Design of Cognitive Radio Systems Under Temperature
... originated as a possible solution to this problem [2] obtained by endowing the radio nodes with “cognitive capabilities”, e.g., the ability to sense the electromagnetic environment, make short term predictions, and react consequently by adapting transmission parameters (e.g., operating spectrum, mo ...
... originated as a possible solution to this problem [2] obtained by endowing the radio nodes with “cognitive capabilities”, e.g., the ability to sense the electromagnetic environment, make short term predictions, and react consequently by adapting transmission parameters (e.g., operating spectrum, mo ...
Application Security within Java 2, Standard Edition (J2SE)
... from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is derived using known information. Using the GetPermissions method of the Policy instance (the Policy instance is maintained by the system) and the Co ...
... from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is derived using known information. Using the GetPermissions method of the Policy instance (the Policy instance is maintained by the system) and the Co ...
A Stateful Intrustion Detection System for World
... Current IDS - limitations Simple pattern matching of HTTP requests Buffer overflows not detected Attacks involving multiple steps cannot be modeled Only detect trends in large sets of web-related events Focuses on single event stream (network log or server application log) Do not maintain ...
... Current IDS - limitations Simple pattern matching of HTTP requests Buffer overflows not detected Attacks involving multiple steps cannot be modeled Only detect trends in large sets of web-related events Focuses on single event stream (network log or server application log) Do not maintain ...
CH10
... • Distributed denial-of-service (DDoS) attack – Launch simultaneous attack on a Web site via botnets ...
... • Distributed denial-of-service (DDoS) attack – Launch simultaneous attack on a Web site via botnets ...
Power Control for Cognitive Radio Networks
... should be allowed access to the spectrum so long as their admission solely deters the QoS of other secondary users. • Autonomous operation: The power-control technique operates with transmitters having access to only local information. A transmitter would obtain the local information via feedback fr ...
... should be allowed access to the spectrum so long as their admission solely deters the QoS of other secondary users. • Autonomous operation: The power-control technique operates with transmitters having access to only local information. A transmitter would obtain the local information via feedback fr ...
3 Touch the OK key.
... Note that it is not necessary to set passwords; the network scanner functionality can also be used without passwords. A password can be set for the administrator and passwords can be set for each user. If you use a user password to access the Web page, you will be able to establish, edit, and delete ...
... Note that it is not necessary to set passwords; the network scanner functionality can also be used without passwords. A password can be set for the administrator and passwords can be set for each user. If you use a user password to access the Web page, you will be able to establish, edit, and delete ...
Mosaic: Quantifying Privacy Leakage in Mobile
... such as smart phones or tablets, as well as the emergence of various mobile applications and services, information access is nearly ubiquitous and literally at our fingertips. With all the value and convenience it brings to our personal, social, and professional lives, this new era of mobile devices ...
... such as smart phones or tablets, as well as the emergence of various mobile applications and services, information access is nearly ubiquitous and literally at our fingertips. With all the value and convenience it brings to our personal, social, and professional lives, this new era of mobile devices ...
Towards Personalized Context-Aware Recommendation by Mining
... preferences and the current contexts of users, we may be able to make more personalized context-aware recommendations for mobile users. Indeed, the personalized context-aware recommendations can provide better user experiences than general context-aware recommendations which only take into account c ...
... preferences and the current contexts of users, we may be able to make more personalized context-aware recommendations for mobile users. Indeed, the personalized context-aware recommendations can provide better user experiences than general context-aware recommendations which only take into account c ...
Oracle9i Security
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
21. immobilizer system (hiss)
... signal may occur and the proper operation of the system will be obstructed. • The key has built-in electronic part (transponder). Do not drop and strike the key against a hard material object, and do not leave the key on the dashboard in the car, etc. where the temperature will rise. Do not leave th ...
... signal may occur and the proper operation of the system will be obstructed. • The key has built-in electronic part (transponder). Do not drop and strike the key against a hard material object, and do not leave the key on the dashboard in the car, etc. where the temperature will rise. Do not leave th ...
Chapter 15
... techniques, that can be verified by anyone and includes: – The name of the holder and other identification information, such as e-mail address – A public key, which can be used to verify the digital signature of a message sender previously signed with the matching mathematically unique private key – ...
... techniques, that can be verified by anyone and includes: – The name of the holder and other identification information, such as e-mail address – A public key, which can be used to verify the digital signature of a message sender previously signed with the matching mathematically unique private key – ...
Cafe Cracks: Attacks on Unsecured Wireless Networks
... leave. Finally, the attacker must not be noticeable in a public location, since this could put potential victims on edge. Therefore the ideal attack machine is a laptop equipped with two wireless cards. One wireless card is used to access an existing, legitimate wireless network that will be used to ...
... leave. Finally, the attacker must not be noticeable in a public location, since this could put potential victims on edge. Therefore the ideal attack machine is a laptop equipped with two wireless cards. One wireless card is used to access an existing, legitimate wireless network that will be used to ...
Chapter12-Security
... • Not possible to break code given public key • If you want someone to send you secure data, give them your public key, you keep the private key • Secure Sockets Layer on the Internet is a common example of public key cryptography Data Communications and Computer Networks: A Business User's Approach ...
... • Not possible to break code given public key • If you want someone to send you secure data, give them your public key, you keep the private key • Secure Sockets Layer on the Internet is a common example of public key cryptography Data Communications and Computer Networks: A Business User's Approach ...
