* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Oracle9i Security
Multilevel security wikipedia , lookup
Web of trust wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Access control wikipedia , lookup
Airport security wikipedia , lookup
Cross-site scripting wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Information security wikipedia , lookup
Distributed firewall wikipedia , lookup
Authentication wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Wireless security wikipedia , lookup
Electronic authentication wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Unix security wikipedia , lookup
Computer security wikipedia , lookup
Security-focused operating system wikipedia , lookup
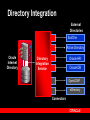
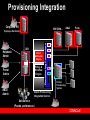
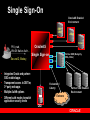
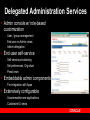
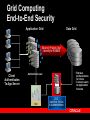
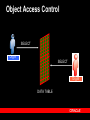
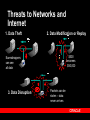
Oracle Security & Identity Management July 20, 2005 Rafael Torres Sr. Solutions Architect Cincinnati, OH 513-768-6856 [email protected] Gary Quarles Sr. Solutions Architect Columbus, OH 614-280-6500 [email protected] Agenda 9am-1015am – Identity Management OID, User Provisioning, Directory Integration, Proxy Authentication – – – Virtual Private Database Securing Data Access Secure Application Roles BREAK (15 mins) Agenda (con’t) 1030am-1145am – – – – – – – – Label Security Fine Grained Auditing Stored Data Encryption Detecting Security Breaches Data Privacy Compliance Network Encryption User Security Oblix Roadmap 1145am-1pm – Buffet Luncheon 1pm-115pm – Raffle Security Legislation Sarbanes-Oxley – – Everyone Financial statements contain no errors Gramm-Leach-Bliley – – Fin Services, Healthcare Ensure privacy, security, confidentiality California’s Breach Disclosure Law – – Anyone with customers in California Audit breach of PII, notify those affected Safe Harbor – – Anyone doing business in Europe Reasonable steps to secure from unauthorized access Data Privacy Concerns Customer information – protecting customer personally identifiable information (PII) Employee information – majority of privacy regulations provide equal or greater rights of privacy to employees Third Party information – protecting PII of third persons provided to you by customers or employees Data Privacy Compliance 25% technical 75% policy and procedures www.oracle.com/consulting The Expert View “90% detected computer security breaches in the past year.” “80% acknowledged financial losses due to computer breaches.” - CSI/FBI Computer Crime and Security Survey “If you spend more on coffee than on IT security, then you will be hacked …what's more, you deserve to be hacked!” Richard Clarke Special Advisor to the President, Cyberspace Security State of Security – United States 90% of respondents* detected computer security breaches within the last twelve months. 80% of respondents acknowledged financial losses due to computer breaches. – – – $455,848,000 in quantifiable losses $170,827,000 theft of proprietary information $115,753,000 in financial fraud 74% cited their Internet connection as a frequent point of attack 33% cited internal systems as a frequent point of attack * Source: CSI/FBI Computer Crime and Security Survey Why Oracle for Security and Identity Management? 25+ year history – First Oracle customer was a government customer Information Assurance – – – – 17 independent security evaluations over past decade Substantial financial commitment to independent security evaluations More evaluations than any other major database vendor Culture of security at Oracle Robust security features and Identity Management Infrastructure – – – – Row level security Fine Grained Auditing Integrated database security and identity management Web Single Sign-on, Oracle Internet Directory Strong authentication Oracle Database = 25+ years of security leadership Label Sec + ID Mgmt Column Sec Policies Security Evaluation 17 Identity Mgmt Release Fine Grained Auditing Common Criteria (EAL4) Oracle9iAS JAAS Oracle9iAS Single Sign-On Oracle Label Security (2000) Virtual Private Database (1998) Enterprise User Security Oracle Internet Directory Database Encryption API 1977 Kerberos framework Support for PKI Radius Authentication Network Encryption Oracle Advanced Security introduced First Orange Book B1 evaluation (1993) Trusted Oracle7 Multilevel Secure Database (1992) Government customer 2004 Oracle Application Server 10g Identity Management Identity Management process by which the complete security lifecycle for users and other entities is managed for an organization or community of organizations. management of an organization's application users, where steps in the security lifecycle include account creation, suspension, privilege modification, and account deletion. Identity Management Components The Identity Challenge End