ppt 2
... security status of the OS Security solutions like IDS (Intrusion Detection Systems) and firewalls can claim to carry out secure reinforcement • But internal vulnerabilities seriously impair the external effectiveness those solutions play • Still expose the whole system to malicious communities • The ...
... security status of the OS Security solutions like IDS (Intrusion Detection Systems) and firewalls can claim to carry out secure reinforcement • But internal vulnerabilities seriously impair the external effectiveness those solutions play • Still expose the whole system to malicious communities • The ...
Firewall
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
Security Considerations for Health Care Organizations
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
Introduction to Databases - Department of Software and Information
... DBMS and Web Security Internet communication relies on TCP/IP TCP/IP and HTTP not designed with security in mind Without special software, all Internet traffic travels ‘in the clear’ Anyone who monitors traffic can read it ...
... DBMS and Web Security Internet communication relies on TCP/IP TCP/IP and HTTP not designed with security in mind Without special software, all Internet traffic travels ‘in the clear’ Anyone who monitors traffic can read it ...
William Stallings, Cryptography and Network Security 3/e
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
The Need for Security
... Amit Yoran, former director of The Department of Homeland Security’s National Cyber Security Division “ only by improving the quality of our software and reducing the number of flaws can we hope to be successful in our security efforts” ...
... Amit Yoran, former director of The Department of Homeland Security’s National Cyber Security Division “ only by improving the quality of our software and reducing the number of flaws can we hope to be successful in our security efforts” ...
Computer Security Presentation
... Inc. found that 20% of home computers were infected by a virus or worm, and that various forms of snooping programs such as spyware and adware are on a whopping 80% of systems. Even so, more than two-thirds of home users think they are safe from online threats. [ComputerWorld, OCTOBER 25, 2004] “A z ...
... Inc. found that 20% of home computers were infected by a virus or worm, and that various forms of snooping programs such as spyware and adware are on a whopping 80% of systems. Even so, more than two-thirds of home users think they are safe from online threats. [ComputerWorld, OCTOBER 25, 2004] “A z ...
Access Control, Operations Security, and Computer Forensics
... • Provides access control for routers, network access servers and other networked computing devices via one or more centralized servers. • Provides separate authentication, authorization and accounting services. • Two factor Authentication • User can change password • Ability to use secure tokens • ...
... • Provides access control for routers, network access servers and other networked computing devices via one or more centralized servers. • Provides separate authentication, authorization and accounting services. • Two factor Authentication • User can change password • Ability to use secure tokens • ...
The most important program that runs on a computer
... at the same time do not interfere with each other. The operating system is also responsible for security, ensuring that unauthorized users do not access the system. Operating systems can be classified as follows: multi-user : Allows two or more users to run programs at the same time. Some operatin ...
... at the same time do not interfere with each other. The operating system is also responsible for security, ensuring that unauthorized users do not access the system. Operating systems can be classified as follows: multi-user : Allows two or more users to run programs at the same time. Some operatin ...
Chapter04
... 12. When a service is in _____ mode, it starts every time the computer is turned on. automatic 13. _____ mode allows Windows to start a service whenever it is needed. Manual 14. A service that has been set to _____ mode is not loaded, even if it is needed. Disable 15. Explain the differences between ...
... 12. When a service is in _____ mode, it starts every time the computer is turned on. automatic 13. _____ mode allows Windows to start a service whenever it is needed. Manual 14. A service that has been set to _____ mode is not loaded, even if it is needed. Disable 15. Explain the differences between ...
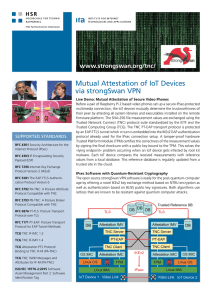
Mutual Attestation of IoT Devices via strongSwan VPN
... their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement values are exchanged using the Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport pr ...
... their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement values are exchanged using the Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport pr ...
