Social Studies
... Use accurate terminology related to technology. Use appropriate terminology related to technology. Use standard multi-media features of presentation software. Use standard multimedia capabilities. For example: the insertion of sound files, pictures/graphics, movie files, hyperlinks, animation, actio ...
... Use accurate terminology related to technology. Use appropriate terminology related to technology. Use standard multi-media features of presentation software. Use standard multimedia capabilities. For example: the insertion of sound files, pictures/graphics, movie files, hyperlinks, animation, actio ...
JRA1.4 AAs in eduGAIN
... ● Permit delegation of the management of user information in a clear and secure way. ● Provide new architectural elements that could seamlessly integrate with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing ...
... ● Permit delegation of the management of user information in a clear and secure way. ● Provide new architectural elements that could seamlessly integrate with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing ...
Overview of Operating Systems Security Features
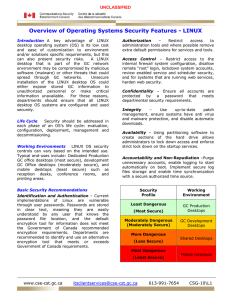
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
Job Title: User Applications Specialist Job Summary A User
... of hardware and software that is typically used in office environments for data management and/or web communication. This is a non-exempt position requiring an intermediate level of knowledge that is typically obtained through work experience and either specific vocational training (e.g., Microsoft ...
... of hardware and software that is typically used in office environments for data management and/or web communication. This is a non-exempt position requiring an intermediate level of knowledge that is typically obtained through work experience and either specific vocational training (e.g., Microsoft ...
Module F - Columbus State University
... Modules (TPM) chips, a hardware-based security scheme that stores cryptographic keys, passwords, and digital certificates on the motherboard. A driver has been introduced to support the embedding of security measures in hardware, including TPM devices from National Semiconductor and Atmel. Also, enh ...
... Modules (TPM) chips, a hardware-based security scheme that stores cryptographic keys, passwords, and digital certificates on the motherboard. A driver has been introduced to support the embedding of security measures in hardware, including TPM devices from National Semiconductor and Atmel. Also, enh ...
Document
... Announcement: July 7, 2009 Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
... Announcement: July 7, 2009 Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
Presentation on Security Flaws in Windows XP
... system tracks privileges associated with each user and application Applications not needing extensive permissions usually run with privileges of the current request. Installing as administrator have access to more privileges needed ...
... system tracks privileges associated with each user and application Applications not needing extensive permissions usually run with privileges of the current request. Installing as administrator have access to more privileges needed ...
Design and Implementation of Security Operating System based on
... IBLP. The overall design scheme and modularized implementation of a secure system for trusted computing. Experiment result to show effectiveness and feasibility of their system. ...
... IBLP. The overall design scheme and modularized implementation of a secure system for trusted computing. Experiment result to show effectiveness and feasibility of their system. ...
Slide 1
... Handling the memory resources for running applications. Virtual memory – the presentation of more memory to applications than is available by using disk. Paging – a block of continuous memory of a predetermined size Page faults – occurs when an application accesses a page that has been virtualized t ...
... Handling the memory resources for running applications. Virtual memory – the presentation of more memory to applications than is available by using disk. Paging – a block of continuous memory of a predetermined size Page faults – occurs when an application accesses a page that has been virtualized t ...
Final bits of OS - Department of Computer Science
... • events that are collected for use by the various security detection and prevention mechanisms • events related to system management and operation • operating system access • application access for selected applications • remote access ...
... • events that are collected for use by the various security detection and prevention mechanisms • events related to system management and operation • operating system access • application access for selected applications • remote access ...
CPM Supported Device - Inter
... Supporting Additional Systems and Devices Cyber-Ark’s Privileged Identity Management (PIM) Suite is designed and developed using an extensible architecture approach, which provides great flexibility to dynamically support additional managed devices. Cyber-Ark constantly releases CPM plug-ins for new ...
