Public-Key Cryptosystems Based on Hard Problems
... which aim is to hiding the meaning of a message. Meanwhile the other one, cryptoanalysis deals with breaking cryptosystems. Cryptography is also can be splitted into three main parts: symmetric algortihms, public-key algorithms and cryptograpic protocols. Symmetric cryptography has been used since a ...
... which aim is to hiding the meaning of a message. Meanwhile the other one, cryptoanalysis deals with breaking cryptosystems. Cryptography is also can be splitted into three main parts: symmetric algortihms, public-key algorithms and cryptograpic protocols. Symmetric cryptography has been used since a ...
Guidance on the Use of E-Mail when Sending Person
... Microsoft Exchange (which is usually accessed through Outlook) is the most widely used email system at Trusts across the NHS, (at NUH this is the normal email system with an address type of [email protected]) NHSmail (or nhs.net email as it’s commonly referred to) is a separate email system whic ...
... Microsoft Exchange (which is usually accessed through Outlook) is the most widely used email system at Trusts across the NHS, (at NUH this is the normal email system with an address type of [email protected]) NHSmail (or nhs.net email as it’s commonly referred to) is a separate email system whic ...
InfoSec Acceptable Use Policy. (nd). SANS Institute. Retrieved from
... Blocking suspicious emails and scanning attachment before an end-user opens them is an integral part of keeping viruses away. 3. Gateway Virus/Firewall: Implementing an anti-virus protection at the Internet gateway is very important; this will reduces the risk of virus-infected data of ever reaching ...
... Blocking suspicious emails and scanning attachment before an end-user opens them is an integral part of keeping viruses away. 3. Gateway Virus/Firewall: Implementing an anti-virus protection at the Internet gateway is very important; this will reduces the risk of virus-infected data of ever reaching ...
Relations
... How tables are used to represent data. Connection between mathematical relations and relations in the relational model. Properties of database relations. How to identify candidate, primary, and ...
... How tables are used to represent data. Connection between mathematical relations and relations in the relational model. Properties of database relations. How to identify candidate, primary, and ...
Security Analysis of a Single Sign
... with, when they said that “the Wu–Hsu’s modified version cold not protect the user’s token against a malicious service provider, the work also implicitly agrees that there is the potential for attacks from malicious service providers against SSO schemes. Moreover, if all service providers are assume ...
... with, when they said that “the Wu–Hsu’s modified version cold not protect the user’s token against a malicious service provider, the work also implicitly agrees that there is the potential for attacks from malicious service providers against SSO schemes. Moreover, if all service providers are assume ...
Computer and Information Security
... Encrypting/decrypting with public/private keys are used during the handshake and the session key is used after that. 1. Browser connects to a web server (website) secured with SSL (https). Browser requests that the server identify itself. 2. Server sends its SSL Certificate, including the server’s p ...
... Encrypting/decrypting with public/private keys are used during the handshake and the session key is used after that. 1. Browser connects to a web server (website) secured with SSL (https). Browser requests that the server identify itself. 2. Server sends its SSL Certificate, including the server’s p ...
MT311-14
... be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with objects, allowing you to create security poli ...
... be granted or denied different types of access independently. For example, a file can be a resource, and the read action can be differentiated from the write action. So, you can easily grant read-only access to a particular file. You can do the same with objects, allowing you to create security poli ...
Auditing (cont'd.) - Elgin Community College
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
Threats To Windows Users and Countermeasures
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
Attestation
... apps can decrypt data. e.g.: Messing with MBR or OS kernel will change PCR values. Why can’t attacker disable TPM until after boot, then extend PCRs with whatever he wants? Root of trust: BIOS boot block. Gaping hole: role-back attack on encrypted blobs e.g. undo security patches without being ...
... apps can decrypt data. e.g.: Messing with MBR or OS kernel will change PCR values. Why can’t attacker disable TPM until after boot, then extend PCRs with whatever he wants? Root of trust: BIOS boot block. Gaping hole: role-back attack on encrypted blobs e.g. undo security patches without being ...
Internet Security
... 140.192.*.* are DePaul IP addresses if an outbound packet has a source address of ...
... 140.192.*.* are DePaul IP addresses if an outbound packet has a source address of ...
The Relational Model
... by hiding parts of database from certain users. Permits users to access data in a customized way, so that same data can be seen by different users in different ways, at same time. Can simplify complex operations on base relations: If a view is defined on the join of two relations, users may perform ...
... by hiding parts of database from certain users. Permits users to access data in a customized way, so that same data can be seen by different users in different ways, at same time. Can simplify complex operations on base relations: If a view is defined on the join of two relations, users may perform ...
Permissions
... • If the owners are the same, only permissions on the queried object are verified • If they are different, permissions on both objects are verified – This is called a broken ownership chain ...
... • If the owners are the same, only permissions on the queried object are verified • If they are different, permissions on both objects are verified – This is called a broken ownership chain ...
