Information Security and its Implications on Everyday
... t let Web browsers store passwords for you Don' t transmit passwords (or PINs) in unencrypted e-mail and Web forms. Assume that all PINs can be easily broken, and plan accordingly. ...
... t let Web browsers store passwords for you Don' t transmit passwords (or PINs) in unencrypted e-mail and Web forms. Assume that all PINs can be easily broken, and plan accordingly. ...
Shawn Bracken - CISSP103 Chester StMenlo Park, CA 94025
... Conducted peer reviews of advisories and white papers from other team members Served as a security resource within the organization 1998 to 1999, Network Security Consultant, International Network Services, Sacramento, CA Delivered consultative services to Fortune 500 companies ...
... Conducted peer reviews of advisories and white papers from other team members Served as a security resource within the organization 1998 to 1999, Network Security Consultant, International Network Services, Sacramento, CA Delivered consultative services to Fortune 500 companies ...
Fundamentals of Computer Security
... perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among them are ...
... perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among them are ...
Resume - Training Directory Mena
... Install and configure Active Directory on windows Server 2003, 2008 and 2012 Install and configure DNS, DHCP. WSUS, WDS, GPOs, VPN, Terminal Services, Print Server and File Server. Managing and configuring Hyper-V. Install and configure Exchange 2013. Install and configure an SCCM 2012 Sever. Managi ...
... Install and configure Active Directory on windows Server 2003, 2008 and 2012 Install and configure DNS, DHCP. WSUS, WDS, GPOs, VPN, Terminal Services, Print Server and File Server. Managing and configuring Hyper-V. Install and configure Exchange 2013. Install and configure an SCCM 2012 Sever. Managi ...
Lakshmi Nannapaneni`s presentation on Patterns for Secure Boot
... succeeded can access the protected data. Data can be stored on a system, such that it can be accessed only when the authorized operating system and software has been started. ...
... succeeded can access the protected data. Data can be stored on a system, such that it can be accessed only when the authorized operating system and software has been started. ...
Module 2
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
CompTIA Strata™ Fundamentals of IT Technology
... maintenance of computers. This test is intended for candidates completing their “secondary” education, considering the pursuit of a CompTIA A+ certification, and/or advanced home users who wish to further their IT knowledge. Domain ...
... maintenance of computers. This test is intended for candidates completing their “secondary” education, considering the pursuit of a CompTIA A+ certification, and/or advanced home users who wish to further their IT knowledge. Domain ...
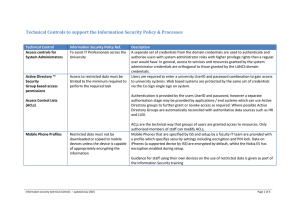
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
Event Title - Microsoft Center
... Notes: Update as of 1/13/2010. Vulnerabilities are included for SQL Server 2000 , SQL Server 2005 , SQL Server 2008. Oracle (8i, 9i, 9iR2, 10g, 10gR2,11g), IBM DB2 (8.0, 8.1, 8.2, 9.0, 9.5), Query for Oracle was run with vendor name: ‘Oracle’ , and product name: ‘any’ (all database product name va ...
... Notes: Update as of 1/13/2010. Vulnerabilities are included for SQL Server 2000 , SQL Server 2005 , SQL Server 2008. Oracle (8i, 9i, 9iR2, 10g, 10gR2,11g), IBM DB2 (8.0, 8.1, 8.2, 9.0, 9.5), Query for Oracle was run with vendor name: ‘Oracle’ , and product name: ‘any’ (all database product name va ...
Think Global, Work Local, FAST™
... √ Distributed locations connect to traditional or cloud datacenter via the Talon FAST™ Fabric √ Software provides a Virtual File Share and Intelligent File Cache at each location √ Enables high performance global file sharing with real-time distributed file locking The software overlays the Microsof ...
... √ Distributed locations connect to traditional or cloud datacenter via the Talon FAST™ Fabric √ Software provides a Virtual File Share and Intelligent File Cache at each location √ Enables high performance global file sharing with real-time distributed file locking The software overlays the Microsof ...
