Virtual Cyber Security Lab - Celtic-Plus
... Develops ICT software solutions for more than 200 global operators ...
... Develops ICT software solutions for more than 200 global operators ...
PowerPoint 簡報
... know of holes within systems and the reasons for such holes. Hackers constantly seek further knowledge, freely share what they have discovered, and never, ever intentionally damage data. ...
... know of holes within systems and the reasons for such holes. Hackers constantly seek further knowledge, freely share what they have discovered, and never, ever intentionally damage data. ...
IIDPS: An Internal Intrusion Detection and
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
Neal Ziring Very Short Bio
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
Types of Encryption Algorithms
... 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal traffic patterns ...
... 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal traffic patterns ...
JO-Oxford_Preso - International Cyber Center
... Net Present Impact in operational terms • In just six months in 2007: • Requirements for system “cleanings” increased 200 percent • Trojan malware downloads and drops increased 300 percent Characteristic of exploitive attacks since 2004 • “Over the past few years, the focus of endpoint exploitation ...
... Net Present Impact in operational terms • In just six months in 2007: • Requirements for system “cleanings” increased 200 percent • Trojan malware downloads and drops increased 300 percent Characteristic of exploitive attacks since 2004 • “Over the past few years, the focus of endpoint exploitation ...
Principal Security Engineer– PAE4IT A. PRIMARY ROLE Working
... providesreports and recommendations on appropriate tactical and strategic security actions. Have expertise and provide input that could have a direct impact on important technology decisions made at the highest levels of the university 5 Develop and maintain contacts at high levels such as organizat ...
... providesreports and recommendations on appropriate tactical and strategic security actions. Have expertise and provide input that could have a direct impact on important technology decisions made at the highest levels of the university 5 Develop and maintain contacts at high levels such as organizat ...
ch 5 - sm.luth.se
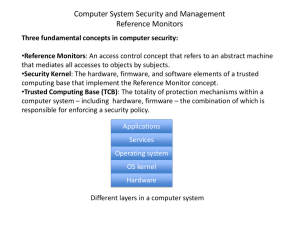
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
Network Security Manager - Harris
... personnel who support network functions and ensure that the network and client computing systems are functioning securely and efficiently to serve the needs of the University’s campus community. The NSM will be responsible for configuring network systems to achieve the institution’s security objecti ...
... personnel who support network functions and ensure that the network and client computing systems are functioning securely and efficiently to serve the needs of the University’s campus community. The NSM will be responsible for configuring network systems to achieve the institution’s security objecti ...
Security Requirements
... (ISPs) in Developing countries are still very much insecure. It took a while for the Tonga ISP (Kalianet) to realize that there was a hole in their security system. Allowing hackers to crack their password system and gain access to the internet free of charge. Entry into the server would give access ...
... (ISPs) in Developing countries are still very much insecure. It took a while for the Tonga ISP (Kalianet) to realize that there was a hole in their security system. Allowing hackers to crack their password system and gain access to the internet free of charge. Entry into the server would give access ...
Security and Ethical Challenges
... – Accessing individuals’ private email conversations and computer records – Collecting and sharing information about individuals gained from their visits to Internet websites ...
... – Accessing individuals’ private email conversations and computer records – Collecting and sharing information about individuals gained from their visits to Internet websites ...
`12
... In this talk, I will summarize our recent research results on quantum and nano photonic devices, including terahertz quantum cascade lasers, terahertz quantum well photodetectors, organic/inorganic hybrid optical upconersion devices, scanning voltage microscopy measurements and nanowire-based nanoge ...
... In this talk, I will summarize our recent research results on quantum and nano photonic devices, including terahertz quantum cascade lasers, terahertz quantum well photodetectors, organic/inorganic hybrid optical upconersion devices, scanning voltage microscopy measurements and nanowire-based nanoge ...
Phoenix SIEM (Security Information and Event
... more than 10 years experience in cyber security software engineering. Some of the notable organizations I have worked for include BAE Systems, Rapid 7 and 3M. At BAE Systems I worked with NetReveal and Vuma, at Rapid 7 I worked with Nexpose and Metasploit, ...
