* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 5 - Department of Computer Science and Information Systems
Web of trust wikipedia , lookup
Trusted Computing wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cryptography wikipedia , lookup
Cross-site scripting wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Digital signature wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Wireless security wikipedia , lookup
Unix security wikipedia , lookup
Content-control software wikipedia , lookup
Security-focused operating system wikipedia , lookup
Distributed firewall wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
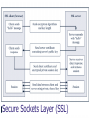
Security Threats and Protection Mechanisms Learning Objectives Internet security issues (intellectual property rights, client, communication channels, servers) Specific security objectives for protecting Web business assets and customer privacy How to protect: clients, data in transit, server computers. Organizations that promote computer, network, and Internet security Security Overview Computer security is the protection of assets from unauthorized access, use, alteration, or destruction Two types of security: • • Physical security Logical security Vocabulary: Any act or object that poses a danger to computer assets is known as a threat Countermeasure is a procedure that recognizes, reduces, or eliminates a threat An eavesdropper is a person or device that can listen in on and copy Internet transmissions Aspects of Security Three computer security categories: • • • Secrecy Integrity Availability Secrecy refers to protecting against unauthorized data disclosure and ensuring the authenticity of the data’s source Integrity refers to preventing unauthorized data modification Necessity refers to preventing data delays or denials Risk Management The risk management model shows four general actions to take according to the severity of a threat Security Policy A security policy is a written statement describing which assets to protect and why they are being protected, who is responsible for that protection, and which behaviors are acceptable and which are not The first step an organization must take in creating a security policy is to determine what assets to protect and from whom Specific elements of a security policy address the following points: • • • • Authentication and access control Secrecy and data integrity Audit Procedures Security elements in e-commerce There are three elements in e-commerce transactions • • • • • Client Communication channel Server Each element must be protected Each element has its own requirements and special characteristics Threats to the Client Active web content, i.e. non-static pages which contain instructions which execute in the client (for example: ActiveX, Java Applets, JavaScript, other plug-ins) Systems software bugs (e.g. Microsoft RPC bugs have allowed the proliferation of the Blaster worm) Software application bugs (e.g. Microsoft Outlook bugs can be exploited by viruses) Result: Unauthorized access or control of the client ActiveX Controls ActiveX is an object that contains programs and properties that Web designers place on Web pages to perform particular tasks ActiveX controls run only on computers running Windows and only on browsers that support them Because ActiveX controls have full access to client computers they can cause secrecy, integrity, or necessity violations Java Applets Java adds functionality to business applications and can handle transactions and a wide variety of actions on the client computer The Java sandbox confines Java applet actions to a set of rules defined by the security model These rules apply to all untrusted Java applets Bugs in the Java VM can cause security compromises JavaScript JavaScript is a scripting language that enables Web page designers to build active content Errors in JavaScript implementations can invoke privacy and integrity attacks JavaScript programs do not operate under the restrictions of the Java sandbox security model Other Active Content Plug-ins are programs that interpret or execute instructions embedded in downloaded graphics, sounds, and other objects Popular plug-ins include Macromedia Flash, Microsoft Media Player and Apple Quicktime. Active content, including all forms, enables Web pages to take action Plug-ins perform their duties by executing commands buried within the media they are manipulating Although active content gives life to static Web pages it also introduces unique challenges for protecting the client Viruses A virus is software that attaches itself to another file and can executes when host program is activated thus bypassing normal authorization controls E.g. a MS Word macro virus is coded as a small program and is embedded in a Word document Viruses can take any number of actions e.g. email everyone in the address book or make phone calls Viruses often use application software bugs Client compromises Clients can be compromised by exploiting system software bugs to take over computers A Trojan horse is a program hidden inside another program or Web page that masks its true purpose A worm is a program that has the instructions to look for and capture other computers on the net after infecting one A zombie is a program that secretly takes over another computer for the purpose of launching attacks on other computers Threats to the Communication Channel The Internet is the medium over which ecommerce data is transferred Messages on the Internet travel a random path from a source node to a destination node The content of messages is not protected and anyone on the message path can record its contents If communication is sensitive additional measures must be taken to protect the data This is a core requirement for e-commerce Specific Threats Secrecy Integrity Capture user identity preferences or record their activities Capture transaction details Capture payment information modify transactions modify user credential (e.g. delivery address) Availability make shop unavailable to customers Threats to the Server Servers have software vulnerabilities that can be exploited to cause