* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Passwords - University of Colorado Boulder
Survey
Document related concepts
Transcript
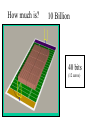
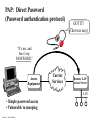
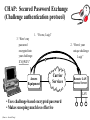
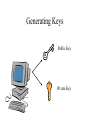
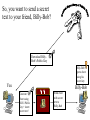
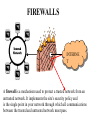
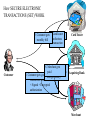
NETWORK SECURITY Source: Wired Computer and Network Attack Taxonomy Attackers Tools Access Hackers User Command Implementation Vulnerability Unauthorized Access Spies Script or Program Design Vulnerability Unauthorized Use Terrorists Autonomous Agent Configuration Vulnerability Corporate Raiders Toolkit Professional Criminals Distributed Tool Vandals Data Tap Process Time Source: Dissertation of John D. Howard, CMU, 1997 Results Objectives Files Corruption of Information Challenge, Status Data in Progress Disclosure of Information Political Gain Theft of Service Financial Gain Denial-ofService Damage Group Task • Get together on groups of 3-5 people • Discuss an attack that one of your group members have experienced or heard about • For that attack, mark within which cells the attack belongs • Five minutes Securing Resources Threats to Security • Physical security • Access Security – Unauthorized access into a computer – Tapping into a data communications line • Personnel – Misuse by authorized personnel • Natural Disaster • Computer Viruses, Worms, Logic Bombs. • Denial of Service Attacks Security concepts/terminology Need to address following issues: • Secrecy/Privacy: guarantee that information given will not be misused • Authenticity: data provided to user must be authentic (i.e., is it really coming from X?) • Integrity: data stored in system must not be corrupted. • Non-repudiation: A mechanism which prevents a user from denying a legitimate, billable charge. Phishing Which one would YOU trust? User Identification and Authorization • Passwords – kept in encrypted file – should be changed frequently – automatic expiration • Ultra-sensitive applications – layered IDs (passwords at several levels) – user profiles (restrictions on who can do what) – access levels (read, write, execute, purge) – combining menus and user profiles (let user see only those options available to her) Time and Location Restrictions • Establish time intervals during which transaction is allowed • Certain transactions can run only from certain locations – attach applications to terminals – maintain terminal profile • Additional precautions on switched ports with dial-in access – call-back unit – restricted hours – safeguard telephone numbers – manual authentication in high security installations Other Methods • Recognizing unauthorized access attempts – after 3 failed attempts disallow log-in for 5 minutes – permit fake log-in after several failed attempts • Automatic log-off – log off anybody with no activity for 10 minutes – authentication for every transaction • Transaction logs – every log-in is logged (date, time user id, unsuccessful attempts, terminal id, location) No method is foolproof. These are delaying tactics. Setting: Europe Time: 1940-45 How? Securing Communications Data Encryption • Symmetric Key Cryptography – Data encryption standard (DES), Bureau of standards (based on symmetric key) • 56-bit encryption key (now available in longer keys) • uses 16 iterations of rearrangement and substitution combinations • Its 72-quadrillion combinations were broken in 1997 by a group using distributed computing (14,000 computers) – lead by Colorado programmer Rocke Verser • Public Key cryptography – (the other approach, covered later) 31798603996994715581310583186337934867429744958612 How much is? 1 Billion 30 bits (9 zeros) Source: http://www.kokogiak.com/ megapenny/default.asp How much is? 10 Billion 40 bits (12 zeros) How much is? 1 Quadrillion 50 bits (15 zeros) How much is? 1 Quintillion 60 bits (18 zeros) How much is? 1 