Database Concepts - classes.ischool.syr.edu
... Computer applications communicate with DBMSs. Users do not communicate with DBMSs directly. As a result DBMSs although they can be used interactively, are not used interactively. A DBMS is not a replacement for sound database design principles. ...
... Computer applications communicate with DBMSs. Users do not communicate with DBMSs directly. As a result DBMSs although they can be used interactively, are not used interactively. A DBMS is not a replacement for sound database design principles. ...
NT Security Overview
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
... organization will have access to the network. In most businesses or organizations there are employees, staff, management and officers. Some can be trusted to access all of the network and others do not have the trust level to access any of the network. The administrator must decide who has access an ...
Web Application Security Vulnerabilities Yen
... the latest patches to these products. Review all code that accepts input from users via the HTTP request and ensure that it provides appropriate size checking on all such ...
... the latest patches to these products. Review all code that accepts input from users via the HTTP request and ensure that it provides appropriate size checking on all such ...
MetaOS Concept • MetaOS developed by Ambient Computing to
... distributed, network-embedded devices • Smart devices and standalone software are abstracted in the same way as resources and peripherals are in traditional operating systems • Supports easy deployment of new services by providing common way to integrate and coordinate devices as well as write appli ...
... distributed, network-embedded devices • Smart devices and standalone software are abstracted in the same way as resources and peripherals are in traditional operating systems • Supports easy deployment of new services by providing common way to integrate and coordinate devices as well as write appli ...
Operating System Security Chapter 9 Operating System Security
... • Security administrators should regularly assess the current status of a computer by locating and analyzing stored status data • Computer forensics is the process of searching for evidence of a specific activity by searching log files and file systems • System footprinting (baselining) is a “snapsh ...
... • Security administrators should regularly assess the current status of a computer by locating and analyzing stored status data • Computer forensics is the process of searching for evidence of a specific activity by searching log files and file systems • System footprinting (baselining) is a “snapsh ...
Section for introduction % \section{Introduction} Over the last several
... 88.6\% from the previous year \cite{Canalys11}. These phones are equipped with a rich set of hardware interfaces and software applications that allow personal and corporate users to interact with both the cyber and physical world through Internet access, email, SMS, and location-based services. To s ...
... 88.6\% from the previous year \cite{Canalys11}. These phones are equipped with a rich set of hardware interfaces and software applications that allow personal and corporate users to interact with both the cyber and physical world through Internet access, email, SMS, and location-based services. To s ...
Slides.
... How Viruses Work • Virus written in assembly language • Inserted into another program • Virus dormant until program executed ...
... How Viruses Work • Virus written in assembly language • Inserted into another program • Virus dormant until program executed ...
Huawei Videoconferencing System Interoperates with Microsoft
... Video communication is becoming increasingly popular as an integral component of any collaboration system. However, enterprises are faced with an awkward situation where room-based videoconferencing systems cannot interoperate with unified communications (UC) systems that incorporate functions such ...
... Video communication is becoming increasingly popular as an integral component of any collaboration system. However, enterprises are faced with an awkward situation where room-based videoconferencing systems cannot interoperate with unified communications (UC) systems that incorporate functions such ...
Insert Title Here
... Obtain & modify intellectual property Bypass system security mechanisms Ability to mask failure detection ...
... Obtain & modify intellectual property Bypass system security mechanisms Ability to mask failure detection ...
Resume - OPResume.com
... eliminate violations. Conferred with computer user department personnel and Computer Programmer to plan data security for new or modified software. Assist regional office staff with computer hardware and software needs, as well as assisting provider and regional office staff with the Child Care Admi ...
... eliminate violations. Conferred with computer user department personnel and Computer Programmer to plan data security for new or modified software. Assist regional office staff with computer hardware and software needs, as well as assisting provider and regional office staff with the Child Care Admi ...
Security
... creates a breach of security, or causing a normal process to change its behavior and create a breach, is a common goal of crackers. In fact, even most nonprogram security events have as their goal causing a program threat. For example, while it is useful to log in to a system without authorization, ...
... creates a breach of security, or causing a normal process to change its behavior and create a breach, is a common goal of crackers. In fact, even most nonprogram security events have as their goal causing a program threat. For example, while it is useful to log in to a system without authorization, ...
Introduction to Computers
... software for limited cost or free. May also give full features but for a short period of time. Open Source: Completely free to use on as many computers and for as many users as necessary. Includes access to the current source code. Alpha/Beta/Release Candidate (RC): A precursor to the next relea ...
... software for limited cost or free. May also give full features but for a short period of time. Open Source: Completely free to use on as many computers and for as many users as necessary. Includes access to the current source code. Alpha/Beta/Release Candidate (RC): A precursor to the next relea ...
Chapter 24 - William Stallings, Data and Computer
... To guard against the baneful influence exerted by strangers is therefore an elementary dictate of savage prudence. Hence before strangers are allowed to enter a district, or at least before they are permitted to mingle freely with the inhabitants, certain ceremonies are often performed by the native ...
... To guard against the baneful influence exerted by strangers is therefore an elementary dictate of savage prudence. Hence before strangers are allowed to enter a district, or at least before they are permitted to mingle freely with the inhabitants, certain ceremonies are often performed by the native ...
Dan A CSC 345 Term Paper
... disguised as being benign, but allows other users to connect without being detected. The cost of having an infected or otherwise compromised mobile device is high. A user could experience a denial-of-service, which could result in the loss of uptime and data. An especially vicious attack could invol ...
... disguised as being benign, but allows other users to connect without being detected. The cost of having an infected or otherwise compromised mobile device is high. A user could experience a denial-of-service, which could result in the loss of uptime and data. An especially vicious attack could invol ...
Understanding and Installing Firewalls
... users who valued openness for sharing and collaboration was ended by a number of major internet security breaches which occurred in the late 1980s: Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic ...
... users who valued openness for sharing and collaboration was ended by a number of major internet security breaches which occurred in the late 1980s: Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic ...
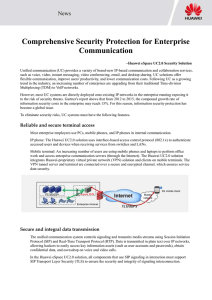
Comprehensive Security Protection for
... allowing hackers to easily access key information assets (such as user accounts and passwords), obtain confidential data, and eavesdrop on voice and video calls. In the Huawei eSpace UC2.0 solution, all components that use SIP signaling in interaction must support SIP Transport Layer Security (TLS) ...
... allowing hackers to easily access key information assets (such as user accounts and passwords), obtain confidential data, and eavesdrop on voice and video calls. In the Huawei eSpace UC2.0 solution, all components that use SIP signaling in interaction must support SIP Transport Layer Security (TLS) ...
PowerPoint Presentation - Security Risk Management
... Automate: Keep Windows up-to-date with the latest critical and security patches ...
... Automate: Keep Windows up-to-date with the latest critical and security patches ...
Current IT Security Threats
... compromise, loss of sensitive information, and use of enterprise systems for illegal activity Instant Messaging Peer-to-Peer Programs ...
... compromise, loss of sensitive information, and use of enterprise systems for illegal activity Instant Messaging Peer-to-Peer Programs ...
Implementing Security for Electronic Commerce
... that the holder of the software is a trusted name. A certification authority (CA) issues a digital certificate to an organization or an individual when provided with required information. A certificate authority also signs the certificate in the form of a public encrypted key, which unlocks the cert ...
... that the holder of the software is a trusted name. A certification authority (CA) issues a digital certificate to an organization or an individual when provided with required information. A certificate authority also signs the certificate in the form of a public encrypted key, which unlocks the cert ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.