Users Application Application Application Application Directory Server or Database Directory Server or Database Directory Server or Database Directory Server or Database User Credentials for Authentication and Authorization User Credentials for Authentication and Authorization User Credentials for Authentication and Authorization User Credentials for Authentication and Authorization Administrators Administrators Administrators Administrators Redundant, silo’d application development Non-uniform access policies Orphan accounts Audit/Log information fragmented Bring Order to Chaos with Identity End Users Application Application Administrators Application User Credentials for Authentication and Authorization Application Centralized, policy-based management of access & authorization Faster development and deployment Centralized audit and logging Oracle ID Mgmt: Typical Deployments Enterprise provisioning – Heterogeneous integration Telco provisioning – Scalability & HA Enterprise Portal – Single Sign-on, administrative delegation Government R&D Organization, Corporate Conglomerates – Centralized Identities with autonomous administration of departmental applications Multi-hosting with delegated subscriber admin – Multiple identity realms in one physical infrastructure + HA Platform Security Architecture ISV & Custom Applications E-Business Suite Collaboration Suite BPEL Prcs Mgr, BI, Portal, ADF Authorization, Privacy, audit, …. Responsibilities, Roles …. Secure Mail, Interpersonal Grants … Roles, Privilege Groups … External Security Services Access Management Provisioning Services Directory Services Oracle Application Server Oracle Database JAAS, JACC, WS Security, … Enterprise users, VPD, Label Security Encryption, Audit Oracle Identity Management Provisioning & Delegated Administration RBAC & Web Authorization Public Key Infrastructure Directory Integration Oracle Internet Directory SSO & Identity Federation Application Security Oracle Platform Security Internet Directory Scalability – – Millions of users 1000’s of simultaneous clients High availability – – Multimaster & Fan-out replication Hot backup/recovery, RAC, etc. LDAP Clients Manageability – OID Server Grid Control multi-node monitoring Security – – – Comprehensive password policies Role & policy based access control Auditability Extensibility & Virtualization – – – – Plug-in Framework Attribute and namespace virtualization External authentication Custom password policies Directory Admin Console Oracle Database Directory Integration External Directories SunOne Active Directory Oracle Internet Directory Directory Integration Service Oracle HR Oracle DB OpenLDAP eDirectory Connectors Provisioning Integration Corporate HR ERP,CRM,… Helpdesk Admin OID Event Notification Engine Policy & Workflow Engine Portal Admin eMail Admin Provisioning Connectors (Employee Enrollment) Oracle Provisioning Integration Service Self-service (Pswds, preferences) eMail Partner Provisioning System Porta l Single Sign-On OracleAS Enabled Environment ERP, CRM, … eMail Portal PKI, pwd, Win2K Native Auth… OracleAS Single Sign-on Partner SSO (Netegrity, RSA, Oblix) SecureID, Biokey, Integrates Oracle and partnerSSO enabled apps Transparent access to DB Tier, 3rd party web apps Multiple AuthN options Different auth modes to match application security levels Federation / Liberty Extrane t OID Partner SSO Enabled Environment Demonstration IdM: SSO SSO Benefits 1) Tightly integrated with the Oracle product stack 2) Easy to deploy, part of Oracle Identity Management 3) Supports PKI authentication with industry standard X.509V3 certificates 4) Accepts Microsoft Kerberos tokens for easy authentication in a windows environment 5) Integrated with Oracle Certificate Authority (OCA) for easy provisioning of X.509V3 certificates using OCA Certificate Authority Solution for strong authentication / PKI Easy provisioning of X.509v3 digital certificates for end users Oracle Internet Directory User Oracle Single Sign-On Web Based certificate management and administration Seamless integration with Oracle Application Server Single Sign-On & OID Oracle Certificate Authority Secure IT Facility Metadata Repository Future support SAML (Security Assertions Meta Language) – facilitates interoperation and federation among security services. SPML (Service Provisioning Meta Language) – XML standard that facilitates integration among provisioning environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. DSML – XML standard for exchanging directory data as well as invoke directory operations over the Internet. Future support (con’t) XKMS – XML Key Management Specification. It is intended to simplify deployment of PKI in a web services environment. WS-Security – defines a set of SOAP extensions that can be used to provide message confidentiality, message integrity, and secure token propagation between Web Services and their clients Liberty Alliance standards