Investments/Standard of Care
... that because of special circumstances, the purposes of the trust are better served ...
... that because of special circumstances, the purposes of the trust are better served ...
Description
... Inventory data is categorized into logical inventory data and physical inventory data. Logical inventory data includes information about cells and NE versions. Physical inventory data includes information about racks, subracks, slots, boards, antennas, and ports. Physical inventory properties includ ...
... Inventory data is categorized into logical inventory data and physical inventory data. Logical inventory data includes information about cells and NE versions. Physical inventory data includes information about racks, subracks, slots, boards, antennas, and ports. Physical inventory properties includ ...
Report The Internet Infrastructure Foundation
... PKIX on the Internet. HTTP as the most prominent of the Internet data communications protocols takes advantage of the Transport Layer Security protocol (TLS, RFC 5247[2]) or the Secure Sockets Layer protocol (SSL) by wrapping the communication in the secure channel established using an URI scheme, a ...
... PKIX on the Internet. HTTP as the most prominent of the Internet data communications protocols takes advantage of the Transport Layer Security protocol (TLS, RFC 5247[2]) or the Secure Sockets Layer protocol (SSL) by wrapping the communication in the secure channel established using an URI scheme, a ...
256 Bit Key — Is It Big Enough?
... As computational ability rapidly increases, more concern is being placed on the key size in cryptographic devices. Individuals commonly have a quad processor 4GHz computer on their desks, so trying billions of possibilities to crack a secret key is pretty easy. These attacks are usually called “offl ...
... As computational ability rapidly increases, more concern is being placed on the key size in cryptographic devices. Individuals commonly have a quad processor 4GHz computer on their desks, so trying billions of possibilities to crack a secret key is pretty easy. These attacks are usually called “offl ...
Project Presentations - 2
... ■ Guess nature of relationships between two users ■ Determine factors most indicative of the type of relationship ■ Determine confidence in our guesses ...
... ■ Guess nature of relationships between two users ■ Determine factors most indicative of the type of relationship ■ Determine confidence in our guesses ...
Organizations That Use TLS/SSL
... or Medicaid, is covered by the Health Insurance Portability and Accountability Act (HIPAA) and must meet certain security standards. Additionally, any organization that stores or transmits user login or patient information may need to be compliant with the HIPAA Security Standard, even if it is not ...
... or Medicaid, is covered by the Health Insurance Portability and Accountability Act (HIPAA) and must meet certain security standards. Additionally, any organization that stores or transmits user login or patient information may need to be compliant with the HIPAA Security Standard, even if it is not ...
slides - cse.sc.edu
... What do we mean by code executing with too much privilege? • Software performs an operation at a privilege level that is higher than the minimum level required, which creates new weaknesses or amplifies the consequences of other weaknesses.[2] • High privilege – any process that is capable of perfor ...
... What do we mean by code executing with too much privilege? • Software performs an operation at a privilege level that is higher than the minimum level required, which creates new weaknesses or amplifies the consequences of other weaknesses.[2] • High privilege – any process that is capable of perfor ...
Chapter 19: Security
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
Chapter 19: Security
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
Chapter 19: Security - Murray State University
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
... • Single sign-on – Simplifies the authentication process • Allows the user to log in once using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • If a password becomes available to crackers, all applications protected by that ...
authentication
... • Password Validation. – System uses Kerberos to validate a user password. – Client obtains ticket for user. • Service immaterial, usually ticket granting service (TGS). • If authenticator successfully decrypted, password valid. • System erases ticket and session key. ...
... • Password Validation. – System uses Kerberos to validate a user password. – Client obtains ticket for user. • Service immaterial, usually ticket granting service (TGS). • If authenticator successfully decrypted, password valid. • System erases ticket and session key. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... the storage and communication overheads in the rekeying process, with acceptable computational overhead. It is expected that the MKEMGKM scheme can be a practical solution for various group applications, especially for those requiring many service groups, such as TV streaming services charged on a c ...