How Does External Conflict Impact Social Trust? Evidence from a
... to them, and opposing interaction with them). Based on that survey data, the authors find a negligible correlation of 0.07 between in-group favoritism and aggression. In relation to this paper0 s objective, the functional theory view would back up the possibility of external conflict reinforcing int ...
... to them, and opposing interaction with them). Based on that survey data, the authors find a negligible correlation of 0.07 between in-group favoritism and aggression. In relation to this paper0 s objective, the functional theory view would back up the possibility of external conflict reinforcing int ...
Sample pages 2 PDF
... Abstract. In order to cooperate in the open distributed environment, truster agents need to be aware trustworthiness of trustee agents for selecting suitable interaction partners. Most of the current computational trust models make use of the truster itself experience or reputation from community on ...
... Abstract. In order to cooperate in the open distributed environment, truster agents need to be aware trustworthiness of trustee agents for selecting suitable interaction partners. Most of the current computational trust models make use of the truster itself experience or reputation from community on ...
Chapter 12
... • Not possible to break code given public key • If you want someone to send you secure data, give them your public key; you keep the private key • Secure Sockets Layer on the Internet is a common example of public key cryptography ...
... • Not possible to break code given public key • If you want someone to send you secure data, give them your public key; you keep the private key • Secure Sockets Layer on the Internet is a common example of public key cryptography ...
Document
... • Injections flaws allow attackers to relay malicious code through a web application to another system (i.e SQL injections). • When a web application passes information from an HTTP request through as part of an external request, it must be carefully scrubbed. Otherwise the attacker can inject speci ...
... • Injections flaws allow attackers to relay malicious code through a web application to another system (i.e SQL injections). • When a web application passes information from an HTTP request through as part of an external request, it must be carefully scrubbed. Otherwise the attacker can inject speci ...
CHAPTER 1 Networking Concepts
... This standard is an extension of SMTP; MIME gives each attachment of an E-mail message its own header NNTP (Network News Transport Protocol) UseNet servers transfer news items using this specialized transfer protocol LDAP Intelligent Directory Services This protocol will store and deliver contac ...
... This standard is an extension of SMTP; MIME gives each attachment of an E-mail message its own header NNTP (Network News Transport Protocol) UseNet servers transfer news items using this specialized transfer protocol LDAP Intelligent Directory Services This protocol will store and deliver contac ...
Protecting the FPGA Design From Common Threats
... out the clear function and the verification function to provide the maximum design flexibility to the user. By default, the clear function clears the configuration RAM, which contains the design itself, and the embedded RAM, which contains any design specific data. Additionally, the AES encryption k ...
... out the clear function and the verification function to provide the maximum design flexibility to the user. By default, the clear function clears the configuration RAM, which contains the design itself, and the embedded RAM, which contains any design specific data. Additionally, the AES encryption k ...
Security of Cookies in a computer lab setting
... Where are the cookies? • Cookies exist on both major web browsers – Netscape stores all cookies in the cookies.txt file in a Netscape directory – Internet Explorer stores individual cookies as text files in a cookies directory ...
... Where are the cookies? • Cookies exist on both major web browsers – Netscape stores all cookies in the cookies.txt file in a Netscape directory – Internet Explorer stores individual cookies as text files in a cookies directory ...
document
... The cost to an organization of traditional leased lines may be reasonable at first but can increase exponentially as the organization grows. A company with two branch offices, for example, can deploy just one dedicated lineto connect the two locations. If a third branch office needs to come online, ...
... The cost to an organization of traditional leased lines may be reasonable at first but can increase exponentially as the organization grows. A company with two branch offices, for example, can deploy just one dedicated lineto connect the two locations. If a third branch office needs to come online, ...
Application Performance Monitoring
... · Avoiding the blame game. IT organizations often split responsibilities among different support teams, such as Network, Server, Desktop, and Applications. Alternatively, they may split responsibilities according to geographical teams. However modern IT environments involve dependencies among the va ...
... · Avoiding the blame game. IT organizations often split responsibilities among different support teams, such as Network, Server, Desktop, and Applications. Alternatively, they may split responsibilities according to geographical teams. However modern IT environments involve dependencies among the va ...
Copy area
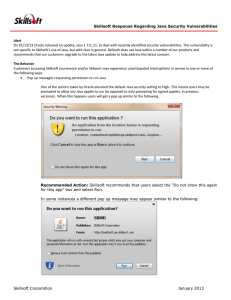
... On 01/13/13 Oracle released an update, Java 1.7.0_11, to deal with recently identified security vulnerabilities. This vulnerability is not specific to Skillsoft’s use of Java, but with Java in general. Skillsoft does use Java within a number of our products and recommends that our customers upgrade ...
... On 01/13/13 Oracle released an update, Java 1.7.0_11, to deal with recently identified security vulnerabilities. This vulnerability is not specific to Skillsoft’s use of Java, but with Java in general. Skillsoft does use Java within a number of our products and recommends that our customers upgrade ...
Application research and analysis based on Bitlocker
... option selected "allows Bitlockerisas without compatible TPM", confirm exit from the local group policy editor, then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the deskt ...
... option selected "allows Bitlockerisas without compatible TPM", confirm exit from the local group policy editor, then Windows 7 operating system uses of Bitlocker encryption system boot disk in the case of without installingtrusted platform module of TPM1.2 version. Encryption started, open the deskt ...