Chapter 1. Introduction to Data Communications
... • User profiles can limit the allowable log-in days, time of day, physical locations, and the allowable number of incorrect log-in attempts. • Creating accounts and profiles is simple, as they are created when new personnel arrive. • One security problem is often created because network managers for ...
... • User profiles can limit the allowable log-in days, time of day, physical locations, and the allowable number of incorrect log-in attempts. • Creating accounts and profiles is simple, as they are created when new personnel arrive. • One security problem is often created because network managers for ...
Hybrid cryptography using symmetric key encryption
... Encryption is a method of converting plain text to cipher text. Generally lot of secured information’s are transferred using internet services these can be easily retrieved by eavesdroppers in the community system. Encryption is mainly employed in banking, accounting, state and national bureau, mili ...
... Encryption is a method of converting plain text to cipher text. Generally lot of secured information’s are transferred using internet services these can be easily retrieved by eavesdroppers in the community system. Encryption is mainly employed in banking, accounting, state and national bureau, mili ...
Dr. Clifford Neuman University of Southern California Information
... – Solves n2 problem • Performance – Slower than conventional cryptography – Implementations use for key distribution, then use conventional crypto for data encryption • Trusted third party still needed – To certify public key – To manage revocation – In some cases, third party may be off-line Copyri ...
... – Solves n2 problem • Performance – Slower than conventional cryptography – Implementations use for key distribution, then use conventional crypto for data encryption • Trusted third party still needed – To certify public key – To manage revocation – In some cases, third party may be off-line Copyri ...
Chapter 7 Review
... submissions to web site may contain malicious code that runs locally when others simple read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
... submissions to web site may contain malicious code that runs locally when others simple read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
Chapter 7 Review
... web site may contain malicious code that runs locally when others simply read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
... web site may contain malicious code that runs locally when others simply read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
Apply encryption to network and system security
... keys. A digital certificate is a password protected and encrypted file that contains information about an individual's identity and their public key. A certificate server stores digital certificates and is used as a central location for users requiring public keys. This is known as a Certificate Aut ...
... keys. A digital certificate is a password protected and encrypted file that contains information about an individual's identity and their public key. A certificate server stores digital certificates and is used as a central location for users requiring public keys. This is known as a Certificate Aut ...
Co-Production is….
... The term Co-Production refers to a way of working, whereby everybody works together on an equal basis to create a service or come to a decision which works for them all. It is built on the principle that those who use a service are best placed to help design it. ...
... The term Co-Production refers to a way of working, whereby everybody works together on an equal basis to create a service or come to a decision which works for them all. It is built on the principle that those who use a service are best placed to help design it. ...
IPSEC Presentation
... • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
... • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
Introduction to z/OS Security
... networks, as it is the case today with TCP/IP networks such as the Internet, can be expressed as: – authentication – data integrity – data confidentiality – non-repudiation they can be achieved with proper reliability only by using cryptography. For instance “strong” authentication is not performe ...
... networks, as it is the case today with TCP/IP networks such as the Internet, can be expressed as: – authentication – data integrity – data confidentiality – non-repudiation they can be achieved with proper reliability only by using cryptography. For instance “strong” authentication is not performe ...
Security - The University of Texas at Dallas
... Example 3: A Distributor Needs a Digital Signature on a PO ...
... Example 3: A Distributor Needs a Digital Signature on a PO ...
Final bits of OS - Department of Computer Science
... • Hardware included on most commercial chips these days • Used by many systems and applications: ...
... • Hardware included on most commercial chips these days • Used by many systems and applications: ...
Operating System Security Fundamentals
... Internet service for transferring files from one computer to another Transmits usernames and passwords in plaintext Root account cannot be used with FTP Anonymous FTP: ability to log on to the FTP server without being authenticated ...
... Internet service for transferring files from one computer to another Transmits usernames and passwords in plaintext Root account cannot be used with FTP Anonymous FTP: ability to log on to the FTP server without being authenticated ...
Edgenuity SSL Protocols
... SSL encrypts information to create secure transactions online. X.509 certificates and asymmetric cryptography are used to verify the counterparty with whom they are communicating with, and to exchange a symmetric key. The session key is then used to encrypt data being exchanged between the Edgenuity ...
... SSL encrypts information to create secure transactions online. X.509 certificates and asymmetric cryptography are used to verify the counterparty with whom they are communicating with, and to exchange a symmetric key. The session key is then used to encrypt data being exchanged between the Edgenuity ...
Support: Ticket, Process, and Expectations
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
... the hard disk will show up just like another hard disk when connected and unlocked via the password). Tutorial available at http://www.trucrypt.org/docs/?s=tutorial Great approach for home computers as it provides a location for all work files to be placed in an encrypted "drive" and when the comp ...
