XTM 2 and 5 Series
... Malware Delivery More Dynamic/Agile Between their increased reliance on botnets and the introduction of new evasion techniques, the servers that deliver malware have become much more dynamic and agile ...
... Malware Delivery More Dynamic/Agile Between their increased reliance on botnets and the introduction of new evasion techniques, the servers that deliver malware have become much more dynamic and agile ...
FREE Sample Here
... A computer virus consists of segments of code that perform malicious actions. This code behaves very much like a virus pathogen attacking animals and plants, using the cell’s own replication machinery to propagate and attack. The code attaches itself to the existing program and takes control of that ...
... A computer virus consists of segments of code that perform malicious actions. This code behaves very much like a virus pathogen attacking animals and plants, using the cell’s own replication machinery to propagate and attack. The code attaches itself to the existing program and takes control of that ...
Chapter 02: The Need for Security
... program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program that replicates itself constantly, without requiring another program to provide a safe environment f ...
... program’s access to the targeted computer. The virus-controlled target program then carries out the virus’s plan, by replicating itself into additional targeted systems. A worm is a malicious program that replicates itself constantly, without requiring another program to provide a safe environment f ...
IPS/IDS - SudeeraJ.com
... • Ability to update all the security functions or programs concurrently • Eliminates the need for systems administrators to maintain multiple security programs over time ...
... • Ability to update all the security functions or programs concurrently • Eliminates the need for systems administrators to maintain multiple security programs over time ...
Exam Topics in This Chapter
... the exam upon which this book is based. When Cisco releases an entirely new exam, the changes are usually too extensive to provide in a simple update appendix. In those cases, you might need to consult the new edition of the book for the updated content. This appendix attempts to fill the void that ...
... the exam upon which this book is based. When Cisco releases an entirely new exam, the changes are usually too extensive to provide in a simple update appendix. In those cases, you might need to consult the new edition of the book for the updated content. This appendix attempts to fill the void that ...
Approved 400-Level courses to count towards CSE Graduate
... Approved 400-Level courses to count towards CSE Graduate Program IMPORTANT: Students who have taken any of the 4XX courses listed below as 598, cannot take the same class at the 400-level. CSE 408 Multimedia Information Systems CSE 412 Database Management CSE 414 Advanced Database Concepts CSE 432 O ...
... Approved 400-Level courses to count towards CSE Graduate Program IMPORTANT: Students who have taken any of the 4XX courses listed below as 598, cannot take the same class at the 400-level. CSE 408 Multimedia Information Systems CSE 412 Database Management CSE 414 Advanced Database Concepts CSE 432 O ...
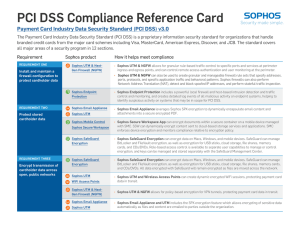
PCI DSS Compliance Reference Card
... ÌÌ Secure Email Gateway can detect and block viruses and known phishing emails that may include malware. ...
... ÌÌ Secure Email Gateway can detect and block viruses and known phishing emails that may include malware. ...
Intelligent Cybersecurity for the Real World Hermes Romero Regional Security Sales, Sourcefire
... FireSIGHT™ Context Explorer View all application traffic… ...
... FireSIGHT™ Context Explorer View all application traffic… ...
3 Responding to Incidents
... Other adverse events that cause system crashes include natural disasters and power-related disruptions (e.g., floods, fires, electrical outages, and excessive heat). For the purpose of this program, the term "incident" refers to an intentional and/or unintentional adverse event that is related to IS ...
... Other adverse events that cause system crashes include natural disasters and power-related disruptions (e.g., floods, fires, electrical outages, and excessive heat). For the purpose of this program, the term "incident" refers to an intentional and/or unintentional adverse event that is related to IS ...
Detecting Malicious SMB Activity Using Bro
... services from server programs on a computer network.” (Microsoft, 2013). Applications can utilize the SMB protocol to retrieve files and resources on a remote server (Microsoft, 2013). SMB primarily uses TCP port 445 for communication, occasionally using TCP port 139 on legacy systems. This paper co ...
... services from server programs on a computer network.” (Microsoft, 2013). Applications can utilize the SMB protocol to retrieve files and resources on a remote server (Microsoft, 2013). SMB primarily uses TCP port 445 for communication, occasionally using TCP port 139 on legacy systems. This paper co ...
Document
... log to create a new log that is smaller Log conversion is parsing a log in one format and storing its entries in a second format. Text to XML etc Log normalization, each log data field is converted to a particular data representation and categorized consistently. Example converting all date/times in ...
... log to create a new log that is smaller Log conversion is parsing a log in one format and storing its entries in a second format. Text to XML etc Log normalization, each log data field is converted to a particular data representation and categorized consistently. Example converting all date/times in ...
Password Security
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
... choosing a sentence that incorporates something unique about the website or account, and then using the first letter of each word as your password. For example the sentence: "This is my August password for the Center for Internet Security website." would become "TimAp4tCfISw." Since a strong passwor ...
LogMeIn Security – an In-Depth Look
... installing a remote access product. Remote access products are perceived as high risk factors, but mainly for psychological reasons. When a user first sees a remote access solution in action, their first negative reaction is usually with regard to the security implications. This is perfectly normal, ...
... installing a remote access product. Remote access products are perceived as high risk factors, but mainly for psychological reasons. When a user first sees a remote access solution in action, their first negative reaction is usually with regard to the security implications. This is perfectly normal, ...
McGraw-Hill
... Computers are required to perform many different tasks at once—to do task management Task: An operation such as storing, printing, or calculating Multitasking: Handling more than one program concurrently ...
