Social Studies
... Understand ramifications of posting information, pictures, and videos online. Explain consequences of illegal and unethical use of technology systems and digital content. Identify examples of a computer crime. Know the penalties, fines, incarceration, and laws related to computer crimes. ...
... Understand ramifications of posting information, pictures, and videos online. Explain consequences of illegal and unethical use of technology systems and digital content. Identify examples of a computer crime. Know the penalties, fines, incarceration, and laws related to computer crimes. ...
Network Security Policy
... All networked systems will comply with the Minimum Security Standards policy. The IT Security Office will publish security alerts, vulnerability notices and patches, and other pertinent information in an effort to prevent security breaches. ITS will coordinate investigations into any alleged comput ...
... All networked systems will comply with the Minimum Security Standards policy. The IT Security Office will publish security alerts, vulnerability notices and patches, and other pertinent information in an effort to prevent security breaches. ITS will coordinate investigations into any alleged comput ...
Internet Techniques
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...
... IMS. Cyber threats and cyber defence. Internet based social networking (e.g. Twitter, Youtube). Military networks, cyber warfare. Semantic Web and Web 2.0. SOA. IoS. P2P. Cloud computing. Laboratories exercises are relevant to the issues raised at the lecture. Students learn the practical use of too ...
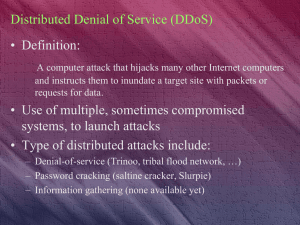
Distributed Denial of Service (DDoS)
... • Check for Trojan horse and zombie code – Network vulnerability scans – Host vulnerability scans – Antivirus ...
... • Check for Trojan horse and zombie code – Network vulnerability scans – Host vulnerability scans – Antivirus ...
module 2 network security unit 1
... employees, contractors and business partners. • Make sure employees know how to secure their home wireless networks. Malicious software that infects their devices at home can infect the company network via an open VPN connection, and • Before granting mobile devices full access to the network, check ...
... employees, contractors and business partners. • Make sure employees know how to secure their home wireless networks. Malicious software that infects their devices at home can infect the company network via an open VPN connection, and • Before granting mobile devices full access to the network, check ...
Technology Chapter 23: Computer and Internet Communication
... Input devices: devices that allow an operator to enter data into a computer’s operating system. Internet: interconnected networks of computers that share information. Internet access: the way a computer is connected to the Internet. Internet protocol address: the identifying number assigned to each ...
... Input devices: devices that allow an operator to enter data into a computer’s operating system. Internet: interconnected networks of computers that share information. Internet access: the way a computer is connected to the Internet. Internet protocol address: the identifying number assigned to each ...
download
... • Computers and networks are the nerves of the basic services and critical infrastructures in our society – Financial services and commerce ...
... • Computers and networks are the nerves of the basic services and critical infrastructures in our society – Financial services and commerce ...
Preface
... management. To control access or usage of digital contents like audio, video or software, information is secretly embedded in the data! Cryptology has developed over the centuries from an art, in which only few were skillful, into a science. Many people regard the “Communication Theory and Secrecy S ...
... management. To control access or usage of digital contents like audio, video or software, information is secretly embedded in the data! Cryptology has developed over the centuries from an art, in which only few were skillful, into a science. Many people regard the “Communication Theory and Secrecy S ...
Lec.4.Communication software and the internet
... communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and maintaining communication across a network is called TCP/IP ...
... communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and maintaining communication across a network is called TCP/IP ...
Blank Jeopardy
... A list of URLs and websites that have been visited in the previous days and weeks ...
... A list of URLs and websites that have been visited in the previous days and weeks ...
Document
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
security_6
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
Fundamentals of Computer Security
... Majority of information security incidents is perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among t ...
... Majority of information security incidents is perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among t ...