Octillion 128 bits (38 zeros) Previous collection (enlarged for your benefit) How much is? Number of pennies that can fit inside the Universe 300 bits (90 zeros) Thanks to Alexander Voronovich for help with calculation “RSA Laboratories currently recommends key sizes of 1024 bits for corporate use and 2048 bits for extremely valuable keys like the root key pair used by a certifying authority “ 2048 bits (616 zeros) Source: http://www.rsasecurity.com/rsalabs/node.asp?id=2218 Downloaded 04/06/06 Symmetric Key Encryption Encrypted message: DSPEZHKE Data encryption based on symmetric key (A very old method) • Divide plain text into groups of 8 characters. Pad with blanks at end (if necessary) • Select an 8-character key • Rearrange plain text by interchanging adjacent characters (first with second, third with fourth) • Translate each character into a number (A-1, B-2, C-3, ....., Z26, blank-0) • Add the numbers of the key (Step 2) to the results of above step. Data encryption based on symmetric key(contd.) • Divide each sum by 27 and keep remainder • Translate remainder back into character to yield the cipher text. At the receiving end • Perform the reverse operation (i.e., the same set of steps in reverse order) to restore the original text. Example • DATA _COM • ADATC_MO rearrange characters • 01 04 01 20 03 00 13 15 translate 16 18 15 20 15 03 15 12 key vals. 17 22 16 40 18 03 28 27 sum 17 22 16 13 18 03 01 00 mod 27 • Q V P M R C A _ result PAP: Direct Password (Password authentication protocol) GOT IT! (That was easy) “It’s me, and here’s my PASSWORD.” Access Equipment Carrier Services Remote LAN Access Server LAN • Simple password access • Vulnerable to snooping (Source: Ascend Corp) CHAP: Secured Password Exchange (Challenge authentication protocol) 3. “Here’s my password encrypted into your challenge: XYQWZY.” ? 1. “It’s me, Luigi” Access Equipment 2. “Here’s your unique challenge 3 2 Carrier Services Luigi” Remote LAN Access Server LAN • Uses challenge-based encrypted password • Makes snooping much less effective (Source: Ascend Corp) Token 2. User enters PIN and challenge into token password Token Device 3. Token device generates onetime password 1. Challenge received from central site Challenge: XYZ123 4. user enters password at prompt Enter password: • Several types of token systems •Token generates exclusive one-time password •Requires possession of token device and PIN Source: Ascend Corp. 5. Password sent to central site Public Key Cryptography (A brilliant idea proposed in 1976) Generating Keys Public Key Private Key Example Public Key: -----BEGIN PGP PUBLIC KEY BLOCK----Version: PGPfreeware 7.0.3 for non-commercial use <http://www.pgp.com> mQGiBDvxSuQRBADwvXMXRZB+lJpzja9Dc3LVjxORM5tWsrPfQdVca2ATYXuFlq/d WdQzyvtc02e4RpTBeeA/X3UCtAhDxKN1QxB08qosV0tQ4XLmwcbazBsZySJQRv2S 0CygJiNltxZgCk4KVciZHQzXW3OU8U+KU7fTsUHkw9qhu1dFcXoVyqj1PQCg/5+u 8zconmVM7z0ivM9y0us9zocD/j5/G+2/tb6b3n3S9KIEo7fTLXytsIp2bN53Kmxx DnIFhXTIb0i3k7JvvQi7v7akPbdrRrNmc+49hYZsYzTIjLDoSzz/A516Rjpp3u/8 7DHZJp3XL60QRfVAYzUeq62PweBgEKcBBaHAe7ylS7ozqENdXe2l6X8sNJjoLmbJ oiqSBADEEt4GRI5/jB5m9QyDBv6h2yTn/J3Ofb6YXc6jlGdUMfCtJtE83EYxetJW qb306epyns6DhbjyR0wdOp9bkt4gOOnDjx01Jcs4ZxaV73daLdnETxOWdTj6aNw5 W+B4xnGBDd6pb2GFx37a29WtlciKqfCPq37gpYOH4tmpzrvP47QqS2FpIFIuIFQu IExhcnNlbiA8a2FpLmxhcnNlbkBjb2xvcmFkby5lZHU+iQBYBBARAgAYBQI78Urk CAsDCQgHAgEKAhkBBRsDAAAAAAoJEOKthI8QozYkJf4An0dsntidqj/NcjtcQQwU 03ehxQDoAJ9+ktKDWo8s4OpVr2q4ZFXIqm8yerkCDQQ78UrkEAgA9kJXtwh/CBdy orrWqULzBej5UxE5T7bxbrlLOCDaAadWoxTpj0BV89AHxstDqZSt90xkhkn4DIO9 ZekX1KHTUPj1WV/cdlJPPT2N286Z4VeSWc39uK50T8X8dryDxUcwYc58yWb/Ffm7 /ZFexwGq01uejaClcjrUGvC/RgBYK+X0iP1YTknbzSC0neSRBzZrM2w4DUUdD3yI sxx8Wy2O9vPJI8BD8KVbGI2Ou1WMuF040zT9fBdXQ6MdGGzeMyEstSr/POGxKUAY EY18hKcKctaGxAMZyAcpesqVDNmWn6vQClCbAkbTCD1mpF1Bn5x8vYlLIhkmuqui XsNV6TILOwACAgf8DeWZPsTT1hmXuDLNgq6ga2m3XDkyrn0+D8Xo99GsK6K+cw40 phiat4XpjgrR9rWxV9F4lfdbp5TZgKrOjvkQ3LRUZW3joL8iuUgWxednC/ZS2hQa YWgDUPSw1u76JbgocbwWyjMj/1Q/iehAZcMicPulPo4vugTuOdEUNHAyhhxCDJSC