define the framework and protocol for network identity based interactions among users and services within a federated identity management environment. Delegated Administration Services Admin console w/ role-based customization – – – User / group management End-user vs Admin views Admin delegation End-user self-service – – – Self service provisioning Set preferences, Org-chart Pswd reset Embeddable admin components – For integration with Apps Extensively configurable – – Accommodate new applications Customize UI views Demonstration IdM: Delegated Admin Svs Delegated Admin Benefits 1) Enables self service administration of passwords and password resets 2) Enables administrative granularity of Identity Management components 3) Centralized provisioning for web SSO and enterprise user database access 4) Supports password or PKI based authentication 5) Self Service password management without the intervention of an administrator 6) Delegated administrators, such as non-technical managers, to create and manage both users and groups 7) Allows users to search parts of the directory to which they have access Grid Computing End-to-End Security Data Grid Application Grid Securely Proxies User Identity to RDBMS Client Authenticates To App Server • Retrieve Authorizations for Users • Connect users to Application Schema Authenticate user OID Identities, Roles & Authorizations AS10g r2 New 3-tier features Via proxy authentication, including credential proxy of X.509 certificates or Distinguished Names (DN) to the Oracle Database Support for Type 2 JDBC driver, connection pooling for ‘application users’ (Type 2 and Type 4 JDBC Drivers, OCI) Integration with Oracle Identity Management for Enterprise Users (EUS). Demonstration User Security User Security Benefits 1) Enables centralized management of traditional application users in Oracle Identity Management 2) Oracle Identity Management directory integration services can be used for bi-directional synchronization with existing Identity Management infrastructures (AD, SunOne/iPlanet, Netscape) 3) Optionally map users to shared schemes or retain individual account mappings in database for complete application transparency 4) Optionally manage database roles in Oracle Identity Management infrastructure 5) Optionally can be used with Oracle Label Security to maintain security clearances in Oracle Identity Management Oracle IT: Before ID Mgmt HR IDs, passwords, profiles, prefs Employees Self-registered TechNet users My.oracle.com Oracle Files IDs, passwords, profiles, prefs IDs, passwords, profiles, prefs E-Business Apps Oracle Technology Network IDs, passwords, profiles, prefs IDs, passwords, profiles, prefs Web Mail / Calendar Intranet Web Intranet Apps Web Intranet Apps Web Intranet Apps Web Apps Numerous Ids / Passwords & Sign-On IDs, passwords, profiles, prefs Global Mail IDs, passwords, profiles, prefs Partners / Suppliers Extranet Web Conferencing DMZ Employees Corporate Network Calendar Oracle IT: After ID Mgmt HR Employees Self-registered TechNet users My.oracle.com Oracle Files Oracle IdM Infrastructure DMZ Web Conferencing Web Mail / Calendar Single ID/Pswd & SSO Partners / Suppliers Extranet E-Business Apps Oracle Technology Network Employees Intranet Web Intranet Apps Web Intranet Apps Web Intranet Apps Web Apps Corporate Network Global Mail Calendar Oracle IdM Summary Oracle Identity Management is a complete infrastructure providing – – – – – – directory services directory synchronization user provisioning delegated administration web single sign-on and an X.509v3 certificate authority. Oracle Identity Management is designed to provide ready, out-of-the-box deployment for Oracle applications, as well as serve as a general-purpose identity management infrastructure for the enterprise and beyond. Break 15 minutes Privacy & Access Control Oracle9i/10g Secure Application Role CREATE ROLE SAR identified using SCHEMA_USER.PACKAGE_NAME; JDBC / Net8 / ODBC User A, HR Application User A, Financials Application User A, Ad-Hoc Reports Oracle9i 10g • Secure application role is a role enabled by security code • Application asks database to enable role (can be called transparently) • Security code performs desired validation before setting role (privileges) Secure Application Role Benefits Security policy can check anything: – – – – – – time of day day of week IP address/domain Local or remote connection user connected through application X.509 data, etc. Database controls whether privileges are enabled Multiple applications can access database securely Allows secure handshake between applications and database Demonstration Secure Application Role Oracle Database 10g Virtual Private Database Column Relevant Policies – – Policy enforced only if specific columns are referenced Increases row level security granularity Select store_id, revenue… (enforce) Store ID Revenue Department AX703 10200.34 Finance B789C 18020.34 Engineering JFS845 12341.34 Legal SF78SD 13243.34 HR OK Oracle Database 10g Virtual Private Database Column Filtering – Optional VPD configuration to return all rows but filter out column values in rows which don’t meet criteria Select revenue…..