Abstract
... becoming increasingly interdisciplinary and reaching across fields such as chemistry, psychology, biology, computer vision, neuroscience, signal processing, and more. In this talk, we show how mathematics, with an emphasis on linear algebra, is used in many industry applications. This includes how t ...
... becoming increasingly interdisciplinary and reaching across fields such as chemistry, psychology, biology, computer vision, neuroscience, signal processing, and more. In this talk, we show how mathematics, with an emphasis on linear algebra, is used in many industry applications. This includes how t ...
Review Questions on Documentary – The Internet Behind the Web
... In telephone network, the main technique for sending signals amongst two telephones is called circuit switching. Then, what is the switching technique for sending data amongst two computers on the network? What did Paul Baran propose in the computer network design? What is the disadvantage of circui ...
... In telephone network, the main technique for sending signals amongst two telephones is called circuit switching. Then, what is the switching technique for sending data amongst two computers on the network? What did Paul Baran propose in the computer network design? What is the disadvantage of circui ...
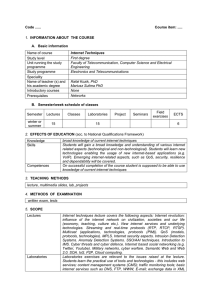
Course name Code/No Units Credit Units Prerequisite Lecture Lab
... To discuss the important of system and network security To explain the relationship between threats, vulnerabilities, countermeasures, attacks, compromises and remediation. To describe of how to manage information security. To explain the encryption technologies. To explain about the privacy and acc ...
... To discuss the important of system and network security To explain the relationship between threats, vulnerabilities, countermeasures, attacks, compromises and remediation. To describe of how to manage information security. To explain the encryption technologies. To explain about the privacy and acc ...
Before You Begin: Assign Information Classification
... looking under keyboards and on desktops. ...
... looking under keyboards and on desktops. ...
security leaflet
... IT security testing for digital office products. Once certified, the devices will have passed a strict security evaluation and be able to satisfy and deliver the kind of security levels that a prudent business operation should look for and rightfully expect. ...
... IT security testing for digital office products. Once certified, the devices will have passed a strict security evaluation and be able to satisfy and deliver the kind of security levels that a prudent business operation should look for and rightfully expect. ...
Westermo Group
... Physical & cyber security is now a key issue The threat of terrorist attacks is real CCTV, intruder and chemical detectors are now part of every system ...
... Physical & cyber security is now a key issue The threat of terrorist attacks is real CCTV, intruder and chemical detectors are now part of every system ...
Security challenges in the lighting use case
... Security challenges in Smart Lighting Paul Chilton NXP Semiconductors ...
... Security challenges in Smart Lighting Paul Chilton NXP Semiconductors ...
Information Security in Real Business
... The outsourcing vendor has the same incentive to secure the data ...
... The outsourcing vendor has the same incentive to secure the data ...
Grossmont-Cuyamaca Community College District
... Analyze and mitigate any possible network and server security vulnerabilities. Monitor for and report on any unusual intrusion activity and react swiftly to prevent or mitigate breaches. Analyze and define security requirements for local and wide area networks. Learn applicable sections of Californi ...
... Analyze and mitigate any possible network and server security vulnerabilities. Monitor for and report on any unusual intrusion activity and react swiftly to prevent or mitigate breaches. Analyze and define security requirements for local and wide area networks. Learn applicable sections of Californi ...
David Cowen, CISSP
... -USAA National Conference - USAA Headquarters, San Antonio, TX -Presentation of the Distributed Password Management Protocol -InfraGard - FBI field office, Dallas, TX -Demonstrated Live Network Penetration to various federal & state law enforcement agencies and security executives representing US cr ...
... -USAA National Conference - USAA Headquarters, San Antonio, TX -Presentation of the Distributed Password Management Protocol -InfraGard - FBI field office, Dallas, TX -Demonstrated Live Network Penetration to various federal & state law enforcement agencies and security executives representing US cr ...