TofJ0nvj5qOwdL+iNU/73xrrckt5QPTnn3Y9mYm3cFYnG2XhU+p2PIzk8US0eUXL dhFVWVQRRa1Jtsk5gOYLPB0H34DjT5CJ7a4ujy4wzR83Mxh1/mmzjVD6Q+qiIbUw 8QJiXBcinwpf9B8/8LfC0eFEHTDU9QmeVDJIy4kATAQYEQIADAUCO/FK5AUbDAAA AAAKCRDirYSPEKM2JAgBAJ4wmc/dZOl7QCYiTHDM9nScqqymLgCg8/eca5JDodSE UqaAm5zi2diYK+s= =w3hs -----END PGP PUBLIC KEY BLOCK----- Imagine a chest with two locks Public Private Keyhole Keyhole …now Imagine that you have the ability to generate such chests at will, and that they all react the same way to the keys belonging to it…as long as you have ONE key (either public or private, you can generate the chest…) So, you want to send a secret text to your friend, Billy-Bob? Download BillyBob’s Public Key Billy-Bob opens chest using his secret key You Billy-Bob Generate chest using B-B’s Public Key + insert secret text! Send chest with secret text to Billy-Bob Public Key Cryptography •Sender encrypts message M into E(M) by applying public key or encryption key (E) of receiver •Receiver decrypts E(M) by applying her private key or decryption key (D): i.e, D(E(M)) = M Based on one-way (or trap door) functions which are easy to compute in one direction but not in the other. – E: Encryption or public key – D: Decryption or private key But how do you prove to your friend, Billy-Bob that you are YOU? (you already have his public key) Use your own Private Key to generate an empty chest Insert your chest inside “his” chest! Billy-Bob tries YOUR public key in the lock of the chest – if the chest opens, it can only be from YOU! You Billy-Bob downloads YOUR public key Billy-Bob opens chest using his secret key Billy-Bob Generate another chest using B-B’s public Key Send chest(s) to Billy-Bob Electronic signatures (Another brilliant idea!) • How do you convince your bank that you are indeed the sender of a message? • Say Alice (A) is sending message to Bank (B): – Alice applies her decryption key DA (M ) – Alice applies bank’s encryption key EB ( DA (M )) – Sends message to bank – Bank applies its decryption key first : DB ( EB ( DA (M ))) DA (M ) – Bank applies Alice’s encryption key EA ( DA (M ))) M • Based on the idea that keys are commutative, ie. EA ( DA (M ))) DA ( EA (M )) PGP (Pretty Good Privacy) (a.k.a. Phil’s pretty good software) http://www.pgp.com • Software written by Phil Zimmerman (of Boulder fame!) • Implements public key cryptography • Available in public domain (on most Unix systems) Basic commands pgp -h (for help) pgp -kg (to create your key) pgp -e text_file her_user_id (to encrypt with recipient’s public key) pgp ciphertextfile (to decrypt ciphertextfile) pgp -ka keyfile ( to add contents of a key file to your key ring) Aircraft Downing in China • • • “The airplane is basically a really big flying tape recorder” “Virtually anything transmitted through the air would be within reach” “…dozens of sensitive antennae pick up signals from radar, radio, cell phones, perhaps even e-mail” Source: The Daily Camera, April 4th, 2001 EP-3E Source: NYT, April 4th, 2001 FIREWALLS INTERNE T A firewall is a mechanism used to protect a trusted network from an untrusted network. It implements the site's security policy and is the single point in your network through which all communications between the trusted and untrusted network must pass. Packet Filtering Firewalls -- Incorporate packet filters in the router software -- Reject/accept packets based on rules Filter Rule Action Internal Host 1 block * 2 allow Mail Port External Host * HACKER 25 * Port Comment * deny access to * connect to mail gateway -- Generally anything not expressly permitted is prohibited. Application-Level Gateways (or Proxy Servers) -- Use software applications to filter traffic for various services. -- Program acts like a gateway (or proxy server), and -- Logs traffic and forwards only the legitimate traffic. -- Do not need rules as with packet level filters, but -- Need a specialized program for each service (e.g. mail proxy, http proxy, etc.). -- Operates at higher layer of OSI