Page | 1
... information technology and methods of transmitting information and data between local and global networks, there are some security gaps that can cause serious problems. This is a fact that can not be denied. For instance, according to Olzak (2007) NetBIOS (Network Basic Input Output System) is almos ...
... information technology and methods of transmitting information and data between local and global networks, there are some security gaps that can cause serious problems. This is a fact that can not be denied. For instance, according to Olzak (2007) NetBIOS (Network Basic Input Output System) is almos ...
Troubleshooting File and Printer Sharing in Microsoft Windows XP
... with other computers on a network. File sharing allows you to make files and folders in a shared folder accessible to others on the network to view, copy, or modify. For example, with file sharing, you can store all of your documents on a central computer and share the folder that contains them. The ...
... with other computers on a network. File sharing allows you to make files and folders in a shared folder accessible to others on the network to view, copy, or modify. For example, with file sharing, you can store all of your documents on a central computer and share the folder that contains them. The ...
Chapter 6 Powerpoint
... • Print provider works with print processor to ensure that file is formatted to use right data type • Print monitor pulls file from spooler’s disk storage and sends it to printer ...
... • Print provider works with print processor to ensure that file is formatted to use right data type • Print monitor pulls file from spooler’s disk storage and sends it to printer ...
ch06 - Seneca - School of Information & Communications
... • Print provider works with print processor to ensure that file is formatted to use right data type • Print monitor pulls file from spooler’s disk storage and sends it to printer ...
... • Print provider works with print processor to ensure that file is formatted to use right data type • Print monitor pulls file from spooler’s disk storage and sends it to printer ...
NetScreen-Remote VPN and Security Client Software
... secure, mobile access to private networks has caused network security administrators to place additional requirements on client software. Remote access clients must now provide secure authentication and VPN policy retrieval while remaining easy to deploy and seamless to end users. The software must ...
... secure, mobile access to private networks has caused network security administrators to place additional requirements on client software. Remote access clients must now provide secure authentication and VPN policy retrieval while remaining easy to deploy and seamless to end users. The software must ...
MCITP Guide to Microsoft Windows Server 2008 Server
... • Ensure IP parameters are correctly configured to provide an address pool for either a VPN or dial-up RAS server • If using a RADIUS server: – Ensure it is connected and working properly and that Internet Authentication Service (IAS) is installed ...
... • Ensure IP parameters are correctly configured to provide an address pool for either a VPN or dial-up RAS server • If using a RADIUS server: – Ensure it is connected and working properly and that Internet Authentication Service (IAS) is installed ...
01 - Quick Heal
... The most notable botnet incident of 2013 was the birth of the CryptoLocker. While PC users are becoming more and more aware of fake anti-virus and alerts, CryptoLocker took all by surprise. Delivered by botnets and devised to extort money by encrypting files and holding them on ransom, this ransomwa ...
... The most notable botnet incident of 2013 was the birth of the CryptoLocker. While PC users are becoming more and more aware of fake anti-virus and alerts, CryptoLocker took all by surprise. Delivered by botnets and devised to extort money by encrypting files and holding them on ransom, this ransomwa ...
Introduction to DNS in Windows Server 2008
... – DNS uses records to provide the information it stores in its database MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration ...
... – DNS uses records to provide the information it stores in its database MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration ...
Introduction to DNS in Windows Server 2008
... – DNS uses records to provide the information it stores in its database MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration ...
... – DNS uses records to provide the information it stores in its database MCTS Guide to Microsoft Windows Server 2008 Network Infrastructure Configuration ...
Managing and Administering DNS in Windows Server 2008
... • Administrators can choose one of the following zone replication options for AD DS DNS zones – To all DNS servers in this forest – To all DNS servers in this domain – To all domain controllers in this domain (for Windows 2000 compatibility) MCTS Guide to Microsoft Windows Server 2008 Network Infras ...
... • Administrators can choose one of the following zone replication options for AD DS DNS zones – To all DNS servers in this forest – To all DNS servers in this domain – To all domain controllers in this domain (for Windows 2000 compatibility) MCTS Guide to Microsoft Windows Server 2008 Network Infras ...
Chapter 6 Configuring, Monitoring & Troubleshooting IPsec
... •Request or require a valid computer certificate, requires at least one CA •Only accept health certificates: request or require a valid health certificate to authenticate, requires IPsec NAP ...
... •Request or require a valid computer certificate, requires at least one CA •Only accept health certificates: request or require a valid health certificate to authenticate, requires IPsec NAP ...
Hyper-v Health Check -Real World Scenario
... Validate the amount of snapshots being taken and the reason for the snapshot. Disable the feature on Client operating systems and enable the snapshot only for those servers which are high performance centric. Check for unused virtual machines that are not in use and decommission them. This can be do ...
