* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Core of the network
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
TV Everywhere wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Wireless security wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
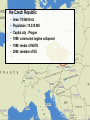
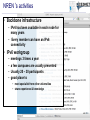
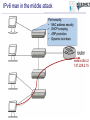
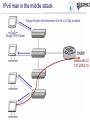
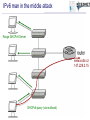
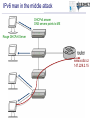
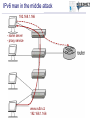
Tomáš Podermański, [email protected] • the Czech Republic – – – – – – Area: 78 866 Km2 Population: 10 230 060 Capital city : Prague 1989: communist regime collapsed 1999: meber of NATO 2004: member of EU Brno NREN – CESNET z.s.p.o. – 26 members – Universities & Czech academy – Many other institutions connected indirectly – Government institutions, hospitals, high schools, research institutions – Network based on DWDM & MPLS technology Rumors about IPv6 • Do you know that IPv4 address space will be exhausted very soon ? – Really, again? I already heard about it 10 years ago. • We are working on IPv6 transition ! – Do you still use it? • How do you get on with IPv6 ? – Everything is ready. The network is well prepared and all applications support dual stack. There is no problem with IPv6. • Very well, can I see how it works? – Ehh, em, you know…. maybe later • Actual point of view – We know that IPv6 is a real problem, but we don’t have time and money to deal with it. – We’d like to cope with IPv6, but we don’t know how. Why IPv6 ? Top 10 Features that make IPv6 'greater' than IPv4 1. Larger IP address space 2. Better end-to-end connectivity 3. Ability for autoconfiguring devices 4. Simplified header structures 5. Better security (IPSEC – ESP, AH) 6. Better quality of services 7. Better multicast and anycast abilities 8. Mobility features 9. Ease of administration 10.Smooth transition from IPv4 source: http://ipv6.com/ Why IPv6 ? Top 10 Features that make IPv6 'greater' than IPv4 1. Larger IP address space 2. Better end-to-end connectivity 3. Ability for autoconfiguring devices 4. Simplified header structures 5. Better security (IPSEC – ESP, AH) 6. Better quality of services 7. Better multicast and anycast abilities 8. Mobility features 9. Ease of administration 10.Smooth transition from IPv4 source: http://ipv6.com/ Ten years ago we had a plan … IPv4 Pool Size IPv6 Deployment Size of the Internet IPv6 Transition using Dual Stack 6 - 10 years Time Source: http://www.potaroo.net/presentations/ What’s the revised plan? IPv4 Pool Size 100 % Size of the Internet ? Today 1% IPv6 Transition IPv6 Deployment 1 year Time Source: http://www.potaroo.net/presentations/ An Internet Transition Plan • Recommendation based on RFC5211 (07/2008) • Phase I (2008 – 2009) – Backbone network, basic infrastructure – Native connectivity to each location (low speed) – Some public services available on IPv6 (web, ftp) • Phase II (2010/1 - 2011/12) – – – – – Stable backbone infrastructure Hardware routing Monitoring of applications & hotline support IPv6 connectivity for end users in selected locations IPv6 multicast in testing mode • Phase III (2012/1) – IPv6 network in good working order (unicast & multicast) – Native IPv6 connectivity for all users – majority of services available through IPv6 IANA: Allocation of /8 IPv4 prefixes 2008: Google on IPv6 2008: European commision targets 25% IPv6 availability by 2010 NAT 1996: IPv6 pon Linux 2007: Win Vista, SP1 dulastack Prefered IPv6 1998: RFC 2460 1992: The first call Source: http://www.potaroo.net/tools/ipv4/index.html 2001: Win XP, SP1 dulastack Action plans of deployment IPv6 • EU : ADVANCING THE INTERNET – Action Plan for the deployment of Internet Protocol version 6 (IPv6) in Europe,Brussels, 27.5.2008, COM(2008) 313 final • USA: Transition Planning for Internet Protocol Version 6 (IPv6), to set the US Federal Agencies a hard deadline for compliance to IPv6 on their core IP networks • China : China Next Generation Internet (CNGI) sets out a 5 year plan (2006-2010) for the early adoption of IPv6 • Korea: IPv6 Promotion Plan