* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download IPS/IDS - SudeeraJ.com
Survey
Document related concepts
Cyberwarfare wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cross-site scripting wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Security-focused operating system wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Cyberattack wikipedia , lookup
Computer security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Distributed firewall wikipedia , lookup
Transcript
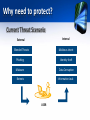
Agenda • • • • • • • • • Introduction Intrusion & current Threat scenario Introduction to IDS/IPS IDS/IPS Detection Techniques Main Types of IDS/IPS Introduction of UTM Intrusion Detection with Tripwire Summary References Q&A What is Intrusion? • A set of actions aimed at compromising the security goals (confidentiality, integrity, availability of a computing/networking resource) Why need to protect? Current Threat Scenario Internal External Malicious intent Blended Threats Phishing Identity theft Malware Data Corruption Botnets Information Leak USER Why need to protect? (Cont..) • There are two types of threats – External threats – Internal threats Why need to protect? (Cont..) • External Threats (Targeting the Individuals) Who are the attackers? • It is no longer individuals • Attacks executed as joint ventures among professional programmers with access to greater pooled resources • Consortiums dedicated to the creation and distribution of malicious software intended to steal money from individuals Why need to protect? (Cont..) What are the motives? • To gain attention • Financial theft (main driver of malware authors) • Identity theft Who are the victims? • Small corporations • Key Individuals • Basically any one Why need to protect? (Cont..) • Internal Threats – Insiders acting as initiators themselves or as conduits for other attacks – User Ignorance – Malicious Intent - Intentional security breaches – Disgruntled employees Why need to protect? (Cont..) • Why such Insider threats can lead to more damage? – Employees carry valid authorization and privacy of the organization’s information – Dishonest insiders’ can exploit an organization’s vulnerabilities To commit identity fraud and expose confidential information For personal gain or organized crime – Insider attacks can be more difficult to detect than external penetration attempts How to protect? There are two ways of protection mechanisms • Intrusion detection (IDS) • Intrusion prevention (IPS) Introduction to IDS • Intrusion detection system (IDS) – A system that automatically identifying and responding to intrusion activities Introduction to IPS • Intrusion prevention system (IPS) – A system that has an ambition to both detect intrusions and manage responsive actions Introduction to IPS (Cont..) – Technically, an IPS contains an IDS and combines it with preventive measures – IPS use IDS algorithms to monitor and drop/allow traffic based on expert analysis – The ”firewall” part of an IPS can prevent malicious traffic from entering/exiting the network Basic assumptions for IDS/IPS • Basic assumptions: – System activities are observable – Normal and intrusive activities have distinct evidence – The goal of an IDS/IPS is to detect the difference How IDS/IPS Works? • The IPS monitors the network much like the IDS but when an event occurs, it takes action based on prescribed rules • Security administrator can define such rules so the systems respond in the way they would How IDS/IPS Works? (Cont..) How IDS/IPS Works? (Cont..) • IPS can be achieved through three main approaches – Building systems with no vulnerability – Taking perfect remediation steps to uncover vulnerabilities and patch them – Detecting the exploit attempts and blocking them before serious damage is done How IDS/IPS Protects? • IPS technologies can respond to a detected threat by attempting to prevent it from succeeding. They use several response techniques, which can be divided into the following groups – The IPS stops the attack itself – The IPS changes the security environment – The IPS changes the attack’s content How IDS/IPS Protects?(Cont..) • The IPS stops the attack itself – Terminate the network connection or user session that is being used for the attack – Block access to the target from the offending user account, IP address, or other attacker attribute. Block all access to the targeted host, service, application, or other resource How IDS/IPS Protects?(Cont..) • The IPS changes the security environment – The IPS could change the configuration of other security controls to disrupt an attack – Common examples are reconfiguring a network device such as firewall, router, and switch to block access from the attacker How IDS/IPS Protects?(Cont..) • The IPS changes the attack’s content – IPS technologies can remove or replace malicious portions of an attack to make it benign An example is an IPS that acts as a proxy and normalizes incoming requests and permitting the cleaned data to reach its recipient How IDS/IPS detects? There are different types of approaches is used in the IPS to secure the network – Signature-Based – Anomaly-Based – Policy-Based – Protocol-Analysis-Based These approaches are also used to classify IDS/IPS systems and the classification is called IDS/IPS by Detection Model How IDS/IPS detects? (Cont...) • Signature-Based IPS – It is the commonly used by many IPS solutions – Signatures are added to the devices that identify a pattern that the most common attacks present – That’s why it is also known as pattern matching – These signatures can be added, tuned, and updated to deal with the new attacks How IDS/IPS detects? (Cont...) • Policy-based IPS – It is more concerned with enforcing the security policy of the organization – Alarms are triggered if activities are detected that violate the security policy coded by the organization – With this type approaches security policy is written into the IPS device How IDS/IPS detects? (Cont...) • Anomaly-Based approach IPS – It is also called as profile-based – It attempts to discover activity that deviates from what an engineer defines as normal activity – Anomaly-based approach can be statistical anomaly detection and non-statistical anomaly detection – The statistical approach is about the traffic patterns on the network itself, and the non-statistical method is about information coded by the solution vendor How IDS/IPS detects?