Cisco ASA 5500 Series SSL/IPsec VPN Edition
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
... AnyConnect VPN Client, an automatically downloadable network-tunneling client that provides access to virtually any application or resource. Optimized Network Performance: The Cisco AnyConnect VPN Client provides an optimized VPN connection for latencysensitive traffic, such as voice over IP (VoIP) ...
Bitdefender GravityZone Administrator`s Guide
... document is provided on an “as is” basis, without warranty. Although every precaution has been taken in the preparation of this document, the authors will not have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the in ...
... document is provided on an “as is” basis, without warranty. Although every precaution has been taken in the preparation of this document, the authors will not have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the in ...
Secure
... years. Wireless transmission (once the domain of amateur radio enthusiasts and the military) is now a commonplace method of data communication for cellular phones, wireless PDAs, text pagers, and, most important, wireless LANs (WLANs). As there are a number of divergent technologies for wireless net ...
... years. Wireless transmission (once the domain of amateur radio enthusiasts and the military) is now a commonplace method of data communication for cellular phones, wireless PDAs, text pagers, and, most important, wireless LANs (WLANs). As there are a number of divergent technologies for wireless net ...
The Gartner Glossary of Information Technology Acronyms and Terms
... ABAP (Advanced Business Application Programming) The core tool for development in SAP’s R/3 system. ABC (activity-based costing) An improved approach to understanding where and why costs are incurred within an enterprise. It provides the information for activity-based management, which focuses on th ...
... ABAP (Advanced Business Application Programming) The core tool for development in SAP’s R/3 system. ABC (activity-based costing) An improved approach to understanding where and why costs are incurred within an enterprise. It provides the information for activity-based management, which focuses on th ...
NSIS: A New Extensible IP Signaling Protocol Suite
... data path, RSVP-TE follows a label switching path for MPLS networks, which may be determined manually. The RSVP-TE signaling messages then establishes the path later taken by the data traffic. Thus, the concept of path discovery is less relevant. During the work of the NSIS working group, several ke ...
... data path, RSVP-TE follows a label switching path for MPLS networks, which may be determined manually. The RSVP-TE signaling messages then establishes the path later taken by the data traffic. Thus, the concept of path discovery is less relevant. During the work of the NSIS working group, several ke ...
No Slide Title
... Security concerns become especially important for parking EPS While EPS for rail and road tolling operate in the on-line mode (thus making it easier to detect malfunctioning of equipment or breach of security) and EPS equipment on motorbus is monitored by a bus driver (again making it easier to dete ...
... Security concerns become especially important for parking EPS While EPS for rail and road tolling operate in the on-line mode (thus making it easier to detect malfunctioning of equipment or breach of security) and EPS equipment on motorbus is monitored by a bus driver (again making it easier to dete ...
PDF - This Chapter (223.0 KB)
... networking investments. Each quarter, Packet delivers coverage of the latest industry trends, technology breakthroughs, and Cisco products and solutions, as well as network deployment and troubleshooting tips, configuration examples, customer case studies, certification and training information, and ...
... networking investments. Each quarter, Packet delivers coverage of the latest industry trends, technology breakthroughs, and Cisco products and solutions, as well as network deployment and troubleshooting tips, configuration examples, customer case studies, certification and training information, and ...
About the VM-Series Firewall
... PAN-SVC-PREM-VM-100 SKU auth-code), and any additional subscriptions such as Threat Prevention, URL Filtering, GlobalProtect, or WildFire. In the case of the VMware integrated NSX solution, the email contains a single authorization code that bundles the capacity license for one or more instances of ...
... PAN-SVC-PREM-VM-100 SKU auth-code), and any additional subscriptions such as Threat Prevention, URL Filtering, GlobalProtect, or WildFire. In the case of the VMware integrated NSX solution, the email contains a single authorization code that bundles the capacity license for one or more instances of ...
PDF
... priorities. Cisco Configuration Assistant is available for download free of charge at http://www.cisco.com/go/configassist. ...
... priorities. Cisco Configuration Assistant is available for download free of charge at http://www.cisco.com/go/configassist. ...
FiOS Quantum Gateway
... when your Gateway is turned on, connected to the Internet, and functioning normally. The Wireless light will be on when your Gateway Wi-Fi is turned on. For additional information on the front lights and error indications, refer the Troubleshooting section in this Guide. The WPS button is used to in ...
... when your Gateway is turned on, connected to the Internet, and functioning normally. The Wireless light will be on when your Gateway Wi-Fi is turned on. For additional information on the front lights and error indications, refer the Troubleshooting section in this Guide. The WPS button is used to in ...
Clavister Virtual Core
... The Clavister Virtual Core Series is a next-generation firewall, but it also has all the traditional security features, such as stateful firewall with deep-packet inspection, and it is powered by our own in-house developed network security operating system, the Clavister cOS Core. As well as providi ...
... The Clavister Virtual Core Series is a next-generation firewall, but it also has all the traditional security features, such as stateful firewall with deep-packet inspection, and it is powered by our own in-house developed network security operating system, the Clavister cOS Core. As well as providi ...
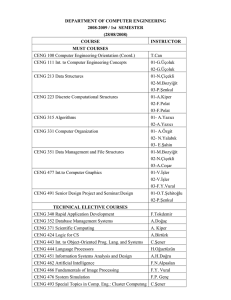
department of computer engineering
... CENG 493 Special Topics in Comp. Eng.: Cluster Computıng C.Şener ...
... CENG 493 Special Topics in Comp. Eng.: Cluster Computıng C.Şener ...
