Active Directory Domain Policy
... ICT: Information and communications technology is an umbrella term used to cover all network, computing, software, and telecommunications systems and resources, including storage and peripheral devices, whether used for research, teaching or administration. Infrastructure: The computer and communica ...
... ICT: Information and communications technology is an umbrella term used to cover all network, computing, software, and telecommunications systems and resources, including storage and peripheral devices, whether used for research, teaching or administration. Infrastructure: The computer and communica ...
brendan_kidwell_resu..
... Web Developer and Application Programmer with over 10 years of professional experience. Expertise in all aspects of web site development, including server-side application programming, client-side HTML/JavaScript programming, and graphic design. Expertise in relational database management, GIS, and ...
... Web Developer and Application Programmer with over 10 years of professional experience. Expertise in all aspects of web site development, including server-side application programming, client-side HTML/JavaScript programming, and graphic design. Expertise in relational database management, GIS, and ...
Windows Vista Performance Technologies
... Use Prioritized IO whenever possible Ensure your startup apps function correctly with startup app boxing Drivers and services not affected ...
... Use Prioritized IO whenever possible Ensure your startup apps function correctly with startup app boxing Drivers and services not affected ...
Antivirus Software
... Limit access to services that are not disabled Use a firewall if you’re connected to the Internet Disable networking protocols that are not used Review services related to remote access and networking, and remove any that are non-essential ...
... Limit access to services that are not disabled Use a firewall if you’re connected to the Internet Disable networking protocols that are not used Review services related to remote access and networking, and remove any that are non-essential ...
presentation source
... – group names <= 15 digits – servers: DOS with add on, Windows for Workgroups, Windows 95, NT WS and Server. – Low security for shares, with one password for a resource, all can see share names, but in NT. ...
... – group names <= 15 digits – servers: DOS with add on, Windows for Workgroups, Windows 95, NT WS and Server. – Low security for shares, with one password for a resource, all can see share names, but in NT. ...
Multicom 2000 Bogen Commander Model MCPCI, version 2, Spec
... Bogen Commander Software (MCPCI) The Bogen Commander software shall be a program facilitator for building, system, station, and schedule information. The system shall include Windows®based diagnostic / programming software for system testing and for full remote maintenance via RS-232 or TCP/IP netwo ...
... Bogen Commander Software (MCPCI) The Bogen Commander software shall be a program facilitator for building, system, station, and schedule information. The system shall include Windows®based diagnostic / programming software for system testing and for full remote maintenance via RS-232 or TCP/IP netwo ...
Operating System Security Fundamentals
... – Allows physical entrance to company property – Magnetic cards and biometric measures ...
... – Allows physical entrance to company property – Magnetic cards and biometric measures ...
Computer Concepts And Applications CIS-107-TE
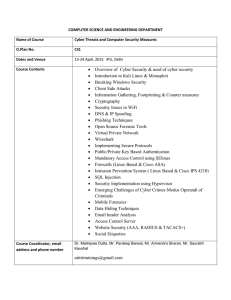
... Passing score: 70%. Your grade will be reported as CR (credit) or NC (no credit). Time limit: 2 hours Topics on the test and their approximate distribution ...
... Passing score: 70%. Your grade will be reported as CR (credit) or NC (no credit). Time limit: 2 hours Topics on the test and their approximate distribution ...
IEEE CONFERENCE ON COMMUNICATION TECHNOLOGIES
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
About Version 9… QuicDoc® Pro – Professional Edition Software
... QuicDoc Version 9 and Office Therapy Version 9. These programs use Microsoft® SQL Server for the backend database. The original Standard Edition software programs use Microsoft Access for their backend database. Version 9 software is being marketed as QuicDoc Pro and Office Therapy Pro - Professiona ...
... QuicDoc Version 9 and Office Therapy Version 9. These programs use Microsoft® SQL Server for the backend database. The original Standard Edition software programs use Microsoft Access for their backend database. Version 9 software is being marketed as QuicDoc Pro and Office Therapy Pro - Professiona ...
Computer Security and Penetration Testing Chapter 16 Windows
... 2008/XP/Vista/7/8 • All of these operating systems are useful for building large corporate networks • All three have good networking features and userfriendly interfaces – Microsoft continues to support these with new security patches ...
