XTM 2 and 5 Series
... Blocks access to IM/P2P download sites, WebMail and over 9,000+ spyware sites ...
... Blocks access to IM/P2P download sites, WebMail and over 9,000+ spyware sites ...
Behavioral fine-grained detection and classification of P2P bots
... Han), [email protected] (Chirine Wolley) ...
... Han), [email protected] (Chirine Wolley) ...
Lab Additions/Suggestions previously done
... Appendix 1-E Linux Firewall exploit Appendix 1-F ZoneAlarm Appendix 1 –G ProcessGuard application to check and control various other applications Appendix 1-H Firewall Builder Appendix 1-I Firehole ...
... Appendix 1-E Linux Firewall exploit Appendix 1-F ZoneAlarm Appendix 1 –G ProcessGuard application to check and control various other applications Appendix 1-H Firewall Builder Appendix 1-I Firehole ...
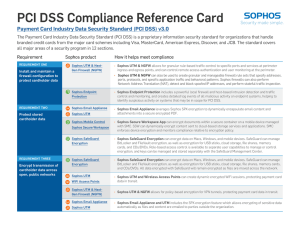
PCI DSS Compliance Reference Card
... ÌÌ Sophos Mobile Security for Android can protect users from malicious applications or potential threats within potentially unwanted applications (PUAs) downloaded by users. ...
... ÌÌ Sophos Mobile Security for Android can protect users from malicious applications or potential threats within potentially unwanted applications (PUAs) downloaded by users. ...
EMC Infrastructure for Microsoft Private Cloud
... Today, many organizations have made a decisive move to revamp the existing storage strategy by running critical applications like Microsoft Exchange Server, SharePoint Server, and SQL Server on a virtualized infrastructure. By consolidating application servers on a virtualized platform, customers ca ...
... Today, many organizations have made a decisive move to revamp the existing storage strategy by running critical applications like Microsoft Exchange Server, SharePoint Server, and SQL Server on a virtualized infrastructure. By consolidating application servers on a virtualized platform, customers ca ...
FY05 Plan
... Patch Information Comprehensive patch information • After scanning, view the list of available patches • View details of each patch e.g.. severity, reboot required, etc. ...
... Patch Information Comprehensive patch information • After scanning, view the list of available patches • View details of each patch e.g.. severity, reboot required, etc. ...
North American Global IPv6 Summit June 24
... – Real-Time communication and Video streaming applications offered by Agora, Microsoft and others ...
... – Real-Time communication and Video streaming applications offered by Agora, Microsoft and others ...
Jack Breese (Microsoft) & Daphne Koller (Stanford)
... Summarizing CSP Hardness With Continuous Probability Distributions ...
... Summarizing CSP Hardness With Continuous Probability Distributions ...
Belief Networks and Decision-Theoretic Reasoning for
... Summarizing CSP Hardness With Continuous Probability Distributions ...
... Summarizing CSP Hardness With Continuous Probability Distributions ...
Dell SonicWALL SuperMassive Firewalls
... protection. The team leverages more than one million sensors across the globe for malware samples and for telemetry feedback on the latest threat information, which in turn is fed into the intrusion prevention, anti-malware and application detection capabilities. SonicWALL NGFW customers with the la ...
... protection. The team leverages more than one million sensors across the globe for malware samples and for telemetry feedback on the latest threat information, which in turn is fed into the intrusion prevention, anti-malware and application detection capabilities. SonicWALL NGFW customers with the la ...
SysKonnect SK-9E21D 10/100/1000Base
... Windows 2000, Windows XP and Windows Server 2003. Additionally, a value added package is available for Windows 2000, Windows XP and Windows Server 2003 enabling Virtual LAN (VLAN) and Link Aggregation support. This package also includes a utility program for easy installation and configuration. For ...
... Windows 2000, Windows XP and Windows Server 2003. Additionally, a value added package is available for Windows 2000, Windows XP and Windows Server 2003 enabling Virtual LAN (VLAN) and Link Aggregation support. This package also includes a utility program for easy installation and configuration. For ...
CISSP Guide to Security Essentials, Ch4
... called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
... called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
SecuROM™ Disc Check
... A unique, uncopyable electronic keycode is added during the glass mastering process for CD-ROM and DVDROM replication. Unlike other digital rights management solutions on the market, the SecuROM™ keycode is fully within the CD/DVD-ROM specification, thereby ensuring the highest possible compatibilit ...