... Validate the amount of snapshots being taken and the reason for the snapshot. Disable the feature on Client operating systems and enable the snapshot only for those servers which are high performance centric. Check for unused virtual machines that are not in use and decommission them. This can be do ...
SubVirt: Implementing malware with virtual machines
... By : F. Zahmatkesh University of Science and Technology of Mazandaran, Babol [email protected] December 24,2009 ...
... By : F. Zahmatkesh University of Science and Technology of Mazandaran, Babol [email protected] December 24,2009 ...
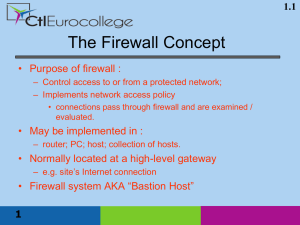
Firewall - theodoros christophides site
... Software-Only Packages • Many free firewall tools on the Internet – Some also run on a free operating system ...
... Software-Only Packages • Many free firewall tools on the Internet – Some also run on a free operating system ...
mypages.iit.edu
... • For organizations that enable users to access network resources through the Web – Rather than through user accounts ...
... • For organizations that enable users to access network resources through the Web – Rather than through user accounts ...
the catalogue here
... protection including: anti-malware, web reputation technology to block access to malicious websites, and HIPS protection. Powered by Trend Micro Smart Protection Network cloud-based security, pattern files are managed in the cloud and not on your endpoints to free computing resources and optimize pe ...
... protection including: anti-malware, web reputation technology to block access to malicious websites, and HIPS protection. Powered by Trend Micro Smart Protection Network cloud-based security, pattern files are managed in the cloud and not on your endpoints to free computing resources and optimize pe ...
Lab1Overview - ECE Users Pages
... Scanning tool: Nessus Purpose: “To provide to the internet community a free, powerful, up-to-date and easy to use remote security scanner.” Security Scanner: “A software which will audit remotely a given network and determine whether bad guys (aka 'crackers') may break into it, or misuse it in some ...
... Scanning tool: Nessus Purpose: “To provide to the internet community a free, powerful, up-to-date and easy to use remote security scanner.” Security Scanner: “A software which will audit remotely a given network and determine whether bad guys (aka 'crackers') may break into it, or misuse it in some ...
Chapter 4
... sequence of bits of data (serial transmission) • To redistribute serial data to parallel lines (and vice versa), one of the most important components on a NIC is memory, which acts as a buffer Guide to Networking Essentials, Fifth Edition ...
... sequence of bits of data (serial transmission) • To redistribute serial data to parallel lines (and vice versa), one of the most important components on a NIC is memory, which acts as a buffer Guide to Networking Essentials, Fifth Edition ...
Security Model for ASP.NET Web Applications: Authentication and
... servers against attacks. Microsoft Internet Information Services (IIS) administrators are aware of the past security holes in IIS and have spend a lot of time fixing them using the patches and security updates from Redmond. II. CLASSIFICATION OF WEBSITES We can categorized websites developed using A ...
... servers against attacks. Microsoft Internet Information Services (IIS) administrators are aware of the past security holes in IIS and have spend a lot of time fixing them using the patches and security updates from Redmond. II. CLASSIFICATION OF WEBSITES We can categorized websites developed using A ...
McAfee Database Security Solution Brief
... of threats: external, internal, and even intra-database exploits. This software-based solution provides robust security and continuous compliance without requiring architecture changes, costly hardware, or downtime. In other words, it’s an efficient, affordable way to protect databases while preserv ...
... of threats: external, internal, and even intra-database exploits. This software-based solution provides robust security and continuous compliance without requiring architecture changes, costly hardware, or downtime. In other words, it’s an efficient, affordable way to protect databases while preserv ...
Threats To Windows Users and Countermeasures
... 6.1 Broadband Internet Connection: DSL and Cable Modem Broadband technology such as DSL and cable modem connection has contributed to the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which ...
... 6.1 Broadband Internet Connection: DSL and Cable Modem Broadband technology such as DSL and cable modem connection has contributed to the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which ...
Chapter 10 Systems Management
... control over Windows 95 for users of differing capabilities or network privilege levels, including control of the user interface, network capabilities, desktop configuration, sharing capabilities, and so on. Like the other two Registry components, System Policies consist of pairs of keys and values. ...
... control over Windows 95 for users of differing capabilities or network privilege levels, including control of the user interface, network capabilities, desktop configuration, sharing capabilities, and so on. Like the other two Registry components, System Policies consist of pairs of keys and values. ...