Cisco TrustSec How-To Guide: Segmenting Clients and Servers in
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
... Virtual server - physical server segmentation using SGFW (Figure 2). For this use case, we will deny all network traffic between the engineering server connected to the Cisco Nexus 7000 distribution switch and the virtual servers hosted behind the Cisco Nexus 7000 end-of-row switch. While SGFW is th ...
Top Ten Things About Spam Firewalls
... Barracuda Spam Firewall provides this functionality as part of the standard solution, using two different virus check systems, both of which are updated hourly with new virus definitions via the Barracuda Energize Update service. This ensures that viruses, which often breakout with little to no warn ...
... Barracuda Spam Firewall provides this functionality as part of the standard solution, using two different virus check systems, both of which are updated hourly with new virus definitions via the Barracuda Energize Update service. This ensures that viruses, which often breakout with little to no warn ...
PDF
... Setup wizards: Cisco Configuration Assistant includes an easy-to-use telephony setup wizard that allows users to configure IP addressing functions such as the WAN IP address and the voice and data VLAN IP address. The wizard also adds configuration options for automated attendant, business schedules ...
... Setup wizards: Cisco Configuration Assistant includes an easy-to-use telephony setup wizard that allows users to configure IP addressing functions such as the WAN IP address and the voice and data VLAN IP address. The wizard also adds configuration options for automated attendant, business schedules ...
SonicWALL PRO 5060 Getting Started Guide
... SonicWALL PRO 5060 correctly. 2. If you cannot view the SonicWALL home page, try a second URL. 3. If you still cannot view a Web page, try one of these solutions: Restart your Management Station Your management station may need to restart to accept new network settings from the DHCP server in the So ...
... SonicWALL PRO 5060 correctly. 2. If you cannot view the SonicWALL home page, try a second URL. 3. If you still cannot view a Web page, try one of these solutions: Restart your Management Station Your management station may need to restart to accept new network settings from the DHCP server in the So ...
Security Enhanced (SE) Android: Bringing Flexible
... As a result, none of the prior work to integrate SELinux into Linux userspace could be directly reused for Android. Android also brings unique challenges for integrating SELinux into the userspace due to its model for starting apps. In Android, a single process, the zygote, preloads the Dalvik VM an ...
... As a result, none of the prior work to integrate SELinux into Linux userspace could be directly reused for Android. Android also brings unique challenges for integrating SELinux into the userspace due to its model for starting apps. In Android, a single process, the zygote, preloads the Dalvik VM an ...
the ZoneAlarm User Manual. - Clear Creek Communications
... Tour of the ZoneAlarm control center . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 Tour of main features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 About the Overview panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... Tour of the ZoneAlarm control center . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 Tour of main features. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 About the Overview panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Security Issues in NIS
... password cannot be prevented, that the password must become more complex and thus more difficult to crack using conventional password cracking utilities. NIS aggravates identity attacks on account information because it does not support the two most common methods of increasing this complexity. NIS ...
... password cannot be prevented, that the password must become more complex and thus more difficult to crack using conventional password cracking utilities. NIS aggravates identity attacks on account information because it does not support the two most common methods of increasing this complexity. NIS ...
Review Questions
... Manufactured in the United States of America No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 Unite ...
... Manufactured in the United States of America No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 Unite ...
Personal Area Networking Bluetooth Profile
... The copyright in these specifications is owned by the Promoter Members of Bluetooth SIG Inc. (“Bluetooth SIG”). Use of these specifications and any related intellectual property (collectively, the “Specification”) is governed by the Promoters Membership Agreement among the Promoter Members and Bluet ...
... The copyright in these specifications is owned by the Promoter Members of Bluetooth SIG Inc. (“Bluetooth SIG”). Use of these specifications and any related intellectual property (collectively, the “Specification”) is governed by the Promoters Membership Agreement among the Promoter Members and Bluet ...
Networks and Network Security - Nicolas T. COURTOIS` research in
... Route packets to the wrong server, A number of commercial ISPs use DNS hijacking for their own purposes, such as displaying advertisements… In the UK, the Information Commissioner's Office have acknowledged that this practice contravenes the EC Directives on Data Protection and Privacy and Electroni ...
... Route packets to the wrong server, A number of commercial ISPs use DNS hijacking for their own purposes, such as displaying advertisements… In the UK, the Information Commissioner's Office have acknowledged that this practice contravenes the EC Directives on Data Protection and Privacy and Electroni ...
Solaris 10 - Center for Internet Security
... The Center for Internet Security ("CIS") provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“R ...
... The Center for Internet Security ("CIS") provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“R ...
Using RADIUS Protocol with Check Point Security
... SafeNet makes no representations or warranties with respect to the contents of this document and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. Furthermore, SafeNet reserves the right to revise this publication and to make changes from time to ...
... SafeNet makes no representations or warranties with respect to the contents of this document and specifically disclaims any implied warranties of merchantability or fitness for any particular purpose. Furthermore, SafeNet reserves the right to revise this publication and to make changes from time to ...
BayStack LAN Switching
... Authentication Dial-In User Service (RADIUS) authentication for switch-security management. IP Manager List limits access to the management features of the BayStack 380 by a defined list of IP addresses, providing greater network security and manageability. SNMP v3 feature provides user authenticati ...
... Authentication Dial-In User Service (RADIUS) authentication for switch-security management. IP Manager List limits access to the management features of the BayStack 380 by a defined list of IP addresses, providing greater network security and manageability. SNMP v3 feature provides user authenticati ...