Chapter 1: Security Problems in Computing
... good guys come”. In the arena of physical security, nothing can be absolutely protected. The only answer is to make a successful attack costly and time-consuming. We often apply the same idea to the protection of computer and information assets”. The Great Diamond Heist This is a true story dating f ...
... good guys come”. In the arena of physical security, nothing can be absolutely protected. The only answer is to make a successful attack costly and time-consuming. We often apply the same idea to the protection of computer and information assets”. The Great Diamond Heist This is a true story dating f ...
Security - UTRGV Faculty Web
... Yes it could. Scripts (malicious code) can be placed inside a program. On the other hand, it could be argued, Microsoft can place malicious code to spy on other countries. It is not good business practice to do so. ...
... Yes it could. Scripts (malicious code) can be placed inside a program. On the other hand, it could be argued, Microsoft can place malicious code to spy on other countries. It is not good business practice to do so. ...
Cyber Challenges
... Defense Information Systems Agency: Value: $32.7Mil Provide all aspects of IA operations, management and project implementation: policy/standards; architecture, engineering and integration; fielding/installation and operations; education/training; C&A ...
... Defense Information Systems Agency: Value: $32.7Mil Provide all aspects of IA operations, management and project implementation: policy/standards; architecture, engineering and integration; fielding/installation and operations; education/training; C&A ...
Securing Information Systems
... – Include software controls, physical hardware controls, computer operations controls, data security controls, controls over implementation of system processes, and administrative controls. ...
... – Include software controls, physical hardware controls, computer operations controls, data security controls, controls over implementation of system processes, and administrative controls. ...
NSintroduction
... * Firewall, to block unauthorized access to your network * Intrusion prevention systems (IPS), to detect and block attacks * Virtual Private Networks (VPNs), to provide secure remote access ...
... * Firewall, to block unauthorized access to your network * Intrusion prevention systems (IPS), to detect and block attacks * Virtual Private Networks (VPNs), to provide secure remote access ...
Open ended challenge rationale
... Someone who violates computer security for malicious reasons, status or personal gain ...
... Someone who violates computer security for malicious reasons, status or personal gain ...
faculty profile proforma
... Won an award for Best Project “Remote program compilation, execution and assessment system.” at Aricent Nalanda Training. Won best Employee Award at “Samsung Engineering Labs” in File Systems team. Teaching Experiences (Subject/Courses taught) BSc.(H) CS : Data Mining, Software Testing, UNIX Network ...
... Won an award for Best Project “Remote program compilation, execution and assessment system.” at Aricent Nalanda Training. Won best Employee Award at “Samsung Engineering Labs” in File Systems team. Teaching Experiences (Subject/Courses taught) BSc.(H) CS : Data Mining, Software Testing, UNIX Network ...
Pan-Oston Company, a Houchens Industries Employee Owned
... store fixtures to the retail industry is pleased to announce an immediate opening to join our team in Bowling Green, Kentucky. Computer Operations Specialist Responsibilities Include: ...
... store fixtures to the retail industry is pleased to announce an immediate opening to join our team in Bowling Green, Kentucky. Computer Operations Specialist Responsibilities Include: ...
Cyber ShockWave exposed missing links in US security
... are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving not only our government’s national security and homeland security elements and private enterpris ...
... are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving not only our government’s national security and homeland security elements and private enterpris ...
Information Security and Cryptography
... The Networked Systems Security major subject gives its students profound and substantial education and expertise in the networked systems security and technology field. The graduates of this major subject will benefit from the strong technological, theoretical and practical understanding and skills ...
... The Networked Systems Security major subject gives its students profound and substantial education and expertise in the networked systems security and technology field. The graduates of this major subject will benefit from the strong technological, theoretical and practical understanding and skills ...
IEEE CONFERENCE ON COMMUNICATION TECHNOLOGIES
... Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Security and Software Engineering, MCS is planning to hold an International Conference ...
... Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Security and Software Engineering, MCS is planning to hold an International Conference ...
Future of Cyber Security and the Issue of Cyber warfare: A
... protect networks, computers, programs and data from attack, damage or unauthorized access.In their most disruptive form, cyber threats take aim at secret, political, military, or infrastructural assets of a nation, or its people. Cyber security is therefore a critical part of any governments’ securi ...
... protect networks, computers, programs and data from attack, damage or unauthorized access.In their most disruptive form, cyber threats take aim at secret, political, military, or infrastructural assets of a nation, or its people. Cyber security is therefore a critical part of any governments’ securi ...
Module3 - ITProGuru Blog
... Dan Stolts, Chief Technology Strategist Twitter: @ITProGuru Blog: http://ITProGuru #InnovateIT ...
... Dan Stolts, Chief Technology Strategist Twitter: @ITProGuru Blog: http://ITProGuru #InnovateIT ...
John L. Nunziato, Vice President , SOSSEC, Inc., is involved in
... executing every aspect of business development/operations of the System of Systems Security (SOSSEC) corporation and consortium. SOSSEC is a broad based consortium comprised of a diverse group of 70+ innovative, high-tech traditional and non-traditional contractors, academic institutions and non-pro ...
... executing every aspect of business development/operations of the System of Systems Security (SOSSEC) corporation and consortium. SOSSEC is a broad based consortium comprised of a diverse group of 70+ innovative, high-tech traditional and non-traditional contractors, academic institutions and non-pro ...
Digital Literacy – Computer Basics – Common Computer Terminology
... A group of computers and associated devices that are linked together to facilitate sharing information is called a ___________. The main computer on a network is called a _________. You use a ______________to access the hardware and software on a network. ___________are commonly used as communicatio ...
... A group of computers and associated devices that are linked together to facilitate sharing information is called a ___________. The main computer on a network is called a _________. You use a ______________to access the hardware and software on a network. ___________are commonly used as communicatio ...
Slide 1
... small, a big and vast attack only needs a simple computer and modem. Can be done by individual, does not have to be done by a group of people. The risk is small. It is difficult to locate the suspects, even sometimes does not realize that one is being attacked No time or place limitation, the attack ...
... small, a big and vast attack only needs a simple computer and modem. Can be done by individual, does not have to be done by a group of people. The risk is small. It is difficult to locate the suspects, even sometimes does not realize that one is being attacked No time or place limitation, the attack ...
Junior Enlisted - Cyber Security
... Conducted Continuity of Operations (COOP) procedures to ensure operational capabilities Performed vulnerability assessments, reported findings, and developed Plans of Action and Milestones (POA&Ms) to remediate identified vulnerabilities Initiated documentation for various Department of Defense Info ...
... Conducted Continuity of Operations (COOP) procedures to ensure operational capabilities Performed vulnerability assessments, reported findings, and developed Plans of Action and Milestones (POA&Ms) to remediate identified vulnerabilities Initiated documentation for various Department of Defense Info ...
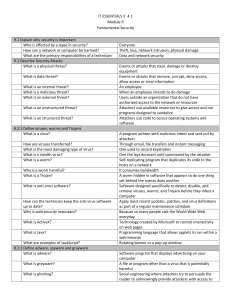
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
ICBA Encourages Consumers to Protect their Data during Cyber
... financial security being compromised,” said ICBA Chairman Jack A. Hartings, president and CEO, The Peoples Bank Co. in Coldwater, Ohio. “Community banks often serve as the first line of defense in ensuring their customers’ financial information is not being used improperly. These banks have establis ...
... financial security being compromised,” said ICBA Chairman Jack A. Hartings, president and CEO, The Peoples Bank Co. in Coldwater, Ohio. “Community banks often serve as the first line of defense in ensuring their customers’ financial information is not being used improperly. These banks have establis ...
Victims who were Hacked PowerPoint Presentation
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
Introduction - Personal Web Pages
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...