8.1 - Nitish Chandan
... • Estimation of Readiness is not possible as of today; numerous health centres still in the digital disconnect. • Standards for EHRs are available but only to the point that they should be secure. • “Generally, all electronic health information must be encrypted and decrypted as necessary according ...
... • Estimation of Readiness is not possible as of today; numerous health centres still in the digital disconnect. • Standards for EHRs are available but only to the point that they should be secure. • “Generally, all electronic health information must be encrypted and decrypted as necessary according ...
- Longwood Blogs
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
Cybersecurity - Queen`s Wiki
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
... That could never happen to me! Think again. • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in ...
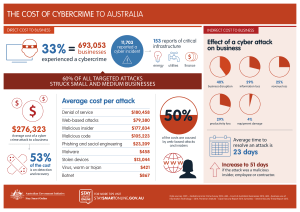
the cost of cybercrime to australia $276323
... THE COST OF CYBERCRIME TO AUSTRALIA DIRECT COST TO BUSINESS ...
... THE COST OF CYBERCRIME TO AUSTRALIA DIRECT COST TO BUSINESS ...
Artificial Intelligence Engineer
... analytics, and applications. Must have a working knowledge of advanced cybersecurity methods, and experience in applying those methods to a variety of applications. Must be flexible, able to move in new directions, and collaborate with our external partners to solve advanced problems. ...
... analytics, and applications. Must have a working knowledge of advanced cybersecurity methods, and experience in applying those methods to a variety of applications. Must be flexible, able to move in new directions, and collaborate with our external partners to solve advanced problems. ...
One Team, One Fight
... Dr. Phyllis Schneck Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
... Dr. Phyllis Schneck Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
new zealand`s cyber security strategy
... Government’s Role • Protecting personal and sensitive governmentheld information and systems • Assisting critical national infrastructure providers • Helping to provide a safe online environment for individuals and businesses ...
... Government’s Role • Protecting personal and sensitive governmentheld information and systems • Assisting critical national infrastructure providers • Helping to provide a safe online environment for individuals and businesses ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber security strategy • Manage CND tools including but not limited to IDS/IPS, IAVM/ACAS, HBSS, Blue Scope, CORE Im ...
... • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber security strategy • Manage CND tools including but not limited to IDS/IPS, IAVM/ACAS, HBSS, Blue Scope, CORE Im ...
Maritime Cyber Vulnerabilities in the Energy Domain
... In 2013, 40% of cyber attacks were directed at energy infrastructure. Challenges to energy industry cyber security can be broken down into 2 major categories. • Protecting the equipment that generates energy • Preventing the attackers to access to system database ...
... In 2013, 40% of cyber attacks were directed at energy infrastructure. Challenges to energy industry cyber security can be broken down into 2 major categories. • Protecting the equipment that generates energy • Preventing the attackers to access to system database ...
• Overview of Cyber Security & need of cyber security • Introduction
... 13-24 April, 2015 IPU, Delhi ...
... 13-24 April, 2015 IPU, Delhi ...