The Trust Paradox
... Appendix – collection and selection of data ...................................................................... 312 Bibliography ...................................................................................................................... 321 ...
... Appendix – collection and selection of data ...................................................................... 312 Bibliography ...................................................................................................................... 321 ...
Trust as a Decision. The Problems and Functions of Trust in
... A journey, rewarding but sometimes tough, is about to finish. This journey can be divided into four periods. Because of the death of my loving father, the first period from 2000 to 2001 was the most painful time in my life and it was often more than difficult to concentrate on doing research. After ...
... A journey, rewarding but sometimes tough, is about to finish. This journey can be divided into four periods. Because of the death of my loving father, the first period from 2000 to 2001 was the most painful time in my life and it was often more than difficult to concentrate on doing research. After ...
IPsec – An Introduction
... If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
... If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
CIFE Modeling & Monitoring Trust in Virtual A/E/C Teams
... This research proposes to develop and test processes, criteria, language, concepts, models and tools that can be used by managers and workers to design, build, maintain, and repair trust in virtual teams. With the trend toward globalization, information technology and E-Comme rce services, Architect ...
... This research proposes to develop and test processes, criteria, language, concepts, models and tools that can be used by managers and workers to design, build, maintain, and repair trust in virtual teams. With the trend toward globalization, information technology and E-Comme rce services, Architect ...
Chapter16-PresentationDistilled
... against scenarios that attempt to break the final system. It can also include penetration testing where the company attempts to break into their own systems to find vulnerabilities as if they were hackers. Whereas normal testing focuses on passing user requirements, security testing focuses on survi ...
... against scenarios that attempt to break the final system. It can also include penetration testing where the company attempts to break into their own systems to find vulnerabilities as if they were hackers. Whereas normal testing focuses on passing user requirements, security testing focuses on survi ...
DNS Security Considerations and the Alternatives to BIND
... (Authoritative for Zone, the SOA), and Resolving Name Servers (resolver, caching, or to answer recursion DNS queries) [7]. In the presentation “Securing an Internet Name Server” by Cricket Liu (http://www.verisigngrs.com/dns/securing_an_internet_name_server.pdf), he has demonstrated the splitservice ...
... (Authoritative for Zone, the SOA), and Resolving Name Servers (resolver, caching, or to answer recursion DNS queries) [7]. In the presentation “Securing an Internet Name Server” by Cricket Liu (http://www.verisigngrs.com/dns/securing_an_internet_name_server.pdf), he has demonstrated the splitservice ...
EE579T-Class 4
... security. How would you use private key crypto to distribute public keys? 4. Refer to Figure 10.5 of the text. Describe the passage of a packet from machine 192.168.1.23 to 192.168.3.3. Be specific as to what happens at boundaries. Spring 2001 © 2000, 2001, Richard A. Stanley ...
... security. How would you use private key crypto to distribute public keys? 4. Refer to Figure 10.5 of the text. Describe the passage of a packet from machine 192.168.1.23 to 192.168.3.3. Be specific as to what happens at boundaries. Spring 2001 © 2000, 2001, Richard A. Stanley ...
Elite Integration and Institutional Trust in Norway - DUO
... more comfortable with others having similar belief systems. Similar groups are assessed more favourably than dissimilar ones. This theory has been developed for explaining the prejudice and stereotype majorities hold about minorities. Delhey and Newton (2005) argue that this theory can be transferre ...
... more comfortable with others having similar belief systems. Similar groups are assessed more favourably than dissimilar ones. This theory has been developed for explaining the prejudice and stereotype majorities hold about minorities. Delhey and Newton (2005) argue that this theory can be transferre ...
slides [pdf]
... user or a concurrent application) can access or manipulate the code or the data of the application (which is similar to overwriting S0). This requirement ensures that the code and the data of the TAS are protected against attacks of concurrent processes.” 2. “Secure Path: The TCB has to provide a se ...
... user or a concurrent application) can access or manipulate the code or the data of the application (which is similar to overwriting S0). This requirement ensures that the code and the data of the TAS are protected against attacks of concurrent processes.” 2. “Secure Path: The TCB has to provide a se ...
LifeCare PCA Infusion System With Hospira MedNet Software
... The only time an infusion can be administered with the door unlocked is when an initial or supplemental Loading Dose has been started. With the LifeCare PCA® device a clinician has the option to program and administer the initial loading dose before completing the remainder of the programming, or de ...
... The only time an infusion can be administered with the door unlocked is when an initial or supplemental Loading Dose has been started. With the LifeCare PCA® device a clinician has the option to program and administer the initial loading dose before completing the remainder of the programming, or de ...
Slide 1
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
The Real Cost of Free Programs such as Instant
... The most common file sharing programs currently available are based on three different protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are ...
... The most common file sharing programs currently available are based on three different protocols. Fasttrack, used by KaZaA and others; Gnutella, which is both a protocol and a client; and WinMX. In addition to the threats below, these programs often come loaded with spyware. Since these products are ...
Slide 1
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
... Data origin authentication is the core of the design of DNSSEC. It mitigates such threats as cache poisoning and zone data compromise on a DNS server. The RRSets within a zone are signed to assert to resolvers and servers that the data just received can be trusted. The digital signature contains ...