II which sets a vision of deploying IPv6 for the public sector by 2010 • Australia: Preparation Jan 2008-Dec 2009, Transition Jan 2010-Dec 2012, Implementation Jan 2013-Dec 2015 Google: users with IPv6 connectivity Source: http://www.google.com/intl/en/ipv6/statistics/ IPv6 deployment ratio – 12/2010 Source: http://bgpmon.net/blog/?p=340 NREN‘s activities • Backbone infrastructure – IPv6 has been available in each node for many years – Every member can have an IPv6 connectivity • IPv6 workgroup – – – – meetings 3 times a year a few campuses are usually presented Usually 20 – 30 participants good place to • meet specialist from other universities • share experience & knowledge IPv6 and Czech Universities Let’s move on to the campus IPv6 status at the Brno University of Technology the Brno University of Technology • • • • • • • http://www.vutbr.cz One of the largest universities in the Czech Republic Founded in 1899, 110th anniversary was recently celebrated 20,000 students and 2,000 employees 9 faculties 6 other organizational units Dormitory for 6,000 students VUT FP, FEKT, Kolejní 4 VUT Koleje, Kolejní 2 VUT FCH, FEKT, Purkyňova 118 VUT Koleje, Mánesova 12 VUT FEKT, Technická 8 VUT FIT, Božetechova 2 VUT FSI, Technická 2 AV VFU, Palackého 1/3 VUT TI, Technická 4 VUT Koleje, Purk. MU CESNET , Botanická 68a AV ČR UPT MZLU, Tauferova VUT, Kounicova 67a VUT Koleje , Kounicova 46/48 AV ČR UFM VUT Rektorát, Antonínská 1 VUT FAST, Veveří 95 VUT FaVU, Údolní 19 VUT , Gorkého 13 VUT FEKT Údolní 53 VUT FA, Poříčí 5 MU, Vinařská 5 VUT FaVU, Rybářská 13 AV ČR, Rybářská 13 Milestones 1992-1995 Modems, dedicated connections, bandwidth 32 - 128 Kb/s, first fiber was build, Ethernet 10 Mb/s, PC based routers KA9Q a BSD/386. 1995-1998 connections among locations almost transferred to fiber, the ATM 155 Mb/s was being built, PC based routers with BSD Unix. 1998-2001 optical connections with multiple fibers, first attempts to build up circuits on Gigabit Ethernet, L3 switches Extreme Networks. 2002-2004 All-core-network circuits on backbone converted to Gigabit Ethernet. Gigabit Ethernet was used to connect each location. 2005 First experience with 10 Gbp/s Ethernet. Looking for popper technology to build up new backbone. 2006-2008 Step-by-step converting from Gigabit Ehernet to 10 Gigabit Ethernet. Selected technology: Extreme Networks, Hewlett Packard. 2008 For management and L2 cross connections the backuped L2 circuit has been build. Each location had been connected on 10 Gigabit. 2009-now The IPv6 backbone has been built up. All tunnel-like connections have been converted to native. The OSPFv3 based routing has been turned on. IPv6 connectivity is now ready to be used in all locations. Layer 3 network Core of the network • Based on 10Gb/s ethernet • Basic L3 services • OSPF and OSPFv3 • multicast - PIM/SM External connectivity • Two 10Gb/s lines connecting the core to CESNET (BGP, BGP4+) • Basic filtering (SMTP, NetBios, 445/Microsof DS) Locality & sub-campuses • Two 10Gb/s lines to the core • More complex firewalls configurations are dependend on local administrators Initial IPv6 topology IPv6 milestones 2002 Basic tunneled connectivity. Assigned own prefix - 2001:718:802::/48 . 2002-2008 Some experimental services. Possibility to connect locations using IPv6 (VLANs) . Static routing based on FreeBSD PC routers. Native connectivity to NREN 2009 Address plan, prefix divided into organization units. OSPFv3 based routing. PC routers with XORP. 3com 4800 GL devices used as HW routers DNS server moved to the dualstack 2010/I, 2010/II Backuped connectivity to each location Every place/subnet can support native IPv6 connectivity Tests with HP devices (participation on beta testing program) Connectivity to NREN through two 10Gb/s lines – BGP4+ Basic firewall Monitoring of IPv6 services, collecting neighbor caches (NAV) Some services moved to dualstack Participation on HP beta testing program 2010/III, 2010/IV Core of the network moved to the dualstack Ridding off the temporary IPv6 network IPv6 milestones - future • Firmware with full IPv6 support has been released – Temporary solution on xorp routers can be switched