OWASP`s Ten Most Critical Web Application Security Vulnerabilities
... Be extremely careful storing keys, certs, and passwords Rethink whether you need to store the information Don’t store user passwords – use a hash like SHA-256 ...
... Be extremely careful storing keys, certs, and passwords Rethink whether you need to store the information Don’t store user passwords – use a hash like SHA-256 ...
Security Features in Windows CE
... Windows CE allows trusted applications to mark a system flag on databases to deny access to untrusted callers. Untrusted applications cannot open, read, or modify databases that are marked with the system flag. Trusted callers can set the CEDB_SYSTEMDB flag inside the CEDBASEINFOEX structure passed ...
... Windows CE allows trusted applications to mark a system flag on databases to deny access to untrusted callers. Untrusted applications cannot open, read, or modify databases that are marked with the system flag. Trusted callers can set the CEDB_SYSTEMDB flag inside the CEDBASEINFOEX structure passed ...
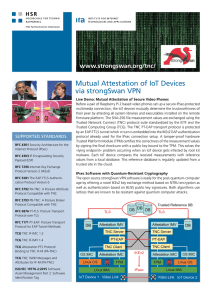
Mutual Attestation of IoT Devices via strongSwan VPN
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
System Security - Wright State engineering
... Let us assume that Mallory, a cracker, not only can listen to the traffic between Alice and Bob, but also can modify, delete, and substitute Alice's and Bob's messages, as well as introduce new ones. Mallory can impersonate Alice when talking to Bob and impersonate Bob when talking to Alice. Here is ...
... Let us assume that Mallory, a cracker, not only can listen to the traffic between Alice and Bob, but also can modify, delete, and substitute Alice's and Bob's messages, as well as introduce new ones. Mallory can impersonate Alice when talking to Bob and impersonate Bob when talking to Alice. Here is ...
pps - AquaLab - Northwestern University
... Protection mechanisms Computer system has objects to protect – Hardware and software, each with ...
... Protection mechanisms Computer system has objects to protect – Hardware and software, each with ...
Lecture #22
... the secret encryption key of the server. Sealed tickets can be sent safely over a network - only the server can make sense out of it. Each ticket has a limited lifetime (a few ...
... the secret encryption key of the server. Sealed tickets can be sent safely over a network - only the server can make sense out of it. Each ticket has a limited lifetime (a few ...
Unit 11
... Public-Key Cryptography • Scenarios: – sender encrypts message with private key – receiver decrypts message with sender’s public key – result: receiver has authenticated sender ...
... Public-Key Cryptography • Scenarios: – sender encrypts message with private key – receiver decrypts message with sender’s public key – result: receiver has authenticated sender ...
Enhanced Security Models for Operating Systems: A Cryptographic
... Vaults provide protection to both read and write operations. Read and Write protection: Now a days, cryptographic file systems only provide confidentiality. Writing into encrypted file is difficult. Vaults provide file protection keys, where it can provide confidentiality and integrity. Mess ...
... Vaults provide protection to both read and write operations. Read and Write protection: Now a days, cryptographic file systems only provide confidentiality. Writing into encrypted file is difficult. Vaults provide file protection keys, where it can provide confidentiality and integrity. Mess ...
FTAA Joint Public-Private Sector Committee of Experts
... signatures, cryptography, authentication and certification, and has been involved in the development of criteria for mutual acceptance of certification authorities, trusted third parties (TTP) and infrastructure for their management and use on an international basis. International Telecommunications ...
... signatures, cryptography, authentication and certification, and has been involved in the development of criteria for mutual acceptance of certification authorities, trusted third parties (TTP) and infrastructure for their management and use on an international basis. International Telecommunications ...
Huawei Videoconferencing System Interoperates with Microsoft
... point-to-point or multipoint in mixed audiovisual format, giving users the flexibility to choose a convenient location to participate in a certain meeting. ...
... point-to-point or multipoint in mixed audiovisual format, giving users the flexibility to choose a convenient location to participate in a certain meeting. ...