(enforce) Store ID Revenue Department AX703 10200.34 Finance OK B789C 18020.34 Engineering OK JFS845 12341.34 Legal OK SF78SD 13243.34 HR OK Demonstration Virtual Private Database Object Access Control SELECT Org A SELECT Org B DATA TABLE Oracle9i/10g Label Security Out-of-the-box, customizable row level security Design based on stringent commercial and government requirements for row level security Project Location Department Sensitivity Label AX703 Chicago Corporate Affairs Public B789C Dallas Engineering Sensitive JFS845 Chicago Legal Highly Sensitive SF78SD Miami Human Resource Confidential : Europe Components of Label Security Label Components are the encoding within data labels and user labels that determine access. Levels – Sensitivity Level (e.g., “Top Secret, Secret, Unclassified”) Compartments – (‘X’,’Y’,’Z’), User must possess all Groups for “Need to Know” – Hierarchical – Supports Organization Infrastructure Oracle Label Security Oracle9i OLS Oracle Label Security Authorizations Confidential : Partners Application Table Project Location Department Sensitivity Label AX703 Boston Finance Public OK B789C Denver Engineering Confidential: Partners OK JFS845 Boston Legal Company Confidential SF78SD Miami HR Company Confidential Demonstration Oracle Label Security Fine-grained Auditing Enforce Audit Policy in Database ... Where Salary > 500000 AUDIT COLUMN = Salary Audit Record Shows... User Queries... Select name, salary from emp where... Employee Table Select name, salary from emp where name = ‘KING’, <timestamp>, <username> The Expert View “ …Companies that properly maintain the security of their systems will eliminate 90 percent of all potential exploits. Companies that fail to take these precautions should prepare for breaches at an increasing rate.” - Giga Information Stored Data Encryption DBMS_OBFUSCATION (9i) DBMS_CRYPTO (10g) Oracle9i Database First Diana Paul Julia Steven Last Roberts Nelson Patterson Drake Store Id 100 200 100 300 Credit Card !3Asjfk234 #k230d23* [email protected] #dkal3j49I3! Supported Encryption Standards AES (128, 192 and 256 Key) RC4 (40, 56, 128, 256 Key) 3DES (2 Key and 3 Key) MD5 SHA1 Demonstration Data Encryption Advanced Security Option Encryption for data in motion – – – – RSA RC4 Public Key Encryption 40, 56 and 128 bit key lengths Support for Data Encryption Standard (DES) algorithm Support for Message Digest 5 (MD5) checksumming algorithm Advanced Security Option Authentication device support – – – RADIUS device Token cards (securID for example) Biometric devices Secure Socket Layer – With X.509 V3 certificate support Support for Open Software Foundation’s Distributed Computing Environment (DCE) Threats to Networks and Internet 1. Data Theft 2. Data Modification or Replay x Eavesdroppers can see all data 3. Data Disruption x Packets can be stolen -- data never arrives $500 becomes $50,000 Demonstration Network Encryption Oblix Brief Overview and Roadmap Oblix: Pure-Play Product Leader Ability To Execute Loosely Coupled: “Leader” in Web Services Management Source Gartner Research (June 2004) Gartner: “Leader” in Access Management Oblix COREid COREid Access COREid Provisioning Web Single Sign-On Template-based workflow Flexible Authentication Methods Policy-based Authorization Agent and Agentless account provisioning Metadirectory synchronization Password synchronization Cross-platform connectivity COREid Identity User, Group, and Organization Management Delegated Administration Self Service and Self Registration Unified Workflow Identity Web Services Controls Password Management Benefits Increased Security Integrated solution Define and enforce security, administrative, and access control policies consistently across enterprise applications Increased Compliance Audit events across entire enterprise Who has access to which applications Access control managed per attribute Meet Sarbanes-Oxley, HIPAA, and GrammLeach-Bliley compliance COREid Reporting Increased Governance COREid Integration Pre-built Connectors – to leading application servers, web servers, portal servers, and directory servers. “Data Anywhere” Configuration Centralized auditing Pre-built identity and security reports Global View user access Robust logging framework Centralized policy definition with localized enforcement Oracle / Oblix IdM Integration Roadmap Current Portfolios Integration Roadmap 10g / 10.1.3 Oblix Immediate Availability Integrated Portfolio Federation (Liberty / SAML-2.0) SHAREid COREid Federation Identity Federation COREid Identity & Access Access Control COREid Provisioning Auditing & Reporting OracleAS SSO Web Authorization Provisioning connectors Provisioning Integration (DIP) Delegated Admin Service