protocol. -- Weakness:Runs on top of OS and subject to holes in OS. Internet Security Protocols S-MIME: Secure Multipurpose Internet Mail Extensions. SSL: Secure Socket Layer. SSL is a protocol for transmitting encrypted data over TCP/IP networks. S-HTTP: Secure HTTP. Security extension to HTTP to protect individual transaction requests and responses. SET: Secure Electronic Transaction. Developed by Visa and MasterCard to support bank card payments involving multiple parties (card holder, merchant, acquirer, issuer). Secure Web Transactions Symmetric algorithms are faster than public key algorithms, but public key algorithms are required to maintain privacy during the exchange of the faster symmetric keys. To preserve both efficiency and privacy, secure Web transactions begin with a public key exchange, followed by the exchange of a session key that follows a faster, symmetric algorithm. Digital Certificate Is the cyberspace equivalent of a driver’s license. Way of authenticating yourself to other party. SSL authentication is done by X.509 certificates. Certificates are issued by certification authorities (CAs), e.g. Verisign, GTE Cybertrust,etc., which act as trusted third parties. Each certificate contains: • information about the certificate's format. • a unique serial number. • information about the algorithm used to sign the certificate. • the name of the CA which issued the certificate. • the validity period of the certificate. • identifying information about the "subject," or the entity to whom the certificate belongs,the subject's public key, and the issuer’s signature. How SECURE ELECTRONIC TRANSACTIONS (SET) WORK 4. checks Card Issuer 9. Customer3.gets Bank card authorizes monthly bill transaction Customer 2. Bank decrypts 7. 8. Merchant asks to gets 5. authorizes authorization and “capture” paid transaction transaction 1. Customer 6. Customer gets Initiates goods +and receipt checks get signature money transaction with Order-form + Signed + Encrypted authorization Card Issuer Acquiring Bank Merchant Problems with Encryption • The Battle of Leyte Gulf (October 23-26 1944) – American navy forces split into two, each steaming to meet separate Japanese forces (located far away from each other) • Task Force 38 and Task Force 34 (commanded by Admiral Halsey) – Admiral Nimitz (in Pearl Harbor) was wondering about Task Force 34’s position, sent message: “Where is Task Force 34?” – Cryptographer stuffed message, and sent it as: • “Turkey trots to water XX Where repeat where is Task Force 34 XX The world wonders.” – Halsey’s cryptographer, forgetting to remove all the stuffing, sent the following message to the bridge: • “Where repeat where is Task Force 34 XX The world wonders.” Tennyson’s The Charge of the Light Brigade Half a league, half a league, Half a league onward, All in the valley of Death Rode the six hundred. "Forward, the Light Brigade! "Charge for the guns!" he said: Into the valley of Death Rode the six hundred. Tennyson’s The Charge of the Light Brigade Flash'd all their sabres bare, Flash'd as they turn'd in air, Sabring the gunners there, Charging an army, while All the world wonder'd: … Then they rode back, but not Not the six hundred. Key Security Points High-level security consists of multiple system components: User identification Access verification Security administration Combine multiple security mechanisms for desired level of security Both dial-up security and backbone security are important. Individual responsibility is essential! Source: Ascend Corp. Security Resources • CERT: Computer Emergency Response Team http://www.cert.org/ 1-412-268-7090 • CSI: Computer Security Institute http//www.gocsi.com 1-415-905-2626 • ISSA: Information Systems Security Association http://www.issa-intl.org/ 1-708-699-6441 • TruSecure Corporation (formerly National Computer Security Association) http://www.trusecure.com 1-717-258-1816 • FIRST Forum of Incident Response and Security Teams http//www.first.org Source: Ascend Corp.