Aspects of Biological Evolution and Their
... provide a great deal of information to an attacker such as user ids and periods of activity on a system thus allowing for exploits based on social engineering (17, 19). ...
... provide a great deal of information to an attacker such as user ids and periods of activity on a system thus allowing for exploits based on social engineering (17, 19). ...
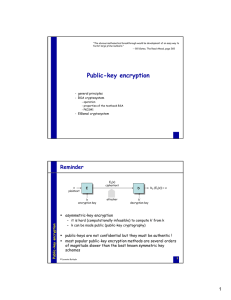
Public-key encryption
... appending a (pseudo) random bit string to the plaintext prior to encryption salting is a solution to the small exponent problem – even if the same message m has to be sent to many recipients, the actual plaintext that is encrypted will be different for everyone due to salting Public-key encrypti ...
... appending a (pseudo) random bit string to the plaintext prior to encryption salting is a solution to the small exponent problem – even if the same message m has to be sent to many recipients, the actual plaintext that is encrypted will be different for everyone due to salting Public-key encrypti ...
2 Optional Features (WOFD-900000)
... The M2000 supports PEM and DER certificate formats defined in the ITU-T X.509v3 standard. The M2000 can manage device certificates, trusted certificates, and CRLs and provides differentiated management functions for these certificates. A device certificate is a file containing public keys and owners ...
... The M2000 supports PEM and DER certificate formats defined in the ITU-T X.509v3 standard. The M2000 can manage device certificates, trusted certificates, and CRLs and provides differentiated management functions for these certificates. A device certificate is a file containing public keys and owners ...
Folksonomy - Columbia University
... • They do not yield the level of clarity that controlled vocabularies do ...
... • They do not yield the level of clarity that controlled vocabularies do ...
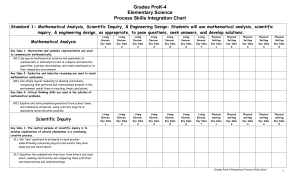
154 kb - Mahopac Central School District
... descriptions of objects and events and to from their own tentative explanations of what they have observed. Key Idea 2: Beyond the use of reasoning & consensus, scientific inquiry involves the testing of proposed explanations involving the use of conventional techniques & procedures & usually requir ...
... descriptions of objects and events and to from their own tentative explanations of what they have observed. Key Idea 2: Beyond the use of reasoning & consensus, scientific inquiry involves the testing of proposed explanations involving the use of conventional techniques & procedures & usually requir ...
Sohel Ahmed Syed Flat #402, Shivshankar 2, Contact Number: +91
... Create new systems on SAP Service Marketplace for the new environment and request license keys. Propose hardware and software requirements based on the sizing calculations. Get an approval for the new server hardware requests and assist server provisioning team for the ...
... Create new systems on SAP Service Marketplace for the new environment and request license keys. Propose hardware and software requirements based on the sizing calculations. Get an approval for the new server hardware requests and assist server provisioning team for the ...
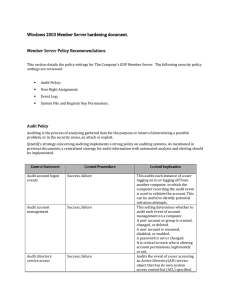
Server hardening - Cisco Security Solutions
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
CIS 5357 - FSU Computer Science
... Semantic Security • The game – Adversary is given a public key and can generate any number of ciphertexts (polynomial time bound and probabilistically) – Adversary generates two equal – length messages m0 and m1 and transmits them to a challenge oracle along with the public key – The challenge orac ...
... Semantic Security • The game – Adversary is given a public key and can generate any number of ciphertexts (polynomial time bound and probabilistically) – Adversary generates two equal – length messages m0 and m1 and transmits them to a challenge oracle along with the public key – The challenge orac ...
Trust in Society - Russell Sage Foundation
... emerge if they allow people to collect information and take tentative steps toward establishing trust where none previously existed. Woven throughout Heimer’s chapter is the story of the “Jane” organization, set up a few years before the Roe v. Wade decision in 1973 to help women terminate unwanted ...
... emerge if they allow people to collect information and take tentative steps toward establishing trust where none previously existed. Woven throughout Heimer’s chapter is the story of the “Jane” organization, set up a few years before the Roe v. Wade decision in 1973 to help women terminate unwanted ...
LogMeIn Security – an In-Depth Look
... installing a remote access product. Remote access products are perceived as high risk factors, but mainly for psychological reasons. When a user first sees a remote access solution in action, their first negative reaction is usually with regard to the security implications. This is perfectly normal, ...
... installing a remote access product. Remote access products are perceived as high risk factors, but mainly for psychological reasons. When a user first sees a remote access solution in action, their first negative reaction is usually with regard to the security implications. This is perfectly normal, ...
Commiting a Rule Tree
... • UNIX has several advantages as an operating system, such as portability, powerful utilities, device independence, being multitasking, allowing multi-user, low system requirements, and the availability of free software. • There are disadvantages of using the UNIX operating system. Some of them are ...
... • UNIX has several advantages as an operating system, such as portability, powerful utilities, device independence, being multitasking, allowing multi-user, low system requirements, and the availability of free software. • There are disadvantages of using the UNIX operating system. Some of them are ...







![slides [pdf]](http://s1.studyres.com/store/data/003737230_1-2696b7865b4160afff3b6862ae017bef-300x300.png)