destruction or to acquire information illegally E.g. databases connected to the Web contain information that could damage a company if it were disclosed or altered Physical security and access control is also very important Threats to Intellectual Property Intellectual property is the ownership of ideas and control over the tangible or virtual representation of those ideas IP includes: Names, for example trademarks and domain names (Cybersquatting, name changing, name stealing) Digital intellectual property, including art, logos, and music posted on Web sites, is protected by laws Computer Security Resources CERT SANS Institute Internet Storm Center Center for Internet Security U.S. Dept. of Justice Cybercrime National Infrastructure Protection Center Protecting Electronic Commerce Assets Monitoring Active Content Most browsers are equipped to recognize when they are about to download Web page containing active content Users can configure the user of active content by their browser For example, configure Java VM using the Java security console Microsoft Internet Explorer Microsoft Internet Explorer Netscape Navigator Netscape Navigator Antivirus Software Antivirus software is a defense strategy Antivirus software matches the contents of a file under examination against a database of virus “signatures” Thus, antivirus software cannot protect against viruses that have not been discovered earlier and recorded in the database One of the most likely places to find a virus is in an electronic mail attachment Some Web e-mail systems let users scan attachments using antivirus software before downloading e-mail Protecting e-commerce communications Providing e-commerce channel security means: • • • • Providing channel secrecy Guaranteeing message integrity Ensuring channel availability A complete security plan includes authentication Businesses must prevent eavesdroppers from reading the Internet messages that they intercept Best available way to do this is via encryption Encryption Encryption is a mathematical technique which encodes information using a key to transform the original information into a string of characters that is unintelligible The program that transforms text into cipher text is called an encryption program At the other end of the communication channel each message is decrypted using the same or a related key by a decryption program Types of Encryption Asymmetric encryption or public-key encryption, encodes messages by using two mathematically related numeric keys: a public key and a private key Symmetric encryption or private-key encryption, encodes a message using a single numeric key to encode and decode data Hash Functions Hash algorithms are one-way functions. A hash algorithm has these characteristics: • • • • It uses no secret key The message digest it produces cannot be inverted to produce the original information The algorithm and information about how it works are publicly available Hash collisions are nearly impossible. MD5 is an example of a hash algorithm Encryption Methods Encryption Algorithms and Standards Secure Sockets Layer (SSL) Digital Certificates A digital certificate verifies that a user or Web site is who it claims to be The digital certificate contains a means for sending an encrypted message to the entity A Web site’s digital certificate is a shopper’s assurance that the Web site is the real store Proof of validity and management of digital certificates is provided by the certification authority Digital Certificates in IE Ensuring Transaction Integrity Integrity violations can occur whenever a message is altered while in transit between the sender and receiver Ensuring transaction integrity, two separate algorithms are applied to a message: • • Hash function Digital signature Digital Signature An encrypted message digest is called a digital signature A purchase order accompanied by the digital signature provides the merchant positive identification of the sender and assures the merchant that the message was not altered Used together, public-key encryption, message digests, and digital signatures provide quality security for Internet transactions Transaction Delivery A denial or delay of service attack removes or absorbs resources One way to deny service is to flood the server with a large number of packets To prevent such attacks, a robust network architecture should be in place and network countermeasures should be in place Protecting the Web Server The e-commerce server which incorporates a Web server, responds to requests from Web browsers through the HTTP protocol and CGI scripts Security measures for commerce servers: • Access control and authentication • Operating system controls • Firewall Access Control and Authentication Access control and authentication refers to controlling who and what has access to the ecommerce server Operating systems often provide access control list security to restrict file access to selected users Users identify themselves using either a password or a token An access control list (ACL) is a list or database of people who can access the files and resources Firewalls A firewall is a system that is installed at the entry point of a network The firewall provides the first line of defense between a network and the Internet or other network that could pose a threat Acting as a filter, firewalls permit selected messages to flow into and out of the protected network Types of Firewalls Packet-filter firewalls examine all the data flowing back and forth between the trusted network Application layer firewalls filter traffic based on the application they request Proxy severs are firewalls that communicate with the Internet on the private network’s behalf IP Protection A watermark is data imperceptibly added to the original digital asset in order to convey hidden copyright data A watermark can be used to verify the lawful use of the asset It should not reduce the quality of the digital asset Still in its infancy as a market Other techniques (less powerful) are based on mechanisms built-in the hardware or the software Examples include DVD and MS Media Player but more often than not can be bypassed