Lab Additions/Suggestions previously done
... Appendix 1-E Linux Firewall exploit Appendix 1-F ZoneAlarm Appendix 1 –G ProcessGuard application to check and control various other applications Appendix 1-H Firewall Builder Appendix 1-I Firehole ...
... Appendix 1-E Linux Firewall exploit Appendix 1-F ZoneAlarm Appendix 1 –G ProcessGuard application to check and control various other applications Appendix 1-H Firewall Builder Appendix 1-I Firehole ...
VPN: Virtual Private Network
... • Lack of standards • Understanding of security issues • Unpredictable Internet traffic • Difficult to accommodate products from different vendors ...
... • Lack of standards • Understanding of security issues • Unpredictable Internet traffic • Difficult to accommodate products from different vendors ...
Microsoft Dynamics AX Implementation Guide
... Preparing to install or upgrade ........................................................................ 27 Recommended methodology and processes ................................................. 28 Implementation methodology .................................................................... 28 Up ...
... Preparing to install or upgrade ........................................................................ 27 Recommended methodology and processes ................................................. 28 Implementation methodology .................................................................... 28 Up ...
About the Presentations
... • Avoid vulnerabilities by ensuring that network’s authorized users – Protect their passwords effectively – Observe some simple security habits ...
... • Avoid vulnerabilities by ensuring that network’s authorized users – Protect their passwords effectively – Observe some simple security habits ...
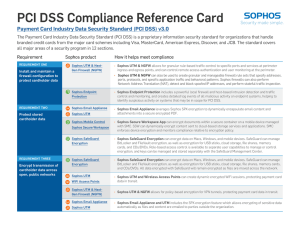
PCI DSS Compliance Reference Card
... ÌÌ Sophos SafeGuard Encryption can encrypt data on Macs, Windows, and mobile devices. SafeGuard can manage BitLocker and FileVault encryption, as well as encryption for USB sticks, cloud storage, file shares, memory cards, and CDs/DVDs. Role-based access control is available to separate user capabil ...
... ÌÌ Sophos SafeGuard Encryption can encrypt data on Macs, Windows, and mobile devices. SafeGuard can manage BitLocker and FileVault encryption, as well as encryption for USB sticks, cloud storage, file shares, memory cards, and CDs/DVDs. Role-based access control is available to separate user capabil ...
Microsoft Windows Operating System Essentials
... No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the pr ...
... No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the pr ...
IIS Security and Programming Countermeasures
... programmable computer is inherently vulnerable because it is controlled by software and is designed to allow new software to be installed or executed arbitrarily. Network computing based on programmable general purpose computers will never be safe from an information security perspective. Eliminatin ...
... programmable computer is inherently vulnerable because it is controlled by software and is designed to allow new software to be installed or executed arbitrarily. Network computing based on programmable general purpose computers will never be safe from an information security perspective. Eliminatin ...
Untitled
... This document supports a preliminary release of a software program that bears the name Microsoft® Windows Vista™. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to c ...
... This document supports a preliminary release of a software program that bears the name Microsoft® Windows Vista™. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to c ...
Era of Spybots - A Secure Design Solution Using
... Figure 2: GIACE Network Design............................................................... 19 Figure 3: GIACE Network Design - Detailed ....................................... 20 GIACE Infrastructure Secure Design.......................................................... 21 ...
... Figure 2: GIACE Network Design............................................................... 19 Figure 3: GIACE Network Design - Detailed ....................................... 20 GIACE Infrastructure Secure Design.......................................................... 21 ...
Junos Pulse Access Control Service
... credentials, and assesses the device’s security state. Junos Pulse leverages and integrates with the native 802.1X supplicant available within Microsoft Windows to deliver comprehensive L2 access control. Junos Pulse Access Control Service can also support native 802.1X supplicants on Apple Mac OS X ...
... credentials, and assesses the device’s security state. Junos Pulse leverages and integrates with the native 802.1X supplicant available within Microsoft Windows to deliver comprehensive L2 access control. Junos Pulse Access Control Service can also support native 802.1X supplicants on Apple Mac OS X ...
conklin_4e_PPT_ch11
... accounting, referred to as AAA. • Authentication is the matching of user-supplied credentials to previously stored credentials on a host machine, and it usually involves an account username and password. • Authorization is the granting of specific permissions based on the privileges held by the acco ...