... more than 10 years experience in cyber security software engineering. Some of the notable organizations I have worked for include BAE Systems, Rapid 7 and 3M. At BAE Systems I worked with NetReveal and Vuma, at Rapid 7 I worked with Nexpose and Metasploit, ...
Artificial Intelligence for Cyber Security (AICS)
... that can be used to induce more secure behavior. Another promising approach is to design automated tools that can perform the task of the human in the loop. This approach mitigates security issues arising from sub-optimal security decision taken by humans. Further, automated tools can be formally sp ...
... that can be used to induce more secure behavior. Another promising approach is to design automated tools that can perform the task of the human in the loop. This approach mitigates security issues arising from sub-optimal security decision taken by humans. Further, automated tools can be formally sp ...
Security Risks
... systems by changing, deleting or copying data while others are deliberately intent on defrauding companies. Nowadays a great deal of time, effort and money is spent attempting to make computer networks as secure as possible from unauthorised access. It is particularly important to make sure wireless ...
... systems by changing, deleting or copying data while others are deliberately intent on defrauding companies. Nowadays a great deal of time, effort and money is spent attempting to make computer networks as secure as possible from unauthorised access. It is particularly important to make sure wireless ...
systemsprinciples2
... What is computer security? – Protecting against worms and viruses? – Making sure programs obey their specifications? – Still plenty of security problems even if these problems are solved… ...
... What is computer security? – Protecting against worms and viruses? – Making sure programs obey their specifications? – Still plenty of security problems even if these problems are solved… ...
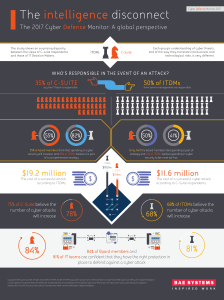
The intelligence disconnect
... Limited registered in England & Wales (No.1337451) with its registered office at Surrey Research Park, Guildford, England, GU2 7RQ. No part of this document may be copied, reproduced, adapted or redistributed in any form or by any means without the express prior written consent of BAE Systems Applie ...
... Limited registered in England & Wales (No.1337451) with its registered office at Surrey Research Park, Guildford, England, GU2 7RQ. No part of this document may be copied, reproduced, adapted or redistributed in any form or by any means without the express prior written consent of BAE Systems Applie ...
CS 494/594 Computer and Network Security - UTK-EECS
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
CS 494/594 Computer and Network Security - UTK-EECS
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
... potential to cause loss or harm A vulnerability is a weakness that may be exploited to cause loss or harm A vulnerability can be exploited to perpetrate an attack ...
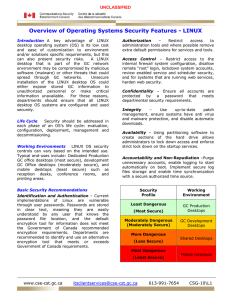
Overview of Operating Systems Security Features
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
... desktop that is part of the GC network environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information ...
Slide 1
... Analyze and address a number of situations in which security in networks can be compromised. Understand and apply selected technologies used to ensure security. Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed ...
... Analyze and address a number of situations in which security in networks can be compromised. Understand and apply selected technologies used to ensure security. Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed ...
Presentation
... Crack- (1) To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaini ...
... Crack- (1) To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaini ...
KESB Advanced Presentation
... USA Today and Washington Post newspaper columnist Steven Petrow has exposed serious flaws in aeroplane wifi On a recent flight, a fellow passenger hacked into his laptop computer and read his emails He learned of the security breach from the hacker after he used Gogo (the biggest on-board WiFi provi ...
... USA Today and Washington Post newspaper columnist Steven Petrow has exposed serious flaws in aeroplane wifi On a recent flight, a fellow passenger hacked into his laptop computer and read his emails He learned of the security breach from the hacker after he used Gogo (the biggest on-board WiFi provi ...
Computersikkerhed
... Denial of Service Distributed Denial of Service Threats in Active or Mobile Code Complex Attacks ...
... Denial of Service Distributed Denial of Service Threats in Active or Mobile Code Complex Attacks ...