Proposal Presentation. - Computer Science
... database products, their adoption might be a little difficult. They are performed on specific hardware platform and operating system. They simulate real world workload that might not reflect the actual workload of a specific organisation database system. Some vendors use techniques such as caching t ...
... database products, their adoption might be a little difficult. They are performed on specific hardware platform and operating system. They simulate real world workload that might not reflect the actual workload of a specific organisation database system. Some vendors use techniques such as caching t ...
Sentinel SuperPro™
... SuperPro provides protection against technologies that can enable users to cheat their licensing agreements through virtualization. For example, USB or parallel port sharing devices as well as virtualization products in which multiple instances of your application attempt to directly access one dong ...
... SuperPro provides protection against technologies that can enable users to cheat their licensing agreements through virtualization. For example, USB or parallel port sharing devices as well as virtualization products in which multiple instances of your application attempt to directly access one dong ...
Security Considerations for RemotelyAnywhere
... System administrators can configure RemotelyAnywhere so that users with certain roles have access only to a subset of tools offered by RemotelyAnywhere; for example, the Helpdesk department can be configured to only view a computer’s screen and performance data, but not actually take over the mouse ...
... System administrators can configure RemotelyAnywhere so that users with certain roles have access only to a subset of tools offered by RemotelyAnywhere; for example, the Helpdesk department can be configured to only view a computer’s screen and performance data, but not actually take over the mouse ...
secure operating system
... A secure operating system is an operating system where its access enforcement satisfies the reference monitor concept The reference monitor concept defines the necessary and sufficient properties of any system that securely enforces a mandatory protection system, consisting of three guarantees: 1. C ...
... A secure operating system is an operating system where its access enforcement satisfies the reference monitor concept The reference monitor concept defines the necessary and sufficient properties of any system that securely enforces a mandatory protection system, consisting of three guarantees: 1. C ...
Resume - my name is chris tran
... Highly responsible, passionate and organised enabling efficient performance in team projects and delivering the best outcome within given timelines. Excellent attitude towards work and possess a strong willingness to learn and maintain currency with Information ...
... Highly responsible, passionate and organised enabling efficient performance in team projects and delivering the best outcome within given timelines. Excellent attitude towards work and possess a strong willingness to learn and maintain currency with Information ...
Example: Data Mining for the NBA - The University of Texas at Dallas
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
How can the SMART card help in new channels?
... accompanying software to be loaded • Generated by Trusted third party called: Multos Key Management Authority: KMA • Card will only load or delete application if ALC is valid ...
... accompanying software to be loaded • Generated by Trusted third party called: Multos Key Management Authority: KMA • Card will only load or delete application if ALC is valid ...
Sujoy Sinha Roy - Cyber Security at IIT Kanpur
... Homomorphic encryption enables computation on encrypted data. One application of homomorphic encryption is private cloud computing: a user uploads her encrypted data in the cloud and then computes on the encrypted data. The ring-LWE problem has been used to construct homomorphic encryption schemes. ...
... Homomorphic encryption enables computation on encrypted data. One application of homomorphic encryption is private cloud computing: a user uploads her encrypted data in the cloud and then computes on the encrypted data. The ring-LWE problem has been used to construct homomorphic encryption schemes. ...
Information Assurance Presentation
... systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely erase their tracks within 20 minutes. OCTOBER 20, 2005 (COMPUTERWORLD) ...
... systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely erase their tracks within 20 minutes. OCTOBER 20, 2005 (COMPUTERWORLD) ...
Chapter 10: Electronic Commerce Security
... What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and authentication? Discuss the role of administration in implementing a security ...
... What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and authentication? Discuss the role of administration in implementing a security ...
10 March 2009 - Computer Science
... encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. Provide some analysis on data that may be useful for detection of possible attacks or for debugging purposes. Initially pr ...
... encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. Provide some analysis on data that may be useful for detection of possible attacks or for debugging purposes. Initially pr ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.