BitLocker - Microsoft
... Assignment of security advisors for all components Threat modeling a part of design phase Required security reviews and testing Security metrics for product teams ...
... Assignment of security advisors for all components Threat modeling a part of design phase Required security reviews and testing Security metrics for product teams ...
Tool: Spector CNE Tool: Track4Win
... • It detects the use of organization resources to engage in illegal or unethical activities. • It limits legal liability (including sexual and racial harassment). • It enforces PC and Internet acceptable-use policies. ...
... • It detects the use of organization resources to engage in illegal or unethical activities. • It limits legal liability (including sexual and racial harassment). • It enforces PC and Internet acceptable-use policies. ...
Here are the PowerPoint slides with links - Auto
... their competitors walked into one of their offices and installed a plugbot (theplugbot.com). The plugbot was able to sniff a domain password and send it over the built-in cellular modem. From there, the attacker established remote access to the corporate data server. A few months later, Widget Corp' ...
... their competitors walked into one of their offices and installed a plugbot (theplugbot.com). The plugbot was able to sniff a domain password and send it over the built-in cellular modem. From there, the attacker established remote access to the corporate data server. A few months later, Widget Corp' ...
An Overview of FileMaker
... database includes more than just data. In addition to tables, you can add: •Saved queries (stored procedures) - organizing and/or manipulating data •Forms – interaction with data, event programming •Reports – customized results for printing forms •Macros and programs for extending functionality Micr ...
... database includes more than just data. In addition to tables, you can add: •Saved queries (stored procedures) - organizing and/or manipulating data •Forms – interaction with data, event programming •Reports – customized results for printing forms •Macros and programs for extending functionality Micr ...
This Article argues that intellectual property law stifles critical
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
EF – One of Microsoft’sORMs - HAAGA
... collection and it is enough to add to one of these, the EF maintains the other automatically. The EF context must know both objects = they must be fetched from same context object or the new created object must be attached to the same EF data context (object) ...
... collection and it is enough to add to one of these, the EF maintains the other automatically. The EF context must know both objects = they must be fetched from same context object or the new created object must be attached to the same EF data context (object) ...
Operating Systems - Personal Web Server
... On -line, Time sharing Personal computing, User progammable Data base, Real time Non-programmable, Multi-user single user, System features ...
... On -line, Time sharing Personal computing, User progammable Data base, Real time Non-programmable, Multi-user single user, System features ...
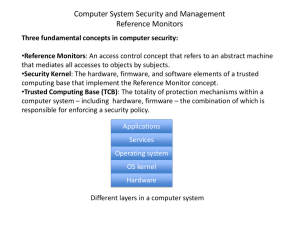
ch 5 - sm.luth.se
... • In the application: In the application code. Operating system integrity The goal of an attacker is to disable the security control by modifying the operating system. When securing an operating system two requirements have to be addressed: • Users should be able to use the operating system. • Users ...
... • In the application: In the application code. Operating system integrity The goal of an attacker is to disable the security control by modifying the operating system. When securing an operating system two requirements have to be addressed: • Users should be able to use the operating system. • Users ...
Differentiate PC, server, and handheld device operating system
... 2.server OS gives centralised administration for users shared resources higher security. But Desktop OS gives local machine administration only. 3.Server OS is fully covered & managed security. For (ex) Domain Controller application server print server etc. We make server with security. for Desktop ...
... 2.server OS gives centralised administration for users shared resources higher security. But Desktop OS gives local machine administration only. 3.Server OS is fully covered & managed security. For (ex) Domain Controller application server print server etc. We make server with security. for Desktop ...
CS15A016
... Rely on data upgrade test iterations to bring data forward to Microsoft Dynamics AX 2012 and test code upgrade ...
... Rely on data upgrade test iterations to bring data forward to Microsoft Dynamics AX 2012 and test code upgrade ...
Hosting Solution for ShowGo Trade Show
... • Triple replicated – Your db is replicated on 3 separate servers. If one fails, we will automatically point it to the second db without you even noticing or having to do anything, then a new 3rd db will be created • Regular maintenance: 24/7 Access • Disaster/Data Recovery, Security, Continually Mo ...