(Cont...) • Protocol-analysis-based IPS – It is similar to signature based approach – Most signatures examines common settings, but the protocol-analysis-based approach can do much deeper packet inspection and is more flexible in finding some types of attacks IDS/IPS Detection Techniques • Stateless – Most of the network-based IDS currently available are stateless. They typically monitor and analyze all traffic in real-time on a packet-by-packet basis against a database of known patters for a match • State full – A State-full IDS can be defined as a packet filtering and analysis mechanism which makes decision on current packet AND information from previous packets IDS/IPS Detection Techniques (Cont..) • Deep Packet Inspection – Deep Packet Inspection mostly used in NIDS to look within the application payload of a packet or traffic stream and make decisions on the significance of that data based on the content of that data (analyze the packet header fields – DPI technology can be effective against buffer overflow attacks, denial of service (DoS) attacks, sophisticated intrusions, and a small percentage of worms that fit within a single packet Main Types of IDS/IPS • Scope based IPS protection (or by location) – Host-Based Intrusion Prevention System (HIPS) – Network-Based Intrusion Prevention System (NIPS) Host Based IDS/IPS • Host-based IPS is a software program that resides on individual systems such as servers, workstations or notebooks • Traffic flowing into or out of that particular system is inspected and the behaviour of the applications and operating system may be examined for indications of an attack • These host system-specific programs or agents may protect just the operating system, or applications running on the host as well as web servers Host Based IDS/IPS (Cont..) • When an attack is detected, the Host IPS software either blocks the attack at the network Interface level, or issues commands to the application or operating system to stop the behaviour initiated by the attack • It binds closely with the operating system kernel and services, monitoring and intercepting system calls to the kernel or APIs in order to prevent attacks as well as log them • One potential disadvantage with this approach is that, given the necessarily tight integration with the host operating system, future operating system upgrades could cause problems Benefits of Host IDS/IPS • Protects mobile systems from attack when attached outside the protected network • Prevents internal attack or misuse on devices located on the same network segment, Network IPS only provides protection for data moving between different segments • Protects against encrypted attacks where the encrypted data stream terminates at the system being protected Network Based IDS/IPS • Network-Based Intrusion Prevention System (NIPS) is software or dedicated hardware system that connects directly to a network segment and protects all of the systems attached to the same or downstream network segments Network Based IDS/IPS (Cont..) • NIPS has at least two network interfaces, one designated as internal and one as external • As packets appear at the either interface they are passed to the detection engine, at which point the IPS device functions much as any IDS would in determining whether or not the packet being examined poses a threat Benefits of Network IDS/IPS • Easy deployment as a single sensor can protect hundreds on systems • A single control point for traffic can protect thousands of systems located down stream of the device (no matter what the operating system or application) • Protects against network DoS, DDos attacks and SYN flood etc Introduction of UTM • Unified threat management (UTM) refers to a comprehensive security product that includes protection against multiple threats • A UTM product typically includes a firewall, antivirus software, content filtering and a spam filter in a single integrated package Advantages of UTM • Simplicity • Streamlined installation and use • Ability to update all the security functions or programs concurrently • Eliminates the need for systems administrators to maintain multiple security programs over time Disadvantages of UTM • UTM introduces a single point of failure it lead for all the network security elements • There is always a possibility of performance constraint as there are limitations in hardware processing capabilities to handle so many applications/users simultaneously • There is always challenge from cloud computing initiatives and UTM’s might have to be deployed in a virtual manner Intrusion Detection with Tripwire • Tripwire compares files and directories against a baseline database of file locations, dates modified, and other data • It generates the baseline by taking a snapshot of specified files and directories in a known secure state • After creating the baseline database, Tripwire compares the current system to the baseline and reports any modifications, additions, or deletions Tripwire Architecture Tripwire Commands • twinstall.sh - Run the configuration script (/etc/tripwire/twinstall.sh) • tripwire –init - The /var/lib/tripwire directory contains the Tripwire database of your system's files (*.twd) and a report directory where Tripwire reports are stored • tripwire –check - To run an integrity check Tripwire compares the current, actual file system objects with their properties as recorded in its database. Violations are printed to standard Tripwire Sample Report Summary • Due to the dynamic nature of network intrusion threats, deploying a mixture of both technologies (HIPS & NIPS) will provide the greatest level of protection for critical assets References • http://www.symantec.com/connect/articles/evolution-intrusiondetection-systems • http://searchmidmarketsecurity.techtarget.com/sDefinition/0,,sid 198_gci295031,00.html • http://searchmidmarketsecurity.techtarget.com/sDefinition/0,,sid 198_gci295031,00.html • http://www.hig.no/index.php/content/download/8588/118736/fi le/Topic_1.ppt • http://searchsecurity.techtarget.com/tip/0,289483,sid14_gci1092 691,00.html • http://idstutorial.com/anomaly-detection.php Questions?