off – IPv6 topology will follow the IPv4 topology – All subnets will have both IPv4 and native IPv6 connectivity • PI IPv6 address range has been assigned – Changing address of all subnets and services. We will move from 2001:718:802::/48 to 2001:67c:1220::/46 – Support for renumbering • Activation of services on dualstack – 90% of services could be moved easily (10% of time) – rest of services (90% of time) • very complicated issue • unpredictable problems IPv6 problem no. 1 Autoconfiguration Autoconfiguration • Brand new autoconfiguration mechanisms – Router advertisement (doesn’t contain address of DNS servers) • There is an extension RFC 6016 but is not widely implemented yet – DHCPv6 (doesn’t contain default route option) • There is an draft draft-ietf-mif-dhcpv6-route-option-02 but not accepted yet • Privacy extensions – IPv6 addresses are created by hosts randomly • You have to use both mechanisms in real network – DHCPv6 server, Advertises on router – Secure either of them – Failure any of them leads to a network connectivity failure • Different platforms support different techniques – Windows XP - SLAAC – Windows Vista/7 – SLAAC + DHCPv6 – MAC OS, iOS - SLAAC only (expect Lion – released 06/2011) – Linux, BSD, … – depends on distribution Autoconfiguration IPv4 x IPv6 • IPv4 – DHCP, ARP • IPv6 – DAD, RS/RA, DHCPv6, MLDv2, ND IPv6 problem no. 2 Impact on existing IPv4 infrastructure IPv4 and IPv6 in a network • More than 50% of PC supports dualstack – Most of them use autoconfiguration (SLAAC) to get IP address (MS Vista/7, Linux, Mac OS, iOS, BSD*) – IPv6 is preferred protocol by default • Steps to make an attack: – Setup attacker’s IP to act as a RA sender – Prepare a DHCPv6 server on the attacker's PC; as DNS servers provide attacker’s addresses – Modify the behavior of DNS server to return A or AAAA records for www.google.com, www.yahoo.com, etc. to your attacker’s address – Transparent proxy service allows attacker to modify content of webpages IPv6 man in the middle attack Port security: • MAC address security • DHCP snooping • ARP protection • Dynamic lock down www.vutbr.cz 147.229.2.15 IPv6 man in the middle attack Rouge Router Advertisement with M or O flag enabled Rouge IPv6 Router www.vutbr.cz 147.229.2.15 IPv6 man in the middle attack Rouge DHCPv6 Server www.vutbr.cz 147.229.2.15 DHCPv6 query (via multicast) IPv6 man in the middle attack DHCPv6 answer DNS servers points to ME Rouge DHCPv6 Server www.vutbr.cz 147.229.2.15 IPv6 man in the middle attack 192.168.1.166 - name server - proxy service www.vutbr.cz 192.168.1.166 # ./flood_router6 eth0 IPv6 problem no. 3 First hop security Autoconfiguration – IPv4 • IPv4 autoconfiguration = DHCP • Protection mechanisms on L2 devices – DHCP snooping • Blocking DHCP responses on access ports • Prevents against fake DHCP servers – Dynamic ARP protection • MAC-IP address database based on DHCP leases • Checking content of ARP packets on client access port • Prevents against ARP spoofing – Dynamic lock down • The MAC-IP database is used for inspection of client source MAC and IP address. • Prevents against source address spoofing Possible solutions for IPv6 • SeND (RFC 3971, March 2005) – Based on cryptography CGA keys – Requires PKI infrastructure – Can not work with • Manually configured, EUI 64 and Privacy Extension addresses • RA-Guard (RFC 6105, February 2011) – Dropping fake RA messages on access port (RA Snooping) – Cooperation with SeND (send proxy) – learning mode • SAVI (draft-ietf-savi-*, divided into more drafts) – Complex solution solving • Rouge RA, DHCPv4 an DHCPv6 Possible solutions for IPv6 • No support in devices – Only few vendors support some of that features – You probably will have to replace all access switches • There is a easy way how to bypass such protection – CVE-2011-2395 (http://seclists.org/fulldisclosure/2011/May/446) – Using extension headers – ICMPv6/ND Packet fragmentation IPv6 problem no. 4 Impact on existing IPv4 infrastructure II Impact on existing IPv4 infrastructure • Deploying IPv6 requires changes in the existing infrastructure – Some routers and switches have to be replaced – Some have to be upgraded – There are a lot of bugs in IPv6 code • More often firmware upgrades • New IPv6 related bugs -> CPU overload, Devices crash • IPv6 is another way how to reach nodes inside of the network – Similar policy have to be applied on both protocols • Users (and managers) can see that network is less stable • Both that group can’t see any benefits of that effort IPv6 problem no. 5 IPv6 can’t provide same services as IPv4 does IPv6 can’t provide same services • Implementations of IPv6 are very immature now – Lack of VRRP (v3 standardized 1 year ago) – DHCPv6 failover is neither standardized nor implemented yet – Issues on VPN • Most of vendors supports only IPv4 over VPN • What happened when user connected via VPN tries to reach some services available on both protocols ? – Implementations do not provide equal features • ACL, OSPFv3, BGP4+, policy routing, … – There are a lot of bugs in implementation • Deploying IPv6 means that you will have to help supplier to solve issues. • Nobody else may have not seen some issues before IPv6 problem no. 6 IPv6 requires brand new techniques to manage networks New techniques to manage networks • Privacy extension – Addresses are created randomly, a device has multiple address – Collecting ND cache (NAV - http://metanav.uninett.no/) • Netflow data have to be threaten in differed way – Practical IPv6 Monitoring on Campus (http://www.terena.org/activities/campus-bp/bpd.html) • DHCPv6 uses DUID as host identifier – MAC address can’t be used as host identifier – The host can change DUID - OS reinstallation, dualboot systems • Absence of NAT – There are some scenarios where NAT is very useful – RFC 6296 - IPv6-to-IPv6 Network Prefix Translation • Tunnels – An easy way to bypass security policy IPv6 problem no. 7 Deploying IPv6 does not mean that you can switch off IPv4 Switching off IPv4 is not easy • IPv4 and IPv6 are incompatible protocols – Services available on IPv4 can be reached only by IPv4 – Applications not supporting IPv6 still needs IPv4 • Skype, ICQ, MSN, games, … • NAT64 in not solution for that problem today – It is more realistic keep running dual stack network • It means that you have to run – Two routing protocols including routing policy – Two autoconfiguration mechanism – Two security policy • IPv4 does not have extension headers but IPv6 does • IPv6 uses differed messages in ICMPv6 • IPv6 can use multiple addresses – You have to have well trained staff with very good knowledge of both protocols IPv6 problem no. 8 Administrators gets disappointed and frustrated with developing IPv6 Deploying IPv6 in reality • How things an administrator that has never heard about IPv6 – Is it easier than IPv4 ? • SLAC – security issues, identity problems – Is it the same as IPv4 ? • Static address configuration, link-local address – Is it similar to IPv4 ? • DHCP(v4) + DHCPv6 + RA, … – There are too many differences • There is to many new protocols, new mechanisms, … • I have to learn too many new thinks • Users will not appreciate it A bit of statistics… collected from the campus network IPv4, IPv6 & tunneled traffic Here IPv6 native traffic How many addressed were we talking with Here How IPv6 many addressed were we talking with Come H on, what all this fuss is about. Just take it easy and see what will happen. Number of unique mac adresses in ARP and NC What can we do about it ? • Start using IPv6 immediately – We have been waiting for perfect IPv6 more than 15 years - it does not work – Until IPv6 is used we will not discover any problem • Prefer native IPv6 connectivity (anywhere you can) – It is a final solution for future (IPv4 will be switched off later) – Native IPv6 is more secure than unattended tunneled traffic ! • Ask vendors and creators of standards to fix problems – More requests escalate troubles on the vendor side – Standardization of IPv6 is not enclosed process. Anyone can contribute or comment the standards • Stop pretending that IPv6 does not have any troubles – IPv6 has got many problems – Problems can not be solved by covering them – Unreliable information led to broken trust amongst users. The naked truth is always better than the best dressed lie