090923-eNMR-Barcelona
... Porting applications to the GRID Interoperability of applications Automated data processing and error handling User access Security ...
... Porting applications to the GRID Interoperability of applications Automated data processing and error handling User access Security ...
Shibboleth Access Management System
... that are available freely available for students to download The site also includes lesson plans, discussion questions, and tests that accompany the freely available materials. These materials should only be available to educators. ...
... that are available freely available for students to download The site also includes lesson plans, discussion questions, and tests that accompany the freely available materials. These materials should only be available to educators. ...
Chapter 4
... Authentication service developed as a part of MIT’s Athena project provides centralized private-key third-party authentication in a distributed network ...
... Authentication service developed as a part of MIT’s Athena project provides centralized private-key third-party authentication in a distributed network ...
The Sociology of Trust - Department of Sociology
... The results indicate that the model: 1. explains much of the variance in trust 2. with just a few variables 3. that are easily defined to others. Also, the results indicate overwhelmingly that confidence, not competence, is the key driver of public trust in societal institutions responsible for the ...
... The results indicate that the model: 1. explains much of the variance in trust 2. with just a few variables 3. that are easily defined to others. Also, the results indicate overwhelmingly that confidence, not competence, is the key driver of public trust in societal institutions responsible for the ...
Document
... – NDN does not restrict the format of names – SCN name can be represented as NDN name • two-component NDN name: producer’s key and data name • concatenation in SCN is also NDN name as well – several pairs of producers’ key and data name ...
... – NDN does not restrict the format of names – SCN name can be represented as NDN name • two-component NDN name: producer’s key and data name • concatenation in SCN is also NDN name as well – several pairs of producers’ key and data name ...
Using Digital Signature with DNS
... • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY) ...
... • Public KEYs can be used to verify the SIGs • The authenticity of public KEYs is established by a SIGnature over the keys with the parent’s private key • In the ideal case, only one public KEY needs to be distributed off-band (the root’s public KEY) ...
Security
... to encrypt and decrypt e-mail over the Internet. It can also be used to send an encrypted digital signature that lets the receiver verify the sender's identity and know that the message was not changed en route. Available both as freeware and in a low-cost commercial version, PGP is the most widely ...
... to encrypt and decrypt e-mail over the Internet. It can also be used to send an encrypted digital signature that lets the receiver verify the sender's identity and know that the message was not changed en route. Available both as freeware and in a low-cost commercial version, PGP is the most widely ...
Full Text
... PHRs available for free having good functionalities and ease of use, there are only relatively few people that seems to use them. A reason for this is that people are lazy in taking preventive measures of their health. They see healthcare as “having someone else to make it better, and not about pers ...
... PHRs available for free having good functionalities and ease of use, there are only relatively few people that seems to use them. A reason for this is that people are lazy in taking preventive measures of their health. They see healthcare as “having someone else to make it better, and not about pers ...
ppt
... round-robin or random manner. In other words, application load balancing uses some knowledge about the application’s run-time behavior and network load balancers limit their knowledge to the ...
... round-robin or random manner. In other words, application load balancing uses some knowledge about the application’s run-time behavior and network load balancers limit their knowledge to the ...
Chapter 24 - William Stallings, Data and Computer
... • a security service that monitors and analyzes system events for the purpose of finding, and providing real-time or near-real-time warning of, attempts to access system resources in an ...
... • a security service that monitors and analyzes system events for the purpose of finding, and providing real-time or near-real-time warning of, attempts to access system resources in an ...
XML: Part - Houston Community College System
... • Can provide the information in a publicly accessible directory, called a Certificate Repository (CR) • Some organizations set up a Registration Authority (RA) to handle some CA, tasks such as processing certificate requests and authenticating users Security+ Guide to Network Security Fundamentals, ...
... • Can provide the information in a publicly accessible directory, called a Certificate Repository (CR) • Some organizations set up a Registration Authority (RA) to handle some CA, tasks such as processing certificate requests and authenticating users Security+ Guide to Network Security Fundamentals, ...
module_70
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...