... A unique, uncopyable electronic keycode is added during the glass mastering process for CD-ROM and DVDROM replication. Unlike other digital rights management solutions on the market, the SecuROM™ keycode is fully within the CD/DVD-ROM specification, thereby ensuring the highest possible compatibilit ...
Market Guide for Enterprise SBC
... price points for small, midsize and large organizations. The AudioCodes E-SBC portfolio covers the capacity and interface needs of distributed enterprises, which positions the company to be a sole source vendor for centralized and distributed deployments within the same network. The company has been ...
... price points for small, midsize and large organizations. The AudioCodes E-SBC portfolio covers the capacity and interface needs of distributed enterprises, which positions the company to be a sole source vendor for centralized and distributed deployments within the same network. The company has been ...
SonicWALL Global Management System Datasheet
... Network Security Appliance (NSA), NSA or PRO Series firewall with minimum firmware and SonicWall VPN-based firewalls ...
... Network Security Appliance (NSA), NSA or PRO Series firewall with minimum firmware and SonicWall VPN-based firewalls ...
Physical Security
... • One of the challenges in a modern enterprise is understanding the impact of system changes from the installation or upgrade of an application on a system. • To help you overcome that challenge, Microsoft has released the Attack Surface Analyzer (ASA), a free tool that can be deployed on a system b ...
... • One of the challenges in a modern enterprise is understanding the impact of system changes from the installation or upgrade of an application on a system. • To help you overcome that challenge, Microsoft has released the Attack Surface Analyzer (ASA), a free tool that can be deployed on a system b ...
Mobility Devices
... cornerstone of most mobile users’ travel gear, but new form factors, such as the Tablet PC and Smartphone, are brilliant complements that better address their needs in different scenarios. Microsoft is extending the business features in Microsoft Windows XP Professional and Office Professional Editi ...
... cornerstone of most mobile users’ travel gear, but new form factors, such as the Tablet PC and Smartphone, are brilliant complements that better address their needs in different scenarios. Microsoft is extending the business features in Microsoft Windows XP Professional and Office Professional Editi ...
Chapter 13 - SaigonTech
... • Switched 56K leased lines are older, digital, pointto-point communication links offered by local and long-distance telcos – They offered the best alternative to PSTN connections, particularly given their on-demand structure – A circuit was not dedicated to a single customer; ondemand pathways esta ...
... • Switched 56K leased lines are older, digital, pointto-point communication links offered by local and long-distance telcos – They offered the best alternative to PSTN connections, particularly given their on-demand structure – A circuit was not dedicated to a single customer; ondemand pathways esta ...
Microsoft Windows 2000? Router Configuration Guide
... The Microsoft Windows 2000 Router Configuration Guide presents a general overview of the routing features, recommended routing protocol, and filtering services. This overview is designed to show the recommended functionality in various locations within a network. The author intends for this guide to ...
... The Microsoft Windows 2000 Router Configuration Guide presents a general overview of the routing features, recommended routing protocol, and filtering services. This overview is designed to show the recommended functionality in various locations within a network. The author intends for this guide to ...
Harden Communications
... use the destination and source IP address information required. In Windows Server 2003, in addition to naming a specific IP address or a specific IP subnet, you may select DNS, DHCP, WINS, or default gateway information. (The computer’s TCP/IP configuration information will be used to supply the IP ...
... use the destination and source IP address information required. In Windows Server 2003, in addition to naming a specific IP address or a specific IP subnet, you may select DNS, DHCP, WINS, or default gateway information. (The computer’s TCP/IP configuration information will be used to supply the IP ...
The Blaster Worm: Then and Now
... from August 2003 and August 2004, and tried to account for DHCP effects. It’s possible that several infected hosts simply moved within the same LAN due to DHCP or other administrative decisions, so again we compared only the first 24 bits of the host IP addresses. We found that 73 percent of the per ...
... from August 2003 and August 2004, and tried to account for DHCP effects. It’s possible that several infected hosts simply moved within the same LAN due to DHCP or other administrative decisions, so again we compared only the first 24 bits of the host IP addresses. We found that 73 percent of the per ...