6.1. Elliptic Curve Cryptography
... The purpose of cryptography is to transmit information in such a way that access to it is restricted entirely to the intended recipient. Originally the security of a cryptotext depended on the secrecy of the entire encrypting and decrypting procedures; however, today we use ciphers for which the alg ...
... The purpose of cryptography is to transmit information in such a way that access to it is restricted entirely to the intended recipient. Originally the security of a cryptotext depended on the secrecy of the entire encrypting and decrypting procedures; however, today we use ciphers for which the alg ...
Security & Cryptography
... Server authentication (almost always). Sets up secure channel between client and server. Client authentication over secure transport layer channel. ...
... Server authentication (almost always). Sets up secure channel between client and server. Client authentication over secure transport layer channel. ...
Session 21
... • Opinion does not cover system description, although system description is often included in the report. But if reviewer knows that system description is misleading, s/he should not issue an opinion on the controls. • Opinion covers the reporting period of not more than one year. CSE 4482, 2009 ...
... • Opinion does not cover system description, although system description is often included in the report. But if reviewer knows that system description is misleading, s/he should not issue an opinion on the controls. • Opinion covers the reporting period of not more than one year. CSE 4482, 2009 ...
PHP Security
... Most PHP application use data entered from a form to build SQL queries, this can cause a security risk. Assume a script that edits data from some table with a form that POSTs to the same script. The beginning of the script checks to see if the form was submitted then updates the user chosen table. ...
... Most PHP application use data entered from a form to build SQL queries, this can cause a security risk. Assume a script that edits data from some table with a form that POSTs to the same script. The beginning of the script checks to see if the form was submitted then updates the user chosen table. ...
A Personalized Recommendation System for NetEase Dating Site
... A matching recommendation is successful only if both of users are satisfied with each other[24, 11]. There have been a few studies on the recommendation of romantic dates for online dating users[13, 5]. The majority of online dating recommendation systems adopt graph-based collaborative filtering al ...
... A matching recommendation is successful only if both of users are satisfied with each other[24, 11]. There have been a few studies on the recommendation of romantic dates for online dating users[13, 5]. The majority of online dating recommendation systems adopt graph-based collaborative filtering al ...
Computer Network Security Protocols and Standards
... – PGP works by creating a circle of trust among its users. In the circle of trust, users, starting with two, form a key ring of public key/name pairs kept by each user. Joining this “trust club” means trusting and using the keys on somebody’s key ring. – Unlike the standard PKI infrastructure, this ...
... – PGP works by creating a circle of trust among its users. In the circle of trust, users, starting with two, form a key ring of public key/name pairs kept by each user. Joining this “trust club” means trusting and using the keys on somebody’s key ring. – Unlike the standard PKI infrastructure, this ...
Speech Title Here
... Would an exploit work every time or only under certain circumstances? E Exploitability How skilled must an attacker be to exploit the vulnerability? users A Affected How many users would be affected by a successful exploit? D Discoverability How likely is it that an attacker will know the vulnerabil ...
... Would an exploit work every time or only under certain circumstances? E Exploitability How skilled must an attacker be to exploit the vulnerability? users A Affected How many users would be affected by a successful exploit? D Discoverability How likely is it that an attacker will know the vulnerabil ...
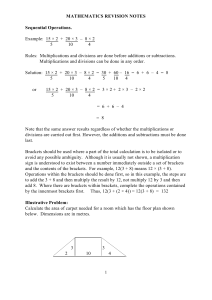
MATHEMATICS REVISION NOTES Sequential Operations. Example
... the number and pressing the LOG key. Some calculators such as the Casio fx100s require the LOG key to be pressed first, enter the number and then press the = key. [See later for more details.] However, in general the exponent is unlikely to be an integer as in the above examples and in this situatio ...
... the number and pressing the LOG key. Some calculators such as the Casio fx100s require the LOG key to be pressed first, enter the number and then press the = key. [See later for more details.] However, in general the exponent is unlikely to be an integer as in the above examples and in this situatio ...
SQL Injection Attack Lab - Computer and Information Science
... – Performance and Inconvenience: not all user inputs are used for SQL queries, so mandatory escaping all data not only affects performance, but also become annoying when some data are not supposed to be esecaped. • Task 3.2: Escaping Special Characters using addslashes(). A PHP function called addsl ...
... – Performance and Inconvenience: not all user inputs are used for SQL queries, so mandatory escaping all data not only affects performance, but also become annoying when some data are not supposed to be esecaped. • Task 3.2: Escaping Special Characters using addslashes(). A PHP function called addsl ...
ppt
... used as the identifiers of classes of email traffic. The lists of addresses spammers send to are unlikely to be similar to those of legitimate users. Lists don’t change that often ...
... used as the identifiers of classes of email traffic. The lists of addresses spammers send to are unlikely to be similar to those of legitimate users. Lists don’t change that often ...