Systems Administrator needed for DoD Griffin Cyberspace Defense
... Assigns personnel to various projects, directs their activities, and evaluates their work. Ensures long-term requirements of systems operations and administration are included in the overall information systems planning of the organization. Responsible for the installation, maintenance, configuratio ...
... Assigns personnel to various projects, directs their activities, and evaluates their work. Ensures long-term requirements of systems operations and administration are included in the overall information systems planning of the organization. Responsible for the installation, maintenance, configuratio ...
Chapter 5 Protecting Information Resources
... Programming routine built into a system by its designer or programmer Enables the designer or programmer to bypass system security and sneak back into the system later to access programs or files System users aren’t aware a backdoor has ...
... Programming routine built into a system by its designer or programmer Enables the designer or programmer to bypass system security and sneak back into the system later to access programs or files System users aren’t aware a backdoor has ...
Are you looking for an easier way to initiate and
... significant resources, such as organized crime or a rogue nation state. ...
... significant resources, such as organized crime or a rogue nation state. ...
Security
... (b) Login rejected after name entered (c) Login rejected after name and password typed ...
... (b) Login rejected after name entered (c) Login rejected after name and password typed ...
Microsoft Silverlight Catching Up To Adobe Flash
... Microsoft (MSFT) has been building out its Silverlight Web video/animation software with some success: While companies like Netflix (NFLX), CBS, and NBC have used it for big projects, it's still far behind Adobe's (ADBE) Flash in adoption and usage. But that doesn't mean Microsoft can't catch up: Th ...
... Microsoft (MSFT) has been building out its Silverlight Web video/animation software with some success: While companies like Netflix (NFLX), CBS, and NBC have used it for big projects, it's still far behind Adobe's (ADBE) Flash in adoption and usage. But that doesn't mean Microsoft can't catch up: Th ...
FAQ - CareLink
... pump model. Once the read is complete, please verify the pump has resumed delivery if it was suspended. If, for some reason, the pump does not resume delivery after the upload, the pump will beep or vibrate about every 15 minutes on the hour to remind you that it is not delivering insulin. o For add ...
... pump model. Once the read is complete, please verify the pump has resumed delivery if it was suspended. If, for some reason, the pump does not resume delivery after the upload, the pump will beep or vibrate about every 15 minutes on the hour to remind you that it is not delivering insulin. o For add ...
Introduction to Biometrics
... BioAPI for Java Card • Java Card: – Java Card technology provides a secure environment for applications that run on smart cards and other devices with very limited memory and processing capabilities. – Multiple applications can be deployed on a single card, and new ones can be added to it even afte ...
... BioAPI for Java Card • Java Card: – Java Card technology provides a secure environment for applications that run on smart cards and other devices with very limited memory and processing capabilities. – Multiple applications can be deployed on a single card, and new ones can be added to it even afte ...
View File
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
Cybersecurity - Queen`s Wiki
... • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in 2016. ...
... • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in 2016. ...
How does it get written up?
... Active attacks • Issues that are impacting Stanford and/or the rest of the Internet • Issues about which the security team is getting lots of questions • Issues that can be easily avoided by updating software or AV signatures ...
... Active attacks • Issues that are impacting Stanford and/or the rest of the Internet • Issues about which the security team is getting lots of questions • Issues that can be easily avoided by updating software or AV signatures ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... •System manages the IESO’s website content and files •Accesses over 35,000 pages of data in real -time ...
... •System manages the IESO’s website content and files •Accesses over 35,000 pages of data in real -time ...
Transparencies (updated, 10/28/98)
... officer directing traffic. This activity is performed by the supervisor, or kernel, the central component of the operating system. The supervisor, which manages the CPU, resides in main memory while the computer is on and directs other programs to perform tasks to support applications programs. Mana ...
... officer directing traffic. This activity is performed by the supervisor, or kernel, the central component of the operating system. The supervisor, which manages the CPU, resides in main memory while the computer is on and directs other programs to perform tasks to support applications programs. Mana ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.