Cisco Product Quick Reference Guide
... Designed for our Cisco field and partners, this guide will help you determine which Cisco product, service, or solution is right for your customer. It is also ideal for end users, networking professionals, Cisco Networking Academy members, and those studying for Cisco certification needing a broad, ...
... Designed for our Cisco field and partners, this guide will help you determine which Cisco product, service, or solution is right for your customer. It is also ideal for end users, networking professionals, Cisco Networking Academy members, and those studying for Cisco certification needing a broad, ...
Cisco Router Guide
... management, and advanced Quality of Service (QoS) for today’s most demanding network services, including IP communications, video, customer relationship management, financial transactions, and other real-time applications. This guide shows how Cisco Services Aggregation Routers and Cisco Integrated ...
... management, and advanced Quality of Service (QoS) for today’s most demanding network services, including IP communications, video, customer relationship management, financial transactions, and other real-time applications. This guide shows how Cisco Services Aggregation Routers and Cisco Integrated ...
5.4.1 Using IPsec to Secure Autoconfiguration
... information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series re ...
... information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series re ...
Guía de Soluciones: Seguridad
... ■ Todos los empleados deben mantenerse al día Control) permite a las redes detectar los sistemas y comprender sus responsabilidades. vulnerables y fijar controles eficaces de acceso a ■ Hay todo un catálogo Cisco de herramientas de la red, admitiendo solamente dispositivos fiables gestión de segurid ...
... ■ Todos los empleados deben mantenerse al día Control) permite a las redes detectar los sistemas y comprender sus responsabilidades. vulnerables y fijar controles eficaces de acceso a ■ Hay todo un catálogo Cisco de herramientas de la red, admitiendo solamente dispositivos fiables gestión de segurid ...
BrainDumps.CISA_1178.QA Isaca CISA Certified
... A call-back system in a net centric environment would mean that a user with an id and password calls a remote server through a dial-up line first, and then the server disconnects and dials back to the user machine based on the user id and password using a telephone number from its database. Although ...
... A call-back system in a net centric environment would mean that a user with an id and password calls a remote server through a dial-up line first, and then the server disconnects and dials back to the user machine based on the user id and password using a telephone number from its database. Although ...
Cisco Security Competitive Reference Guide
... In the past, many businesses thought they had to make a choice when it came to security: they could use best-in-class products that were effective against specific types of emerging threats but did not fully integrate into a pervasive defense system, or they could take a systems approach that assimi ...
... In the past, many businesses thought they had to make a choice when it came to security: they could use best-in-class products that were effective against specific types of emerging threats but did not fully integrate into a pervasive defense system, or they could take a systems approach that assimi ...
SonicOS Standard 3.1 Administrator`s Guide
... Chapter 2: Basic SonicWALL Security Appliance Setup . . . . . . . . . . . . . . . . .9 Collecting Required ISP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Internet Service Provider (ISP) Information . . . . . . . . . . . . . . . . . . . . . . . ...
... Chapter 2: Basic SonicWALL Security Appliance Setup . . . . . . . . . . . . . . . . .9 Collecting Required ISP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Internet Service Provider (ISP) Information . . . . . . . . . . . . . . . . . . . . . . . ...
Paper Title (use style: paper title)
... construct the multicast delivery tree should be optimized and well scheduled. In fact, multicast routers cannot trigger automatically a unidirectional or a bidirectional multicast routing protocol unless they are manually configured to use a specific routing protocol for a predetermined pool of IP ...
... construct the multicast delivery tree should be optimized and well scheduled. In fact, multicast routers cannot trigger automatically a unidirectional or a bidirectional multicast routing protocol unless they are manually configured to use a specific routing protocol for a predetermined pool of IP ...
Cisco TrustSec�5.0 - Systemmerkblatt
... Cisco Industrial Ethernet switch families, delivering policy-enforcement capabilities to field locations for energy providers and utilities. ...
... Cisco Industrial Ethernet switch families, delivering policy-enforcement capabilities to field locations for energy providers and utilities. ...
Symantec™ Security Gateways Reference Guide
... Advanced features, such as the Symantec Alerting Service and Technical Account Manager role, offer enhanced response and proactive security support Please visit our Web site for current information on Support Programs. The specific features available may vary based on the level of support purchased ...
... Advanced features, such as the Symantec Alerting Service and Technical Account Manager role, offer enhanced response and proactive security support Please visit our Web site for current information on Support Programs. The specific features available may vary based on the level of support purchased ...
Palo Alto Networks Administrator’s Guide Release 5.0
... Palo Alto Networks, Inc. www.paloaltonetworks.com © 2007-2013 Palo Alto Networks. All rights reserved. Palo Alto Networks, PAN-OS, and Panorama are trademarks of Palo Alto Networks, Inc. All other trademarks are the property of their respective owners. P/N 810-000107-00D ...
... Palo Alto Networks, Inc. www.paloaltonetworks.com © 2007-2013 Palo Alto Networks. All rights reserved. Palo Alto Networks, PAN-OS, and Panorama are trademarks of Palo Alto Networks, Inc. All other trademarks are the property of their respective owners. P/N 810-000107-00D ...