... Supporting Additional Systems and Devices Cyber-Ark’s Privileged Identity Management (PIM) Suite is designed and developed using an extensible architecture approach, which provides great flexibility to dynamically support additional managed devices. Cyber-Ark constantly releases CPM plug-ins for new ...
Trend Problem Vista/WS08 Impact
... • Microsoft: Validation of algorithms on Large Network Emulator on real satellite network as part of JWID 05 Microsoft for managing • Framework IP: Facilitates free flow of ideas and testing results ...
... • Microsoft: Validation of algorithms on Large Network Emulator on real satellite network as part of JWID 05 Microsoft for managing • Framework IP: Facilitates free flow of ideas and testing results ...
- Longwood Blogs
... Respond to user requests within specified on-call time periods Assist with network, printer, computer, and peripheral configuration Remove virus, malware, and perform maintenance on various operating systems Train students on safe and secure computer usage Develop and update Longwood’s net ...
... Respond to user requests within specified on-call time periods Assist with network, printer, computer, and peripheral configuration Remove virus, malware, and perform maintenance on various operating systems Train students on safe and secure computer usage Develop and update Longwood’s net ...
Drive pervasive business performance
... Office Performance Point Server to integrate scorecarding, analysis and planning Integrated workflow for simpler consolidation and reporting Common model for planning used in analysis ...
... Office Performance Point Server to integrate scorecarding, analysis and planning Integrated workflow for simpler consolidation and reporting Common model for planning used in analysis ...
Slide 1
... other organization that are not made available to the public. Thus, Cloud Computing is the sum of SaaS and Utility Computing, but does not normally include Private Clouds. ...
... other organization that are not made available to the public. Thus, Cloud Computing is the sum of SaaS and Utility Computing, but does not normally include Private Clouds. ...
Linux and Unix Administrator
... The Linux/Unix Administrator is responsible for Unix (e.g. Sun F15000 and smaller) or Linux environments, as well as the operating system software and its successful integration with the hardware and applications software of the major computing systems across the organization. Tasks of the Linux/Uni ...
... The Linux/Unix Administrator is responsible for Unix (e.g. Sun F15000 and smaller) or Linux environments, as well as the operating system software and its successful integration with the hardware and applications software of the major computing systems across the organization. Tasks of the Linux/Uni ...
CH 8 – Review - WordPress.com
... what does silverman consider to be the weak link in the computer security chain – people allowing hackers to access their machines what does silverman think could be the solution for computer security problems – people getting better educated about computer security according to silverman, why is Ma ...
... what does silverman consider to be the weak link in the computer security chain – people allowing hackers to access their machines what does silverman think could be the solution for computer security problems – people getting better educated about computer security according to silverman, why is Ma ...
slide 2 - Software
... • A single-user operating System is a type of operating system (OS) that is developed and intended for use on a computer or similar machine that will only have a single user at any given time. ...
... • A single-user operating System is a type of operating system (OS) that is developed and intended for use on a computer or similar machine that will only have a single user at any given time. ...
ROOTKIT VIRUS
... systems and the word ‘kit’, which refers to the software components that implement the tool. ...
... systems and the word ‘kit’, which refers to the software components that implement the tool. ...
Lecture 3.1 - Host
... defense based in cryptography. In this lecture we begin another layer. host-level security. Host-level security is about the software that executes on user’s machines, often connected to a network. Host-level security must focus especially on operating systems, because operating systems for two reas ...
... defense based in cryptography. In this lecture we begin another layer. host-level security. Host-level security is about the software that executes on user’s machines, often connected to a network. Host-level security must focus especially on operating systems, because operating systems for two reas ...
DBMS RESEARCH Are We On The Right Tracks?
... – Multi-Billion dollar industry – How can you argue with success? ...
... – Multi-Billion dollar industry – How can you argue with success? ...
IT Security, SQL Server and You!
... by granting access to a single user. The user will not cooperate with you. What actions would you take to access the data? ...
... by granting access to a single user. The user will not cooperate with you. What actions would you take to access the data? ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.