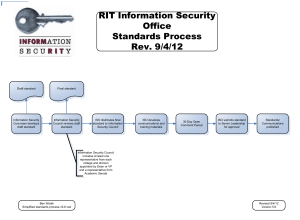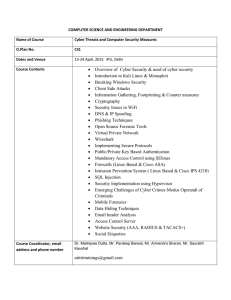
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
Preface
... Caesar saw the need to encrypt messages by means of cryptographic tools. Even before then, people tried to hide their messages by making them "invisible". These hiding techniques, in an interesting twist of history, have resurfaced quite recently in the context of digital rights management. To contr ...
... Caesar saw the need to encrypt messages by means of cryptographic tools. Even before then, people tried to hide their messages by making them "invisible". These hiding techniques, in an interesting twist of history, have resurfaced quite recently in the context of digital rights management. To contr ...
JRA1.4 AAs in eduGAIN
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
Introduction - Personal Web Pages
... • What can go wrong – Trojan war story (Trojan horse): USB keys (Digital photo frame and SCADA) – Corrupted internal worker – Vulnerabilities of protocols or security mechanisms (security patch has problems) – By-passing protection walls – Backdoors for systems (Linux password) – Known attacks ignor ...
... • What can go wrong – Trojan war story (Trojan horse): USB keys (Digital photo frame and SCADA) – Corrupted internal worker – Vulnerabilities of protocols or security mechanisms (security patch has problems) – By-passing protection walls – Backdoors for systems (Linux password) – Known attacks ignor ...
PPT - Cyber Seminar
... Information Rights Management • Growing outsourced relationships • Need to look beyond NDA ...
... Information Rights Management • Growing outsourced relationships • Need to look beyond NDA ...
Honeynet Project
... threats and vulnerabilities that exist in the Internet”. Research Alliance. Security research and raising awareness through the status reports. ...
... threats and vulnerabilities that exist in the Internet”. Research Alliance. Security research and raising awareness through the status reports. ...
Joshua W. Michalik
... INFORMATION SYSTEMS PROJECTS: • ELIZA web application INFORMATION TECHNOLOGY SKILLS: • Microsoft Office • Data Visualization and Analysis • MySQL, HTML, CSS, PHP, Python, RStudio EXPERIENCE: ...
... INFORMATION SYSTEMS PROJECTS: • ELIZA web application INFORMATION TECHNOLOGY SKILLS: • Microsoft Office • Data Visualization and Analysis • MySQL, HTML, CSS, PHP, Python, RStudio EXPERIENCE: ...
Federal Bio
... Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line specialties included performing risk assessments and creating risk mitigation strategies for ...
... Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line specialties included performing risk assessments and creating risk mitigation strategies for ...
Malicious Cryptography : Exposing Cryptovirology
... be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” by a piece of software planted surreptitiously on their computer while browsing t ...
... be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” by a piece of software planted surreptitiously on their computer while browsing t ...
Verbal Attestation of Standard form SF
... Intending TO be legally bound, I hereby accept the obligations contained in this Agreement in consideration of my being granted access to classified information. AS used in this Agreement, classified information is marked or unmarked classified information, including oral communications, that is cla ...
... Intending TO be legally bound, I hereby accept the obligations contained in this Agreement in consideration of my being granted access to classified information. AS used in this Agreement, classified information is marked or unmarked classified information, including oral communications, that is cla ...
Systems Development Brochure
... increase organizational effectiveness. Build strategic information systems using the latest technologies. ...
... increase organizational effectiveness. Build strategic information systems using the latest technologies. ...