CICS TS for z/OS 4.2: RACF Security Guide
... This edition applies to Version 4 Release 2 of CICS Transaction Server for z/OS (product number 5655-S97) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1989, 2014. US Government Users Restricted Rights – Use, duplication or di ...
... This edition applies to Version 4 Release 2 of CICS Transaction Server for z/OS (product number 5655-S97) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1989, 2014. US Government Users Restricted Rights – Use, duplication or di ...
Comparative firewall study - Torsten Hoefler - Qucosa
... to the Internet over an access point. These kind of nodes are called router or gateway. The disadvantage of this transition is the possible misuse or malicious utilisation from the internal network or the Internet. Attackers are able to access services offered by the company or lead offences from co ...
... to the Internet over an access point. These kind of nodes are called router or gateway. The disadvantage of this transition is the possible misuse or malicious utilisation from the internal network or the Internet. Attackers are able to access services offered by the company or lead offences from co ...
Hack Attacks Revealed
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
Hack Attacks Revealed
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
... sabotage careers, and just to make trouble. Together, the Internet and the World Wide Web have opened a new backdoor through which a remote attacker can invade home computers or company networks and electronically snoop through the data therein. According to my experiences, approximately 85 percent ...
IPv6 Advantages March 2000
... Limits Internet growth for existing users Hinders use of the Internet for new users Internet Routing today is inefficient Forces users to use NAT ...
... Limits Internet growth for existing users Hinders use of the Internet for new users Internet Routing today is inefficient Forces users to use NAT ...
Model FVL328 ProSafe High-Speed VPN Firewall Reference
... This equipment is in the second category (information equipment to be used in a residential area or an adjacent area thereto), and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing Equipment and Electronic Office Machines, aimed at preventing radio in ...
... This equipment is in the second category (information equipment to be used in a residential area or an adjacent area thereto), and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing Equipment and Electronic Office Machines, aimed at preventing radio in ...
TRITON - Web Security Help, v7.7
... Websense is a registered trademark and TRITON is a trademark of Websense, Inc., in the United States and certain international markets. Websense has numerous other unregistered trademarks in the United States and internationally. All other trademarks are the property of ...
... Websense is a registered trademark and TRITON is a trademark of Websense, Inc., in the United States and certain international markets. Websense has numerous other unregistered trademarks in the United States and internationally. All other trademarks are the property of ...
Core of the network
... • Implementations of IPv6 are very immature now – Lack of VRRP (v3 standardized 1 year ago) – DHCPv6 failover is neither standardized nor implemented yet – Issues on VPN • Most of vendors supports only IPv4 over VPN • What happened when user connected via VPN tries to reach some services available o ...
... • Implementations of IPv6 are very immature now – Lack of VRRP (v3 standardized 1 year ago) – DHCPv6 failover is neither standardized nor implemented yet – Issues on VPN • Most of vendors supports only IPv4 over VPN • What happened when user connected via VPN tries to reach some services available o ...
N150 Wireless ADSL2+ Modem Router DGN1000 User
... way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets you block unsafe Internet content and applications, and protects the devices (PCs, ga ...
... way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets you block unsafe Internet content and applications, and protects the devices (PCs, ga ...
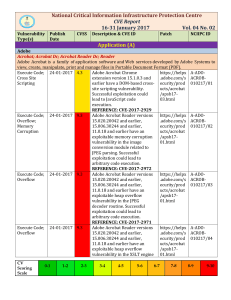
16-31 Jan`17 - National Critical Information Infrastructure Protection
... REFERENCE: CVE-2017-3798 Webex Meeting Center; Webex Meetings Server Cisco WebEx, formerly WebEx Communications Inc. is a company that provides on-demand collaboration, online meeting, web conferencing and videoconferencing applications. NA ...
... REFERENCE: CVE-2017-3798 Webex Meeting Center; Webex Meetings Server Cisco WebEx, formerly WebEx Communications Inc. is a company that provides on-demand collaboration, online meeting, web conferencing and videoconferencing applications. NA ...
N150 Wireless ADSL2+ Modem Router DGN1000 User Manual 350 East Plumeria Drive
... way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets you block unsafe Internet content and applications, and protects the devices (PCs, ga ...
... way to set up a wireless home network with fast access to the Internet over a high-speed digital subscriber line (DSL). It has a built-in DSL modem, is compatible with all major DSL Internet service providers, lets you block unsafe Internet content and applications, and protects the devices (PCs, ga ...
Web Security Help for Websense TRITON Web Security Solutions
... ©1996–2014, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA Published 2014 Printed in the United States and Ireland The products and/or methods of use described in this document are covered by U.S. Patent Numbers 5,983,270; 6,606,659; 6,947,985; 7,185,015; 7,1 ...
... ©1996–2014, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA Published 2014 Printed in the United States and Ireland The products and/or methods of use described in this document are covered by U.S. Patent Numbers 5,983,270; 6,606,659; 6,947,985; 7,185,015; 7,1 ...