Secure Socket Layer (SSL) 1: Basic Overview
... SSL was originally created to secure web traffic information, in particular data sent between web browsers and servers. For example, when you use Internet Banking and you see https:// and the little padlock in bottom right hand corner of the web browser, you are using SSL. It then grew to work with ...
... SSL was originally created to secure web traffic information, in particular data sent between web browsers and servers. For example, when you use Internet Banking and you see https:// and the little padlock in bottom right hand corner of the web browser, you are using SSL. It then grew to work with ...
XML Security Standards — Overview for the Non - Events
... More efficient and secure than using long term secrets directly Like SSL/TLS except at SOAP layer Useful in conjunction with reliable messaging Adds two new Token types ...
... More efficient and secure than using long term secrets directly Like SSL/TLS except at SOAP layer Useful in conjunction with reliable messaging Adds two new Token types ...
Effective Key Management in Dynamic Wireless
... These approaches take advantage of public key cryptography (PKC) such as elliptic curve cryptography (ECC) or identity-based public key cryptography (ID-PKC) in order to simplify key establishment and data authentication between nodes. PKC is relatively more expensive than symmetric key encryption w ...
... These approaches take advantage of public key cryptography (PKC) such as elliptic curve cryptography (ECC) or identity-based public key cryptography (ID-PKC) in order to simplify key establishment and data authentication between nodes. PKC is relatively more expensive than symmetric key encryption w ...
Web Application Security Vulnerabilities Yen
... should be documented. Ensure that the site is built to gracefully handle all possible errors. Certain classes of errors should be logged to help detect implementation flaws in the site and/or hacking attempts. ...
... should be documented. Ensure that the site is built to gracefully handle all possible errors. Certain classes of errors should be logged to help detect implementation flaws in the site and/or hacking attempts. ...
CIT 016 Review for Final
... Operating systems are intended to be dynamic As users’ needs change, new hardware is introduced, and more sophisticated attacks are unleashed, operating systems must be updated on a regular basis However, vendors release a new version of an operating system every two to four years Vendors use certai ...
... Operating systems are intended to be dynamic As users’ needs change, new hardware is introduced, and more sophisticated attacks are unleashed, operating systems must be updated on a regular basis However, vendors release a new version of an operating system every two to four years Vendors use certai ...
MobileMAN Project Web Service Location in Ad Hoc Network
... • Each information system can publish contents through WS • Each information system can use contents published from other publisher • Use of UDDI (Universal Description Discovery and Integration) to define a way to publish and discover information about Web Services • Use of SOAP (Simple Object Acce ...
... • Each information system can publish contents through WS • Each information system can use contents published from other publisher • Use of UDDI (Universal Description Discovery and Integration) to define a way to publish and discover information about Web Services • Use of SOAP (Simple Object Acce ...
Chapter 6
... • Public-key systems provide several advantages over private-key systems: – The combination of keys required to provide private messages between enormous numbers of people is small – Key distribution is not a problem – Public-key systems make implementation of digital signatures possible ...
... • Public-key systems provide several advantages over private-key systems: – The combination of keys required to provide private messages between enormous numbers of people is small – Key distribution is not a problem – Public-key systems make implementation of digital signatures possible ...
answer-sheet-7540-040-7630-345-b_
... Malware – This is malicious software that is used to gather sensitive information, gain access to private computers, and disrupt computer systems. The consequences of malware are the fact that an individual or company could lose sensitive data that could be used against them and also the fact that p ...
... Malware – This is malicious software that is used to gather sensitive information, gain access to private computers, and disrupt computer systems. The consequences of malware are the fact that an individual or company could lose sensitive data that could be used against them and also the fact that p ...
DCN-7-Network_Security
... of its Digital Certificate issued by some Certification Authority (CA). Digital Certificate is encrypted by the Private Key of CA. 3. Client decrypts the Digital Certificate using the preloaded Public Key of CA and extracts information such as Name of Server, Address of Server, Public Key of Server, ...
... of its Digital Certificate issued by some Certification Authority (CA). Digital Certificate is encrypted by the Private Key of CA. 3. Client decrypts the Digital Certificate using the preloaded Public Key of CA and extracts information such as Name of Server, Address of Server, Public Key of Server, ...
03-WAS Common Threats - Professional Data Management
... • Take advantage of authentication credentials such as tokens and other forms of two factor authentication for sensitive accounts. • Treat e-mails from unknown senders with a high degree of skepticism, and don't click links to access secure sites (type in the Web address into the browser). ...
... • Take advantage of authentication credentials such as tokens and other forms of two factor authentication for sensitive accounts. • Treat e-mails from unknown senders with a high degree of skepticism, and don't click links to access secure sites (type in the Web address into the browser). ...
The CyberFence Difference
... Operators of industrial control networks often opt to secure communications by tunneling protocols over TLS. While doing so may seem a straightforward solution, it often introduces unanticipated impacts. TLS has a higher overhead relative to VPN or V-LAN encryption, which reduces network performance ...
... Operators of industrial control networks often opt to secure communications by tunneling protocols over TLS. While doing so may seem a straightforward solution, it often introduces unanticipated impacts. TLS has a higher overhead relative to VPN or V-LAN encryption, which reduces network performance ...
Cryptography and Coding Theory
... IT662 Cryptography and Coding Theory L – T – P: 3 – 0 – 0 Credit: 3 Objectives: The objective of the course is to provide detail knowledge of cryptography and Coding Theory Pre-requisite: Cryptography knowledge of under grad level. Outcome: Should have earned knowledge of several cryptographic algor ...
