DNS Session 5 Additional Topics
... • Clients obtain a trusted copy of a public key used to sign the root zone ...
... • Clients obtain a trusted copy of a public key used to sign the root zone ...
Protecting Valuable Physical Assets in a High Traffic Setting
... within that system) or operator level (opens specific doors only). Rekeying, re-pinning and re-issuing replacement keys must all happen very quickly. Finally, the TSA needs to be notified within a certain time frame that the key has been lost and the locks have been changed—essentially they need ass ...
... within that system) or operator level (opens specific doors only). Rekeying, re-pinning and re-issuing replacement keys must all happen very quickly. Finally, the TSA needs to be notified within a certain time frame that the key has been lost and the locks have been changed—essentially they need ass ...
Web Application Security
... HTTPS Stands for Hypertext Transfer Protocol over Secure Socket Layer. HTTPS = Combination of normal HTTP interaction over an encrypted Secure Sockets Layer (SSL) or Transport Layer Security (TLS) connection. Using an https: URL indicates that HTTP is to be used, but with a different default ...
... HTTPS Stands for Hypertext Transfer Protocol over Secure Socket Layer. HTTPS = Combination of normal HTTP interaction over an encrypted Secure Sockets Layer (SSL) or Transport Layer Security (TLS) connection. Using an https: URL indicates that HTTP is to be used, but with a different default ...
Collaborative Filtering
... Regression-Based • Use approximation of ratings to make predictions against a regression model • Apply to situations where rating vectors have large Euclidean distances but very high Similarity Computation scores ...
... Regression-Based • Use approximation of ratings to make predictions against a regression model • Apply to situations where rating vectors have large Euclidean distances but very high Similarity Computation scores ...
Security
... Privacy – how to ensure information has not been captured by a third party Integrity – how to ensure the information has not been altered in transit Authentication – how to ensure the identity of the sender and receiver Authorization – how to ensure a user has the authority to access / update inform ...
... Privacy – how to ensure information has not been captured by a third party Integrity – how to ensure the information has not been altered in transit Authentication – how to ensure the identity of the sender and receiver Authorization – how to ensure a user has the authority to access / update inform ...
Chapter 10: Electronic Commerce Security
... today as Caesar Cyphers. The simplest replaces A with B, B with C etc. This is called a one-rotate code. The following is encrypted using a simple Caesar rotation cypher. See if you can decrypt it: ...
... today as Caesar Cyphers. The simplest replaces A with B, B with C etc. This is called a one-rotate code. The following is encrypted using a simple Caesar rotation cypher. See if you can decrypt it: ...
Enabling Trustworthy Service Evaluation in
... users to share service reviews in service-oriented mobile social networks (SMSNs). Each service provider independently maintains a TSE for itself, which collects and stores users’ reviews about its services without requiring any third trusted authority. The service reviews can then be made available ...
... users to share service reviews in service-oriented mobile social networks (SMSNs). Each service provider independently maintains a TSE for itself, which collects and stores users’ reviews about its services without requiring any third trusted authority. The service reviews can then be made available ...
abstract - Chennaisunday.com
... sector but also to the government sector. As a result, many aspects required for successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. Ho ...
... sector but also to the government sector. As a result, many aspects required for successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. Ho ...
Public Key Encryption and Digital Signatures
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
... – Public Key encryption • does not require communication of a key • security depends on the difficulty of factoring very large numbers (hundreds of digits) ...
CMSC 414 Computer (and Network) Security
... – Can provide security on “insecure” systems – Users choose when to use PGP; user must be involved – Alice’s signature on an email proves that Alice actually generated the message, and it was received unaltered; also non-repudiation – In contrast, SSL would secure “the connection” from Alice’s compu ...
... – Can provide security on “insecure” systems – Users choose when to use PGP; user must be involved – Alice’s signature on an email proves that Alice actually generated the message, and it was received unaltered; also non-repudiation – In contrast, SSL would secure “the connection” from Alice’s compu ...
Three challenges with secret key encryption
... 2. Organizational Registration Authorities (ORAs) that vouch for the binding between public keys, certificate holder identities, and other attributes. 3. Certificate holders that are issued certificates and that can sign digital documents. 4. Clients that validated digital signatures and their certi ...
... 2. Organizational Registration Authorities (ORAs) that vouch for the binding between public keys, certificate holder identities, and other attributes. 3. Certificate holders that are issued certificates and that can sign digital documents. 4. Clients that validated digital signatures and their certi ...
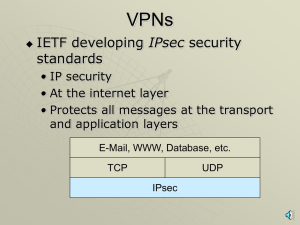
VPNs, PKIs, ISSs, SSLs with narration
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
Chapter 8: Network Security
... your network communication, reading your messages to obtain your credit card information. It is possible and practical, however, to encrypt messages so as to prevent an adversary from understanding the message contents. A protocol that does so is said to provide confidentiality. ...
... your network communication, reading your messages to obtain your credit card information. It is possible and practical, however, to encrypt messages so as to prevent an adversary from understanding the message contents. A protocol that does so is said to provide confidentiality. ...
Document
... Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
... Target: Users who primarily utilizes the web Platform: Netbooks License: Open Source (As of Nov 19, 2009) Called Chromium OS Anticipated Release Date: Second half of ...
Chapter 2: Introduction to Microprocessor
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
Disclaimer - euphore home page
... For documents and data available from this server, Fundación CEAM does not warrant or assume any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, analysis procedure, tools or process descriptions disclosed. Security We inform the users of these Web ...
... For documents and data available from this server, Fundación CEAM does not warrant or assume any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, analysis procedure, tools or process descriptions disclosed. Security We inform the users of these Web ...
055931_PPTx_CH14
... Crypto Keys on the Network • The key management problem – Ensure that the right people have keys – Prevent attackers from uncovering keys • Key distribution objectives – Ensure that keys are changed periodically – Change keys when access rights change • The default keying risk: keys installed by ve ...
... Crypto Keys on the Network • The key management problem – Ensure that the right people have keys – Prevent attackers from uncovering keys • Key distribution objectives – Ensure that keys are changed periodically – Change keys when access rights change • The default keying risk: keys installed by ve ...
Database Security
... Writing applications programs that perform unauthorized operations Deriving information about hidden data by clever querying Removing physical storage devices from the computer facility Making copies of stored files without going through the DBMS Bribing, blackmailing or influencing authorized users ...
... Writing applications programs that perform unauthorized operations Deriving information about hidden data by clever querying Removing physical storage devices from the computer facility Making copies of stored files without going through the DBMS Bribing, blackmailing or influencing authorized users ...
Abstract - PG Embedded systems
... · Packet recovery latency is independent of the RTT of the link. While FEC codes have been used for decades within link-level hardware solutions, faster commodity processors have enabled packet-level FEC at end hosts. ...
... · Packet recovery latency is independent of the RTT of the link. While FEC codes have been used for decades within link-level hardware solutions, faster commodity processors have enabled packet-level FEC at end hosts. ...
Passwords - University of Colorado Boulder
... Symmetric algorithms are faster than public key algorithms, but public key algorithms are required to maintain privacy during the exchange of the faster symmetric keys. To preserve both efficiency and privacy, secure Web transactions begin with a public key exchange, followed by the exchange of a se ...
... Symmetric algorithms are faster than public key algorithms, but public key algorithms are required to maintain privacy during the exchange of the faster symmetric keys. To preserve both efficiency and privacy, secure Web transactions begin with a public key exchange, followed by the exchange of a se ...