* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Document
Cryptanalysis wikipedia , lookup
Wireless security wikipedia , lookup
Microsoft Security Essentials wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Public-key cryptography wikipedia , lookup
Mobile security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Computer virus wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cryptography wikipedia , lookup
History of cryptography wikipedia , lookup
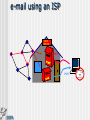
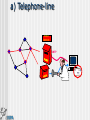
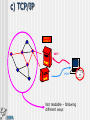
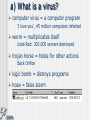
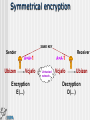
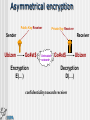
SECURITY Bart Vansevenant Who is who? Who can read what? Traces Virusses Safety and confidentiality Who is who? Who can read what ? Telephone line Mail server TCP/IP Echelon & Carnivore e-mail using an ISP POST OFFICE SMTP POP3 a) Telephone-line POST OFFICE SMTP POP3 b) e-mail server Everything on the servers can be read or copied POST OFFICE SMTP POP3 c) TCP/IP POST OFFICE SMTP POP3 Not readable – following different ways Echelon/Carnivore Source: http://www.fbi.gov/hq/lab/carnivore/carnlrgmap.htm Traces Traces The IP address of your computer is : 213.177.129.120 your DNS address is : adsl-129-120.wanadoo.be We know you use : Microsoft Windows 98 Your navigator has the code: Mozilla/4.78 [en] (Win98; U) In fact it is: Netscape Communicator 4.x English What you did is stored : Windows 95 C:\Windows\Temporary Internet Files\ Windows NT C:\WinNt\Temporary Internet Files\ A nice demo in french on: www.cnil.fr Virus What is a virus and types? How is a computer infected? Danger a) What is a virus? computer virus = a computer program 'I love you', 45 million computers infected worm = multiplicates itself code Red: 300.000 servers destroyed trojan horse = hides for other actions Back Orifice logic bomb = distroys programs hoax = false alarm b) How is a computer infected? files attached to e-mail (attachment) diskettes other c) Danger infecting components of your system effects: malfunctions deletion of data wiping of hard disk ... Solutions to provide safety and confidentiality solving identity problem and unauthorised reading protection against traces protection against virusses Identity and unauthorised reading Encryption Purpose Functions How? Functions of encryption Authentication Integrity Confidentiality Symmetrical encryption SAME KEY Sender Receiver A=A+1 Ubizen Vcjafo Encryption E(…) A=A-1 Untrusted network Vcjafo Ubizen Decryption D(…) Asymmetrical encryption Public Key Receiver Private Key Receiver Sender Ubizen Receiver Go#st$ Encryption E(…) Untrusted network Go#st$ Ubizen Decryption D(…) confidentiality towards receiver Asymmetrical encryption Private Key Sender Public Key Sender Sender Ubizen Receiver Go#st$ Encryption E(…) Untrusted network Go#st$ Ubizen Decryption D(…) authentication of sender Example Example Example Against leaving traces Traces at the ISP Traces on own computer Against virusses anti-virus program Norton, McAfee, eSafe, F-Secure, … watch out for attachments .exe, .com, .pif, .vbs, .doc, .xls, … www.bipt.be