... accounting, referred to as AAA. • Authentication is the matching of user-supplied credentials to previously stored credentials on a host machine, and it usually involves an account username and password. • Authorization is the granting of specific permissions based on the privileges held by the acco ...
The Real Cost of Free Programs such as Instant
... The current and third generation of file sharing applications still uses a decentralized framework; however, by adding some control to this framework, it essentially becomes a hybrid of the central server and decentralized methods. The latest version of the Gnutella protocol uses this technology, as ...
... The current and third generation of file sharing applications still uses a decentralized framework; however, by adding some control to this framework, it essentially becomes a hybrid of the central server and decentralized methods. The latest version of the Gnutella protocol uses this technology, as ...
VPN
... point connection through the use of dedicated connections, encryption, or a combination of the two VPN technology is also used by ordinary Internet users to connect to proxy servers for the purpose of protecting one's identity ...
... point connection through the use of dedicated connections, encryption, or a combination of the two VPN technology is also used by ordinary Internet users to connect to proxy servers for the purpose of protecting one's identity ...
Remote Access—Attack Vectors
... First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be su ...
... First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be su ...
Application Security
... The attacker modifies the 'CC' parameter in their browser to: '>'. This causes the victim’s session ID to be sent to the attacker’s website, allowing the attacker to hijack the user’s current session. ...
... The attacker modifies the 'CC' parameter in their browser to: '>'. This causes the victim’s session ID to be sent to the attacker’s website, allowing the attacker to hijack the user’s current session. ...
RADIUS Implementation and Deployment Best Practices
... server and the RADIUS server. This implies that the attacker has physical access to the network and is in the routing path between the access server and the RADIUS server. RADIUS Access-Request messages sent by RADIUS clients are not authenticated By default, there is no cryptographic verification o ...
... server and the RADIUS server. This implies that the attacker has physical access to the network and is in the routing path between the access server and the RADIUS server. RADIUS Access-Request messages sent by RADIUS clients are not authenticated By default, there is no cryptographic verification o ...
CH10
... Encryption Solutions (cont’d.) • Asymmetric encryption (public-key encryption) – Encodes messages using two mathematically related numeric keys – Public key: one key freely distributed to public • Encrypt messages using encryption algorithm ...
... Encryption Solutions (cont’d.) • Asymmetric encryption (public-key encryption) – Encodes messages using two mathematically related numeric keys – Public key: one key freely distributed to public • Encrypt messages using encryption algorithm ...
Chapter 10
... • Biometric security devices – Identification using element of person’s biological makeup • Writing pads, eye scanners, palm reading scanners, reading back of hand vein pattern E-Business, Eighth Edition ...
... • Biometric security devices – Identification using element of person’s biological makeup • Writing pads, eye scanners, palm reading scanners, reading back of hand vein pattern E-Business, Eighth Edition ...
Chapter 9 - EECS People Web Server
... rights are granted to entities and groups This policy must include provisions for periodically reviewing all access rights, granting access rights to new employees, changing access rights when job roles change, and revoking access rights as appropriate ...
... rights are granted to entities and groups This policy must include provisions for periodically reviewing all access rights, granting access rights to new employees, changing access rights when job roles change, and revoking access rights as appropriate ...
Certified Penetration Testing Specialist
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
BIND - University of Guelph
... 4. a hash of the process code 5. Authentication tag binds the output data with the code that has generated it. 6. BINDs undoes the protection it has set up for the protection. 7. BINDs returns the authenticator to the process. ...
... 4. a hash of the process code 5. Authentication tag binds the output data with the code that has generated it. 6. BINDs undoes the protection it has set up for the protection. 7. BINDs returns the authenticator to the process. ...
Application Security within Java 2, Standard Edition (J2SE)
... because decisions made by the application developer within the application programming logic affect how the application is secured. An example of programmatic security is a web page which makes decisions on which content to show a user based on the user’ s attributes. For example, an employee logs o ...
... because decisions made by the application developer within the application programming logic affect how the application is secured. An example of programmatic security is a web page which makes decisions on which content to show a user based on the user’ s attributes. For example, an employee logs o ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.