF ...
SNMP Simple Network Management Protocol - CS-UCY
... Get-request. Requests the values of one or more objects Get-next-request. Requests the value of the next object, according to a lexicographical ordering of OIDs. Set-request. A request to modify the value of one or more ...
... Get-request. Requests the values of one or more objects Get-next-request. Requests the value of the next object, according to a lexicographical ordering of OIDs. Set-request. A request to modify the value of one or more ...
Global Information Grid (GIG)
... and computing systems and services, software (including applications), data, security services, and other associated services necessary to achieve Information Superiority. It also includes National Security Systems (NSS) as defined in section 5142 of the Clinger-Cohen Act of 1996. The GIG supports a ...
... and computing systems and services, software (including applications), data, security services, and other associated services necessary to achieve Information Superiority. It also includes National Security Systems (NSS) as defined in section 5142 of the Clinger-Cohen Act of 1996. The GIG supports a ...
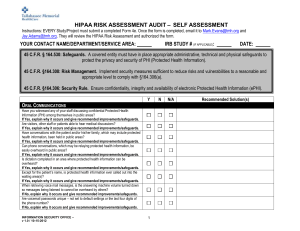
Form 4e HIPAA Risk Assessment Survey
... 45 C.F.R. § 164.530: Safeguards. A covered entity must have in place appropriate administrative, technical and physical safeguards to protect the privacy and security of PHI (Protected Health Information). 45 C.F.R. §164.308: Risk Management. Implement security measures sufficient to reduce risks an ...
... 45 C.F.R. § 164.530: Safeguards. A covered entity must have in place appropriate administrative, technical and physical safeguards to protect the privacy and security of PHI (Protected Health Information). 45 C.F.R. §164.308: Risk Management. Implement security measures sufficient to reduce risks an ...
About the Presentations
... – Authorization: determining which actions that entity can perform in that physical or logical area – Accountability: documenting the activities of the authorized individual and systems ...
... – Authorization: determining which actions that entity can perform in that physical or logical area – Accountability: documenting the activities of the authorized individual and systems ...
8_The_Basics_of_Information_Security
... operating system and the steps that we take to do so. We also review the additional security-related software that we might use to secure our systems including anti-malware tools, software firewalls, and host-based intrusion detection systems in order to protect us from a variety of attacks. Lastly, ...
... operating system and the steps that we take to do so. We also review the additional security-related software that we might use to secure our systems including anti-malware tools, software firewalls, and host-based intrusion detection systems in order to protect us from a variety of attacks. Lastly, ...
Datasäkerhet/Data security EDA625 – Lect2 CRYPTOGRAPHY
... length Input x of arbitrary length is broken up into blocks x = x1 x2 ...xm where padding is applied to the last block h0 fixed value. Recursive applications of h by ...
... length Input x of arbitrary length is broken up into blocks x = x1 x2 ...xm where padding is applied to the last block h0 fixed value. Recursive applications of h by ...
Document
... Logs are usually in proprietary format and difficult to manage Routine log reviews and analysis are beneficial for identifying security incidents, policy violations, fraudulent activity, and operational problems Logs can also be useful for performing auditing and forensic analysis, supporting the or ...
... Logs are usually in proprietary format and difficult to manage Routine log reviews and analysis are beneficial for identifying security incidents, policy violations, fraudulent activity, and operational problems Logs can also be useful for performing auditing and forensic analysis, supporting the or ...
Lecture17 - The University of Texas at Dallas
... applications. The organization will run the vendor-provided applications on the vendor infrastructure and software. For the IaaS model, the applications are controlled by the organization while the services are controlled by both the organization and the vendor. This is because to host the organizat ...
... applications. The organization will run the vendor-provided applications on the vendor infrastructure and software. For the IaaS model, the applications are controlled by the organization while the services are controlled by both the organization and the vendor. This is because to host the organizat ...
File - Information Technology Security
... ____ 34. A flaw or weakness that allows a threat agent to bypass security ____ 35. The likelihood that the threat agent will exploit the vulnerability ____ 36. A subject’s access level over an object, such as a user’s ability to open a payroll file ____ 37. The process of assigning and revoking priv ...
... ____ 34. A flaw or weakness that allows a threat agent to bypass security ____ 35. The likelihood that the threat agent will exploit the vulnerability ____ 36. A subject’s access level over an object, such as a user’s ability to open a payroll file ____ 37. The process of assigning and revoking priv ...
Password Security
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
PDF - IBM Redbooks
... media sites were used to both obtain information about users and as an initial access point into organizations. Attacks against mobile devices increased dramatically, in particular against mobile devices running the Android operating system. Although fixes were released to fix these mobile vulnerabi ...
... media sites were used to both obtain information about users and as an initial access point into organizations. Attacks against mobile devices increased dramatically, in particular against mobile devices running the Android operating system. Although fixes were released to fix these mobile vulnerabi ...
Example: Data Mining for the NBA
... applications. The organization will run the vendor-provided applications on the vendor infrastructure and software. For the IaaS model, the applications are controlled by the organization while the services are controlled by both the organization and the vendor. This is because to host the organizat ...
... applications. The organization will run the vendor-provided applications on the vendor infrastructure and software. For the IaaS model, the applications are controlled by the organization while the services are controlled by both the organization and the vendor. This is because to host the organizat ...