Enhanced Security Models for Operating Systems: A Cryptographic
... Escrow vaults: It is similar to GPRIV vault. It is used to hold keys for protected objects such that they can be retrieved if required by the Security administrator. Fundamental Vaults: The fundamental vaults are used to hold the keys for encrypting the other four vaults. ...
... Escrow vaults: It is similar to GPRIV vault. It is used to hold keys for protected objects such that they can be retrieved if required by the Security administrator. Fundamental Vaults: The fundamental vaults are used to hold the keys for encrypting the other four vaults. ...
Operating System Security Fundamentals
... Suppose you are the security manger for a small high-tech company. Outline security measures that you would implement to protect the operating system containing code for a new product innovation. Everyone research on this topic and prepare a 5-minute presentation with 10-page slides in the next meet ...
... Suppose you are the security manger for a small high-tech company. Outline security measures that you would implement to protect the operating system containing code for a new product innovation. Everyone research on this topic and prepare a 5-minute presentation with 10-page slides in the next meet ...
Access Control, Operations Security, and Computer Forensics
... Separation of Duties • Assign different tasks to different personnel • No single person can completely compromise a system • Related to the concept of least privileges – least privileges required to do one’s job • Secure Systems - System Administrator and Security Administrator must be different ro ...
... Separation of Duties • Assign different tasks to different personnel • No single person can completely compromise a system • Related to the concept of least privileges – least privileges required to do one’s job • Secure Systems - System Administrator and Security Administrator must be different ro ...
Security, Authorization, and Authentication for Enterprise Computing
... Mobile aglet security is progressing with the use of the Java sandbox mechanism and separate execution environments. Java security mechanisms such as cryptography and authentication are also be investigated to ensure security of both the aglet and the messages transported between aglets. Aglets offe ...
... Mobile aglet security is progressing with the use of the Java sandbox mechanism and separate execution environments. Java security mechanisms such as cryptography and authentication are also be investigated to ensure security of both the aglet and the messages transported between aglets. Aglets offe ...
BitLocker Drive Encryption Self
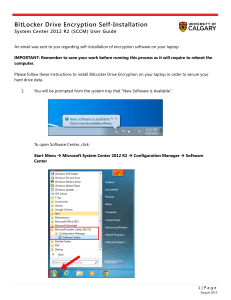
... IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive Encryption on your laptop in order to secure your hard drive data. ...
... IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive Encryption on your laptop in order to secure your hard drive data. ...
Hands-On Ethical Hacking and Network Security
... Best way to protect a network from SMB attacks ...
... Best way to protect a network from SMB attacks ...
Orange Book Summary - UMBC Center for Information Security and
... Object protection can be on a single-user basis, e.g. through an ACL or Trustee database. Authorisation for access may only be assigned by authorised users. Object reuse protection (i.e. to avoid reallocation of secure deleted objects). Mandatory identification and authorisation procedures for users ...
... Object protection can be on a single-user basis, e.g. through an ACL or Trustee database. Authorisation for access may only be assigned by authorised users. Object reuse protection (i.e. to avoid reallocation of secure deleted objects). Mandatory identification and authorisation procedures for users ...
Mark Boyer - Methods of securing data in window networks
... The process of securing data in windows networks is a very important task, especially if you are involved with a company or business. The loss or theft of data from a top secret sector of a company could be catastrophic. Items such as people’s personal files, bank account information, and things of ...
... The process of securing data in windows networks is a very important task, especially if you are involved with a company or business. The loss or theft of data from a top secret sector of a company could be catastrophic. Items such as people’s personal files, bank account information, and things of ...
Quality Attributes of Web Software Applications – Jeff Offutt
... Quality Attributes of Web Software Applications – Jeff Offutt By Julia Erdman SE 510 October 8, 2003 ...
... Quality Attributes of Web Software Applications – Jeff Offutt By Julia Erdman SE 510 October 8, 2003 ...
Orange
... You can get further information on the Orange Book and Rainbow Series by looking at the Orange Book Links page. Example Operating System descriptions link to the NCSC Evaluated Products List. The DoD security categories range from D (Minimal Protection) to A (Verified ...