COREid Access Oracle-Oblix IdM COREid Provisioning COREid Identity Certificate Authority Delegated Admin Service Meta-Directory Certificate Authority Provisioning Integration Virtual Directory Directory (OID) Meta Directory (DIP) Oracle Identity Mgmt Identity Grid Control COREsv Web Services Management Identity Provisioning Oracle AS SSO Cert. Authority / PKI (OCA) Directory (OID) SSO WS Management (COREsv) OracleAS Option Virtual Directory Directory (OID) ID Grid Control Oracle Identity Mgmt WS Management Gateway OracleAS Option IdM – What does Oracle offer today? Identity & Access Mgmt Identity Integration SSO Web Authorizations Enterprise Provisioning Automation Identity Federation Security Monitoring & Audit Services Privacy & Compliance Management Delegated Admin Role Based Access Ctrl Policy Based Access Ctrl Non-web & 3rd party SSO PKI Certificate Services Password Management Yes Virtual Directory Meta-Directory Directory Oracle - Full Functionality Oracle - Limited Functionality Partner Offering Planned Functionality Current offering with Oblix today Identity & Access Mgmt Identity Integration SSO Web Authorizations Enterprise Provisioning Automation Identity Federation Security Monitoring & Audit Services Privacy & Compliance Management Delegated Admin Role Based Access Ctrl Policy Based Access Ctrl Non-web & 3rd party SSO PKI Certificate Services Password Management Yes Virtual Directory Meta-Directory Directory Oracle - Full Functionality Oracle - Limited Functionality Partner Offering Planned Functionality Thursday, August 11, 2005 8:00 am - 11:00 am (Breakfast & Registration at 8:00am) Oracle Office - Cincinnati 312 Elm Street Suite 1525 Cincinnati, OH 45202 •Oracle COREid Access & Identity •Oracle COREid Federation •Oracle COREid Provisioning •Oracle Single Sign On/Oracle Internet Directory •Oracle Application Server, Enterprise Edition •Oracle Web Services Manager http://www.oracle.com/webapps/events/EventsDetail.jsp?p_eventId=42000&src=3830746&src=3830746&Act=41 QUESTIONS ANSWERS Additional Slides Security Tips 101 “Oracle Security Step-by-step” – – By Pete Finnigan SANS Press Security Tips 101 Keep up with security patches! – – Security alerts from Oracle Technology Network site Security Issues Website Security Tips 101 Check your file system privileges If on Windows, use NTFS not FAT or FAT32 Prevent seeing passwords with UNIX “ps” command –Note 136480.1 or 1009091.6 Check privileges on export files in OS Security Tips 101 If a full export is done to populate a test database, immediately change all passwords No database user except SYS must have: –ALTER SYSTEM –ALTER SESSION Security Tips 101 Change default passwords: – – List of default users and passwords Where to get this list SYS should not be “CHANGE_ON_INSTALL” !!!! SYSTEM should not be “MANAGER” !!!! Security Tips 101 Check scripts that are in the file system that have embedded passwords! Make sure REMOTE_OS_AUTHENT = FALSE –(Allows login without password) REMOTE_OS_ROLES = FALSE also Check for all users with DBA role Check for users or roles with an “ANY” privilege –UPDATE ANY TABLE –DROP ANY TABLE Security Tips 101 Revoke RESOURCE role from normal users No users or roles should have access to: –dba_users –Sys.link$ –Sys.user$ –Sys.user_history$ These have clear text passwords! Security Tips 101 Make sure your listener has a password Use “Current User” database links if possible –“CONNECT TO CURRENT USER” Check database links from Test, Dev and QA instances. Remove any that are not absolutely necessary Avoid plain text passwords in batch files. Use an encryption utility Avoid external accounts for batch processes Security Tips 101 Use the Oracle Security Checklists: – – 9i R2 Security Checklist 9iAS Security Checklist Or third party utilities to check your security Oracle Enterprise Manager 10g includes Security Checking Security Tips 101 1. Only two highly trusted DBAs have sys privileges 2. All other DBAs log in using unique user IDs and those IDs be granted ONLY the privileges needed to do their job. 3. Partition responsibilities as much as possible between the DBAs 4. Security administration, not DBAs, have the ability to grant or change access privileges 5. Employ strong password policies 6. Audit ALL activities the DBAs do 7. Audit ALL activities the two trusted DBAs do both in their regular login and when connected as sys. (9iR2 and higher) Security Tips 101 8. Audit logs are locked out of DBAs reach and monitored and reviewed by security administration, possibly stored on a separate system 9. Replicate the logs to help identify if a log has been tampered with 10. Audit ALL DML on the audit logs 11. Set up fine grained auditing alerts on key information when there is attempted access by unauthorized persons. These alerts are sent to the security administrator. 12. If offshore DBA services are employed, track everything they do very closely and restrict what they can see or do.