Lecture 10
... Calculates c (t ) mod p and y (t a ) 1 mod p x . Question: Why does it work? It works since: t a (s k ) a s ak mod p , so y (t a ) 1 ( x s ak ) (s ak ) 1 x mod p . ...
... Calculates c (t ) mod p and y (t a ) 1 mod p x . Question: Why does it work? It works since: t a (s k ) a s ak mod p , so y (t a ) 1 ( x s ak ) (s ak ) 1 x mod p . ...
SRA Customized Web Portal | Secure Remote Access | SonicWALL
... The personalized portal is a key element in controlling granular access for each end user. The policies that are created and enforced by the network administrator are reflected in the personalized portal, which reveals to the end user access to only those resources which they are authorized to view. ...
... The personalized portal is a key element in controlling granular access for each end user. The policies that are created and enforced by the network administrator are reflected in the personalized portal, which reveals to the end user access to only those resources which they are authorized to view. ...
CS 291 Special Topics on Network Security
... Both encryption algorithms can provide confidentiality Secret Key Encryption is more efficient and faster ...
... Both encryption algorithms can provide confidentiality Secret Key Encryption is more efficient and faster ...
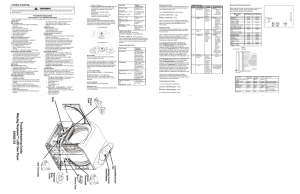
CADD LEGACY PCA Model 6300
... pump will not allow you to start the infusion. 17. To Prime the tubing: o Tubing must NOT be attached to the patient o Pump must be stopped and in LL0 or LL1. o Press the PRIME key and hold the PRIME key down until 3 sets of dashes appears. o Release the PRIME key o Press the PRIME key once more to ...
... pump will not allow you to start the infusion. 17. To Prime the tubing: o Tubing must NOT be attached to the patient o Pump must be stopped and in LL0 or LL1. o Press the PRIME key and hold the PRIME key down until 3 sets of dashes appears. o Release the PRIME key o Press the PRIME key once more to ...
EAP
... A client device connects to a port on an 802.1x switch and AP The switch port can determine the authenticity of the devices The services offered by the switch can be made available on that port Only EAPOL frames can be sent and received on that port until authentication is complete. When the device ...
... A client device connects to a port on an 802.1x switch and AP The switch port can determine the authenticity of the devices The services offered by the switch can be made available on that port Only EAPOL frames can be sent and received on that port until authentication is complete. When the device ...
OSCAR-ENGAGE Refactoring – Progress and Future Work
... But not sacrifice demonstration of features Provide pre-installed demonstrations of software using real scientific applications Straightforward, minimum number of steps to use ...
... But not sacrifice demonstration of features Provide pre-installed demonstrations of software using real scientific applications Straightforward, minimum number of steps to use ...
Acceptable Use Policy
... User’s failure to observe the guidelines set forth in this AUP may result in Company taking actions which range from a warning to a suspension or termination of User’s Products. When feasible, Company may provide User with a notice of an AUP violation via e-mail or otherwise allowing the User to pro ...
... User’s failure to observe the guidelines set forth in this AUP may result in Company taking actions which range from a warning to a suspension or termination of User’s Products. When feasible, Company may provide User with a notice of an AUP violation via e-mail or otherwise allowing the User to pro ...
Ecommerce: Security and Control
... On-line transaction processing: Transactions entered online are immediately processed by computer, and recorded for audit Fault-tolerant computer systems: Contain extra hardware, software, and power supply components in case of element failure High-availability computing: Tools and technologies enab ...
... On-line transaction processing: Transactions entered online are immediately processed by computer, and recorded for audit Fault-tolerant computer systems: Contain extra hardware, software, and power supply components in case of element failure High-availability computing: Tools and technologies enab ...
Troubleshooting Guide Maytag Neptune™ LED Gas Dryer 6390 2110
... Press Air Fluff and Time (^) to enter Service Mode. Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next cod ...
... Press Air Fluff and Time (^) to enter Service Mode. Press the Wrinkle Release key to access the Diagnostic Codes. Scroll through the Diagnostic Codes by pressing the Temperature (^) key. The first time the key is pressed the newest code will be displayed. Each additional key press shows the next cod ...
Hardware Building Blocks and Encoding
... This is an old protocol because early Internet users used to dial into the Internet using a modem and PPP. It is a protocol limited to a single data link. Each call went directly to the remote access server (RAS) whose job was to authenticate the calls as they came in. A PPP communication begins w ...
... This is an old protocol because early Internet users used to dial into the Internet using a modem and PPP. It is a protocol limited to a single data link. Each call went directly to the remote access server (RAS) whose job was to authenticate the calls as they came in. A PPP communication begins w ...