... You can get further information on the Orange Book and Rainbow Series by looking at the Orange Book Links page. Example Operating System descriptions link to the NCSC Evaluated Products List. The DoD security categories range from D (Minimal Protection) to A (Verified ...
Chapter 05
... Information Flow: describe how information can flow. ◦ Bell-LaPadula and Biba use this. Chinese Wall (Brewer-Nash):avoid conflicts of interest. (consultant control) ◦ Prohibit access to conflict of interest categories. Noninterference: data at different security domains remain ...
... Information Flow: describe how information can flow. ◦ Bell-LaPadula and Biba use this. Chinese Wall (Brewer-Nash):avoid conflicts of interest. (consultant control) ◦ Prohibit access to conflict of interest categories. Noninterference: data at different security domains remain ...
operating system
... Operating systems can be classified as follows: multi-user : Allows two or more users to use system resources at the same time. Some operating systems permit hundreds or even thousands of concurrent users. multitasking : Allows more than one program to run concurrently. single user, single task :is ...
... Operating systems can be classified as follows: multi-user : Allows two or more users to use system resources at the same time. Some operating systems permit hundreds or even thousands of concurrent users. multitasking : Allows more than one program to run concurrently. single user, single task :is ...
Chapter 5 - Department of Computer Science and Information Systems
... A security policy is a written statement describing which assets to protect and why they are being protected, who is responsible for that protection, and which behaviors are acceptable and which are not The first step an organization must take in creating a security policy is to determine what asset ...
... A security policy is a written statement describing which assets to protect and why they are being protected, who is responsible for that protection, and which behaviors are acceptable and which are not The first step an organization must take in creating a security policy is to determine what asset ...
Security - UTRGV Faculty Web
... When a digital signature is encrypted using a private key – it can be read by anyone with a public key. But the message was sent by only one who has the private key. Digital certificates are used to authenticate the source of a file. ...
... When a digital signature is encrypted using a private key – it can be read by anyone with a public key. But the message was sent by only one who has the private key. Digital certificates are used to authenticate the source of a file. ...
Securing Mission- Critical Mobile Devices and Data
... sources. This is particularly useful for bring your own device (BYOD) programs should a mobile device be lost, since enterprise data can be wiped without affecting the user’s personal data. ...
... sources. This is particularly useful for bring your own device (BYOD) programs should a mobile device be lost, since enterprise data can be wiped without affecting the user’s personal data. ...
Computer Science or Software Engineering?
... Nearly three out of four new science or engineering jobs in the United States will be in computing, according to the Bureau of Labor Statistics. But what kind of computing job is right for you? If you are interested in majoring in either computer science or software engineering but do not know which ...
... Nearly three out of four new science or engineering jobs in the United States will be in computing, according to the Bureau of Labor Statistics. But what kind of computing job is right for you? If you are interested in majoring in either computer science or software engineering but do not know which ...
Current Issues in Maintaining a Secure System
... firewalls and spyware to help protect your computer from hackers. • To explain other terms frequently used with system security and examples of how they fit into the big picture. ...
... firewalls and spyware to help protect your computer from hackers. • To explain other terms frequently used with system security and examples of how they fit into the big picture. ...
draft - Union College
... [This document will be given to those faculty members who are having their computers replaced by ITS. It can also be posted on the campus website and distributed by other means.] Commitment and rationale Union College is committed to providing each faculty member, staff member and administrator with ...
... [This document will be given to those faculty members who are having their computers replaced by ITS. It can also be posted on the campus website and distributed by other means.] Commitment and rationale Union College is committed to providing each faculty member, staff member and administrator with ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
A Technical Introduction to NGSCB Security Summit East 2003
... NGSCB Features All NGSCB-enabled application capabilities build off of four key features (the pillars!) Strong process isolation Sealed storage Secure path Attestation ...
... NGSCB Features All NGSCB-enabled application capabilities build off of four key features (the pillars!) Strong process isolation Sealed storage Secure path Attestation ...
E-Surveillance and User Privacy
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.