... IT662 Cryptography and Coding Theory L – T – P: 3 – 0 – 0 Credit: 3 Objectives: The objective of the course is to provide detail knowledge of cryptography and Coding Theory Pre-requisite: Cryptography knowledge of under grad level. Outcome: Should have earned knowledge of several cryptographic algor ...
Grid Programming (1)
... consistent view of the global status If it provides, the system does not scale to the number of providers ...
... consistent view of the global status If it provides, the system does not scale to the number of providers ...
Do`s and Don`ts for web application developers
... having defined and documented the security configuration and process for keeping all related software up to date. Leave the system in a default install state. Allow access to administration interfaces from untrusted networks. Rely on other people to configure SSL, should the application require it, ...
... having defined and documented the security configuration and process for keeping all related software up to date. Leave the system in a default install state. Allow access to administration interfaces from untrusted networks. Rely on other people to configure SSL, should the application require it, ...
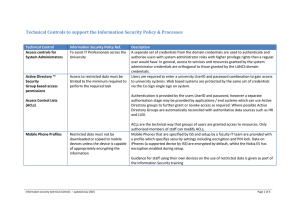
Technical Controls to support the Information
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
compatible-development-of
... RSA Security Inc. released their RSA algorithm into the public domain, a few days in advance of their U.S. Patent 4,405,829 expiring. Following the relaxation of the U.S. government export restrictions, this removed one of the last barriers to the worldwide distribution of much software based on cry ...
... RSA Security Inc. released their RSA algorithm into the public domain, a few days in advance of their U.S. Patent 4,405,829 expiring. Following the relaxation of the U.S. government export restrictions, this removed one of the last barriers to the worldwide distribution of much software based on cry ...
Sujoy Sinha Roy - Cyber Security at IIT Kanpur
... roughly 10 times faster than the ECC-based public-key encryption. Homomorphic encryption enables computation on encrypted data. One application of homomorphic encryption is private cloud computing: a user uploads her encrypted data in the cloud and then computes on the encrypted data. The ring-LWE p ...
... roughly 10 times faster than the ECC-based public-key encryption. Homomorphic encryption enables computation on encrypted data. One application of homomorphic encryption is private cloud computing: a user uploads her encrypted data in the cloud and then computes on the encrypted data. The ring-LWE p ...
01-Intro
... Trap Door (or Back Door) - undocumented entry point written into code for debugging that can allow unwanted users. Bot (robot) - a compromised host that is controlled remotely. Bot Net (botnet) - many bots controlled by the same organization. ...
... Trap Door (or Back Door) - undocumented entry point written into code for debugging that can allow unwanted users. Bot (robot) - a compromised host that is controlled remotely. Bot Net (botnet) - many bots controlled by the same organization. ...
TRUST SCAMS STILL HURTING SENIORS By Lisa Pepicelli
... Pennsylvania of the Uniform Trust Act in 2006, a trust must be administered very much like probate, with legal notices published. A revocable living trust saves no estate or inheritance taxes, because it is still owned by the grantor who puts his assets into it. Anyone who tells you different is lyi ...
... Pennsylvania of the Uniform Trust Act in 2006, a trust must be administered very much like probate, with legal notices published. A revocable living trust saves no estate or inheritance taxes, because it is still owned by the grantor who puts his assets into it. Anyone who tells you different is lyi ...
The key questions that we`d like to ask at the beginning
... Perfect Forward Secrecy Provides Better Protection for Your Website You don’t want your email to be read by other people. You don’t want your credit card information swiped by some hacker online. And that’s why there are secure Web pages—those pages that are transmitted via HTTPS rather than HTTP. H ...
... Perfect Forward Secrecy Provides Better Protection for Your Website You don’t want your email to be read by other people. You don’t want your credit card information swiped by some hacker online. And that’s why there are secure Web pages—those pages that are transmitted via HTTPS rather than HTTP. H ...
System Configuration - Millennium Software Solutions
... by matching statistics Abstract:Most users of online services have unique behavioral or usage patterns. These behavioral patterns can be exploited to identify and track users by using only the observed patterns in the behavior. We study the task of identifying users from statistics of their behavior ...
... by matching statistics Abstract:Most users of online services have unique behavioral or usage patterns. These behavioral patterns can be exploited to identify and track users by using only the observed patterns in the behavior. We study the task of identifying users from statistics of their behavior ...
29-sets-dictionaries
... • count digits: 22092310907 index 0 1 2 3 4 5 6 7 8 9 value 3 1 3 0 0 0 0 1 0 2 ...
... • count digits: 22092310907 index 0 1 2 3 4 5 6 7 8 9 value 3 1 3 0 0 0 0 1 0 2 ...
how to avoid getting on the front pages for the
... Corporation for Assigned Names and Numbers (ICANN). Data that travels from one host to another does not follow a fixed path. It is impossible to predict which paths and through which hosts a data packet will flow. You must therefore assume that every packet sent over the Internet can be intercepted ...
... Corporation for Assigned Names and Numbers (ICANN). Data that travels from one host to another does not follow a fixed path. It is impossible to predict which paths and through which hosts a data packet will flow. You must therefore assume that every packet sent over the Internet can be intercepted ...
網站安全 - 國立暨南國際大學
... • If an attacker can cause errors to occur that the web application does not handle, they can gain detailed system information, deny service, cause security mechanisms to fail, or crash the server. ...
... • If an attacker can cause errors to occur that the web application does not handle, they can gain detailed system information, deny service, cause security mechanisms to fail, or crash the server. ...