... 2008/XP/Vista/7/8 • All of these operating systems are useful for building large corporate networks • All three have good networking features and userfriendly interfaces – Microsoft continues to support these with new security patches ...
Architecting High-Security Systems for Multilateral
... information it is processing and to be free of covert channels between separate clients. In addition to the information-flow aspect, a secure GUI must enable the user to reliably distinguish screen output of different sessions and to know to which session keyboard and mouse events are redirected. Fo ...
... information it is processing and to be free of covert channels between separate clients. In addition to the information-flow aspect, a secure GUI must enable the user to reliably distinguish screen output of different sessions and to know to which session keyboard and mouse events are redirected. Fo ...
Junior Enlisted - Cyber Security
... Implemented security controls to bring IT systems to Security Technical Implementation Guide (STIG) compliance and hardening overall network security posture of the Marine Corps by installing, configuring and maintaining software ...
... Implemented security controls to bring IT systems to Security Technical Implementation Guide (STIG) compliance and hardening overall network security posture of the Marine Corps by installing, configuring and maintaining software ...
CSC 386 Operating Systems Concepts
... 1. Understand the role of an operating system as an intermediary between a user program (or, a user) and the computer hardware. Explain how different operating system components facilitate the role. 2. Compare different operating system design alternatives. 3. Identify their advantages and tradeoffs ...
... 1. Understand the role of an operating system as an intermediary between a user program (or, a user) and the computer hardware. Explain how different operating system components facilitate the role. 2. Compare different operating system design alternatives. 3. Identify their advantages and tradeoffs ...
Document
... for legacy applications) Central logging of network behaviors Protects against application & OS authentication vulnerabilities Leverages tried & true VPN security technology Cons: VPN client required for access ...
... for legacy applications) Central logging of network behaviors Protects against application & OS authentication vulnerabilities Leverages tried & true VPN security technology Cons: VPN client required for access ...
Open Source Software
... • Variety of licenses • FREE – no restrictions on its use • World-wide community of developers and ...
... • Variety of licenses • FREE – no restrictions on its use • World-wide community of developers and ...
View Printable Resume
... Developed embedded systems and user interfaces on Windows CE to monitor data from vision systems Created robotic communication protocols for data transfer to central databases Performed rapid prototyping of smart drilling system to eliminate manufacturing faults System Integration Engineer at ...
... Developed embedded systems and user interfaces on Windows CE to monitor data from vision systems Created robotic communication protocols for data transfer to central databases Performed rapid prototyping of smart drilling system to eliminate manufacturing faults System Integration Engineer at ...
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
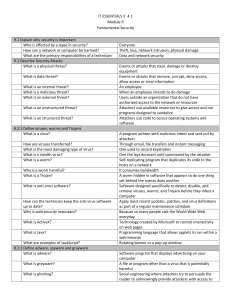
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
Quiz
... c. Wipe the sensitive OS regularly to reduce the amount of data which could be compromised. d. Use the OS access control features to strictly limit where the user can save files. ...
... c. Wipe the sensitive OS regularly to reduce the amount of data which could be compromised. d. Use the OS access control features to strictly limit where the user can save files. ...
Word
... - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk - virtual memory - CD-ROM, DVD-ROM - Flash drive Provides the Interface for Input and Output Devices ...
... - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk - virtual memory - CD-ROM, DVD-ROM - Flash drive Provides the Interface for Input and Output Devices ...
System Administration
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
... Access Controls - specific access controls can include restrictions on: • Locations from which a user can log on to the system or access its resources. • Days/times when access is granted or denied. • The ability to read, write, create and delete directories and files. • The ability to execute progr ...
Windows vs.. Linux Security - Montclair State University
... Win32,Linux/Simile.D is a very complex virus that uses entry-point obscuring, metamorphism, and polymorphic decryption. The virus contains no destructive payload, but infected files may display messages on certain dates. Jack Clarke, European product manager at McAfee, said, "So we will be seeing mo ...
... Win32,Linux/Simile.D is a very complex virus that uses entry-point obscuring, metamorphism, and polymorphic decryption. The virus contains no destructive payload, but infected files may display messages on certain dates. Jack Clarke, European product manager at McAfee, said, "So we will be seeing mo ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.