... • Triple replicated – Your db is replicated on 3 separate servers. If one fails, we will automatically point it to the second db without you even noticing or having to do anything, then a new 3rd db will be created • Regular maintenance: 24/7 Access • Disaster/Data Recovery, Security, Continually Mo ...
Network Security
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
... PGP (short for Pretty Good Privacy), created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digit ...
Win32 Programming
... Make sure you have a Gentoo Linux VM and a Windows XP 32-bit VM up and running (unless you want to experiment on live ...
... Make sure you have a Gentoo Linux VM and a Windows XP 32-bit VM up and running (unless you want to experiment on live ...
EnvisionManager System Software System control, monitoring and management
... management and monitoring software tool. It provides users with full visibility of the lighting and energy management system status and performance, while enabling simple local or global system adjustments. ...
... management and monitoring software tool. It provides users with full visibility of the lighting and energy management system status and performance, while enabling simple local or global system adjustments. ...
small business software
... ARTECO-SERVER Small Business is compatible with ONVIF ™ devices and integrates hundreds of cameras from the leading brands on the market. The system can view live/recorded video, as well as analyze video from cameras in full Megapixel resolution. It supports the most advanced encoding: H.264, MJPEG, ...
... ARTECO-SERVER Small Business is compatible with ONVIF ™ devices and integrates hundreds of cameras from the leading brands on the market. The system can view live/recorded video, as well as analyze video from cameras in full Megapixel resolution. It supports the most advanced encoding: H.264, MJPEG, ...
PPT - Cyber Seminar
... Information Rights Management • Growing outsourced relationships • Need to look beyond NDA ...
... Information Rights Management • Growing outsourced relationships • Need to look beyond NDA ...
Looking into Windows
... have been entertained. However, when Microsoft introduced their Windows XP operating system over a decade ago, industry sat up and took notice. Windows XP provided the stability, flexibility and functionality needed by many industrial users and soon appeared in every imaginable type of application. ...
... have been entertained. However, when Microsoft introduced their Windows XP operating system over a decade ago, industry sat up and took notice. Windows XP provided the stability, flexibility and functionality needed by many industrial users and soon appeared in every imaginable type of application. ...
Tobias Herber (530) 723-6691
... - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical servers, patch panel, managed/unmanaged switches, UPS, NAS, and wireless AP's Septe ...
... - Administered Windows 2003-2012, CentOS, and vSphere ESXi servers - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical servers, patch panel, managed/unmanaged switches, UPS, NAS, and wireless AP's Septe ...
Security at the Operating System Level (Microsoft)
... Secure input and output: Guarantee a trusted path from the input devices to a “Trusted Agent” and from a “Trusted Agent” to the output devices. ...
... Secure input and output: Guarantee a trusted path from the input devices to a “Trusted Agent” and from a “Trusted Agent” to the output devices. ...
Powered by SQL Data Platform
... Microsoft BI for the Enterprise Kamal Hathi Director of Program Management Microsoft Server & Tools Division ...
... Microsoft BI for the Enterprise Kamal Hathi Director of Program Management Microsoft Server & Tools Division ...
Security Highlights of Windows 10 - University of Hawai`i
... Antimalware Scan Interface (AMSI): The AMSI is a vendor agnostic interface that allows the operating system to interact with installed antimalware products through a universal mechanism. For example, Powershell, VBSript, and JScript engines now automatically submit script content to AMSI prior to ex ...
... Antimalware Scan Interface (AMSI): The AMSI is a vendor agnostic interface that allows the operating system to interact with installed antimalware products through a universal mechanism. For example, Powershell, VBSript, and JScript engines now automatically submit script content to AMSI prior to ex ...
URL-Encoded Form Data is Not Valid Error
... should not expose the vulnerability Microsoft has corrected and should allow screens with large amounts of data to save without error. Although we are recommending 6,000, it may be necessary for some customers to increase this number to resolve this issue. We recommend not increasing this value to m ...
... should not expose the vulnerability Microsoft has corrected and should allow screens with large amounts of data to save without error. Although we are recommending 6,000, it may be necessary for some customers to increase this number to resolve this issue. We recommend not increasing this value to m ...
UAE Online Child Safety Awareness Campaign
... person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Computing ...
... person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Computing ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.