* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Fundamentals of Computer Security
Multilevel security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Airport security wikipedia , lookup
Trusted Computing wikipedia , lookup
Information security wikipedia , lookup
Access control wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Distributed firewall wikipedia , lookup
Mobile security wikipedia , lookup
Unix security wikipedia , lookup
Computer security wikipedia , lookup
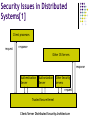
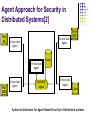
Fundamentals of Computer Security Geetika Sharma Fall 2008 Outline Fundamentals of Computer Security Security Threats and Protection Methods Security Models and Mechanisms Security Issues in Distributed systems Latest Techniques Agent Based Approach Grid Specific Host Based Intrusion Detection System Fundamentals of Computer Security[1] Computer Systems Can be represented by: Subjects Objects Active entities that access objects Passive entities that must be protected Examples: data, hardware, software and communication links Access Control Policy Describes how objects are accessed by subjects Flow Control Policy Regulates the information flow between objects and subjects Security Threats[1] Interruption (availability) Interception Loss of data and denial of service Related to secrecy Modification and Fabrication are violations of system integrity Threats from Web/Network[4] Client Side What can the server do to the client? Fool it Server Side What can the client do to the server? Bring it down (denial of service) Install or run unauthorized software, inspect/alter files Gain access (break-in) Network Is anyone listening? (Sniffing) Is the information genuine? Are the parties genuine? Security Mechanisms[1] Authentication Verification Authorization Extending permission Fault Tolerance Sustaining faults Encryption Prevents exposure of information and maintains privacy Auditing Passive form of protection Security Models[1] Discretionary Provides separation of users and data E.g. access control matrix Mandatory Requires access control of all subjects and orders under its control on a system wide basis E.g. multilevel security, all subjects and objects in the system are assigned a sensitivity label. The labels are used as the basis for mandatory access control decisions. Security Issues in Distributed Systems[1] Interoperability and Transparency Gives rise to security issues Approaches to Implementing New Services Add an additional layer of software that runs on top of the existing system to provide the new services Redesign the system so that the new services can be executed more efficiently in the kernel mode Security Issues in Distributed Systems[1] Client/Server Security A client initiates an access to an object through the kernel Kernel authenticates the client and then invokes the object server Implemented via Interprocess Communication at transport layer Supported by secure host-to-host communications at the network layer and node to node communication at the link layer Secure distributed system consists of communicating security servers using trusted gateway. Security Issues in Distributed Systems[1] Client processes request response Other OS Servers response Authentication Server Authorization Server Other Security Servers request Trusted Secure Kernel Client/Server Distributed Security Architecture Latest Techniques Majority of information security incidents is perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among them are low ability of internal malicious users detection, inability to process large amounts of information, low productivity Agent Approach for Security in Distributed Systems[2] Intelligent Security System for Computers users’ activity monitoring Online and off-line monitoring allowing to detect anomalies and irregularities in user behavior. On-line monitoring is carried in real time, and is used to predict user actions (use neural networks) Off-line monitoring is done after the user has ended his work, and is based on the analysis of statistical information obtained during user's work. Agent Approach for Security in Distributed Systems[2] Win 98 On-line User Agent On-line User Agent Free BSD Dbase Off-line User Agent Win 2000 On-line User Agent Controller Agent On-line User Agent Linux System Architecture for Agent Based Security in Distributed systems GHIDS: Defending Computational Grids Against Misusing of Shared Resources [3] Grid Specific Host Based Intrusion Detection System Design Performance Impact Central Control Leverage Existing Software Configurability Effectiveness Approach/Services Uses Bottleneck Verification (Host) Detects users that go from user to super user improperly Monitors process creation, modification and destruction (Host) Monitors accessing of critical resources (Host) Grid User ID and Host Level ID stores when Grid services used Architecture Host and Grid level deployment Virtual Kernel Device created Grid Middleware modified Data Analyzer User Interface References 1. Randy Chow, Theodore Jognson. Distributed Operating Systems and Algorithms, Addison-Wesley 1997 2. Agent Approach for Providing Security in Distributed Systems; TCSET'2006, February 28-March 4, 2006, Lviv-Slavsko, Ukraine 3. GHIDS:Defending Computational Grids Against Misusing of Shared Resources”, Feng et all, IEEE 2006 4. www.cse.sc.edu/~farkas/csce522-2003/lectures/csce522lect22.ppt (2003) Thanks!