... Computers are required to perform many different tasks at once—to do task management Task: An operation such as storing, printing, or calculating Multitasking: Handling more than one program concurrently ...
Aspects of Biological Evolution and Their
... The control mechanism which regulates this access is either the .rhost or hosts.equiv file. The .rhost file can either contain a list of machine-user name pairs, one per line, of systems and users that have access to the machine or simply a line containing the machine name. In the first case the rig ...
... The control mechanism which regulates this access is either the .rhost or hosts.equiv file. The .rhost file can either contain a list of machine-user name pairs, one per line, of systems and users that have access to the machine or simply a line containing the machine name. In the first case the rig ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
... As the sub product of electronic mail services, spam became a serious issue in penetrating into any mail system and this types of penetration is mainly used by hackers for stealing confidential data without the knowledge of the user. Generally few hackers use worm which is standalone malware compute ...
Click for PDF - Cyber Security Services
... goal of this strategy is to ensure that the only users who have administrative privileges to operating systems and applications such as databases, are those users who require such privileges based on their job role and duties. 11. Mitigation strategy ‘User application configuration hardening ...
... goal of this strategy is to ensure that the only users who have administrative privileges to operating systems and applications such as databases, are those users who require such privileges based on their job role and duties. 11. Mitigation strategy ‘User application configuration hardening ...
Application research and analysis based on Bitlocker
... then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the desktop icon, select the system disk (C:), click the right key and chooseBitlocker (B), requires the startup key when ...
... then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the desktop icon, select the system disk (C:), click the right key and chooseBitlocker (B), requires the startup key when ...
EH34803812
... 2003 [2], and “Witty”/ “Sasser” worms in 2004 [3]. Many active worms are used to infect a large number of computers and recruit them as bots or zombies, which are networked together to form botnets [4]. Worms can start on a host (Computer) in various fashions. It may be an attachment to a mail and w ...
... 2003 [2], and “Witty”/ “Sasser” worms in 2004 [3]. Many active worms are used to infect a large number of computers and recruit them as bots or zombies, which are networked together to form botnets [4]. Worms can start on a host (Computer) in various fashions. It may be an attachment to a mail and w ...
the catalogue here
... data protection in a flexible, centrally-managed solution, it lowers the cost and effort to deploy and manage while closing critical security and compliance gaps—for complete end-user protection across endpoints, mobile devices, email, and gateway. ...
... data protection in a flexible, centrally-managed solution, it lowers the cost and effort to deploy and manage while closing critical security and compliance gaps—for complete end-user protection across endpoints, mobile devices, email, and gateway. ...
report 2012 - CERT Polska
... unsolicited messages. These are mostly computers infected with malware, thus bots used for mass mailing without the knowledge or consent of their legitimate owners. In 2012 we received 5,189,274 submissions related to spam from Polish IP addresses, 10.9% more than in 2011. These are related to 1,648 ...
... unsolicited messages. These are mostly computers infected with malware, thus bots used for mass mailing without the knowledge or consent of their legitimate owners. In 2012 we received 5,189,274 submissions related to spam from Polish IP addresses, 10.9% more than in 2011. These are related to 1,648 ...
Introduction to Computer Security
... • Overt channel – Communication channel that is used in the way it is intended to use ...
... • Overt channel – Communication channel that is used in the way it is intended to use ...
Introduction to Information Security Chapter 2
... Metric: did testers get access either without a password or by gaining unauthorized access to a password? ...
... Metric: did testers get access either without a password or by gaining unauthorized access to a password? ...
Using Spamhaus BGPf in a production environment
... In 2012, Spamhaus launched a new service to protect internet users from cyber threats and crime being committed through these threats by using so-called Trojan horses - the Spamhaus BGP feed (BGPf ). In the past year, Spamhaus was able to identify thousands of malicious server operated by cybercrimi ...
... In 2012, Spamhaus launched a new service to protect internet users from cyber threats and crime being committed through these threats by using so-called Trojan horses - the Spamhaus BGP feed (BGPf ). In the past year, Spamhaus was able to identify thousands of malicious server operated by cybercrimi ...
Malware

Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. Malware is defined by its malicious intent, acting against the requirements of the computer user, and does not include software that causes unintentional harm due to some deficiency. The term badware is sometimes used, and applied to both true (malicious) malware and unintentionally harmful software.Malware may be stealthy, intended to steal information or spy on computer users for an extended period without their knowledge, as for example Regin, or it may be designed to cause harm, often as sabotage (e.g., Stuxnet), or to extort payment (CryptoLocker). 'Malware' is an umbrella term used to refer to a variety of forms of hostile or intrusive software, including computer viruses, worms, trojan horses, ransomware, spyware, adware, scareware, and other malicious programs. It can take the form of executable code, scripts, active content, and other software. Malware is often disguised as, or embedded in, non-malicious files. As of 2011 the majority of active malware threats were worms or trojans rather than viruses.In law, malware is sometimes known as a computer contaminant, as in the legal codes of several U.S. states.Spyware or other malware is sometimes found embedded in programs supplied officially by companies, e.g., downloadable from websites, that appear useful or attractive, but may have, for example, additional hidden tracking functionality that gathers marketing statistics. An example of such software, which was described as illegitimate, is the Sony rootkit, a Trojan embedded into CDs sold by Sony, which silently installed and concealed itself on purchasers' computers with the intention of preventing illicit copying; it also reported on users' listening habits, and unintentionally created vulnerabilities that were exploited by unrelated malware.Software such as anti-virus, anti-malware, and firewalls are used to protect against activity identified as malicious, and to recover from attacks.