... the storage and communication overheads in the rekeying process, with acceptable computational overhead. It is expected that the MKEMGKM scheme can be a practical solution for various group applications, especially for those requiring many service groups, such as TV streaming services charged on a c ...
slides
... Only the owner can grant/revoke read access to/from other users. The creator is the owner of the object. Membership of the three administrative roles cannot change. This policy can be enforced by imposing a cardinality constraint of 1 on OWN_O and of 0 on PARENT_O and PARENTwithGRANT_O. This policy ...
... Only the owner can grant/revoke read access to/from other users. The creator is the owner of the object. Membership of the three administrative roles cannot change. This policy can be enforced by imposing a cardinality constraint of 1 on OWN_O and of 0 on PARENT_O and PARENTwithGRANT_O. This policy ...
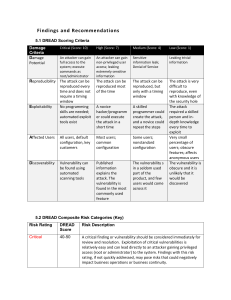
Findings and Recommendations
... the security hole The attack required a skilled person and indepth knowledge every time to exploit Very small percentage of users; obscure features; affects anonymous users The vulnerability is obscure and it is unlikely that it would be discovered ...
... the security hole The attack required a skilled person and indepth knowledge every time to exploit Very small percentage of users; obscure features; affects anonymous users The vulnerability is obscure and it is unlikely that it would be discovered ...
Security Risks
... – Password-protected, encrypted file – Holds identification information – Includes public key ...
... – Password-protected, encrypted file – Holds identification information – Includes public key ...
Get a WIF of this!
... This presentation will focus on how WIF: Can be used with websites as well as web services. Makes life much easier for the developer. Opens up possibilities that normally have been prohibitively complex. Now to introduce the participants of this presentation: ...
... This presentation will focus on how WIF: Can be used with websites as well as web services. Makes life much easier for the developer. Opens up possibilities that normally have been prohibitively complex. Now to introduce the participants of this presentation: ...
Why Do I Retweet It? An Information Propagation Model for Microblogs
... that affect the forwarding of his messages. As previously discussed, these parameters of the model are not directly quantifiable. We could estimate them using a MLE estimator where the likelihood function is given by a sample of retweeting actions extracted from the dataset. Unfortunately, applying ...
... that affect the forwarding of his messages. As previously discussed, these parameters of the model are not directly quantifiable. We could estimate them using a MLE estimator where the likelihood function is given by a sample of retweeting actions extracted from the dataset. Unfortunately, applying ...
Relational Model
... are dynamic, meaning that changes made to base relations that affect view attributes are immediately reflected in the view. ...
... are dynamic, meaning that changes made to base relations that affect view attributes are immediately reflected in the view. ...
Sentinel SuperPro™
... Extensive Code Protection along with Copy Protection CodeCover also enables you to encrypt important code fragments, constants, and plain strings in order to protect your intellectual property (IP) from being copied or modified. For example, CodeCover provides you the assurance that proprietary IP, ...
... Extensive Code Protection along with Copy Protection CodeCover also enables you to encrypt important code fragments, constants, and plain strings in order to protect your intellectual property (IP) from being copied or modified. For example, CodeCover provides you the assurance that proprietary IP, ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... any damage on one side cannot spread to the other side. Ex. Some routers come with firewall functionality ipfw, ipchains, pf on Unix systems, Windows XP and Mac ...
... any damage on one side cannot spread to the other side. Ex. Some routers come with firewall functionality ipfw, ipchains, pf on Unix systems, Windows XP and Mac ...
On PRY-layer Security of Cognitive Radio: Collaborative Sensing
... As shown in (6), the system cannot detect the incumbent primary user (Qd = 0) when the decision rule requests more reports than the number of benign users. Severe interferences will then be introduced to the primary system. Therefore, q should not be very large. Suppose the number of benign users is ...
... As shown in (6), the system cannot detect the incumbent primary user (Qd = 0) when the decision rule requests more reports than the number of benign users. Severe interferences will then be introduced to the primary system. Therefore, q should not be very large. Suppose the number of benign users is ...
Chapter 3 RELATIONAL MODEL
... Candidate key selected to identify tuples uniquely within relation. Candidate keys that are not selected to be primary key. ...
... Candidate key selected to identify tuples uniquely within relation. Candidate keys that are not selected to be primary key. ...