VPN: Virtual Private Network
... Secret code that the encryption algorithm uses to create a unique version of cipher-text 8-bits keys = 256 combinations or two to the eighth power 16-bits keys = 65,536 combinations or two to the 16th power 56-bits keys = 72,057,594,037,927,900 or two to the 56th power 168-bits keys … ...
... Secret code that the encryption algorithm uses to create a unique version of cipher-text 8-bits keys = 256 combinations or two to the eighth power 16-bits keys = 65,536 combinations or two to the 16th power 56-bits keys = 72,057,594,037,927,900 or two to the 56th power 168-bits keys … ...
IPsec – An Introduction
... If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
... If Perfect Forward Secrecy (FPS) is being used, performs another Diffie-Hellman (DH) exchange to generate new keys for generating the data encryption keys ...
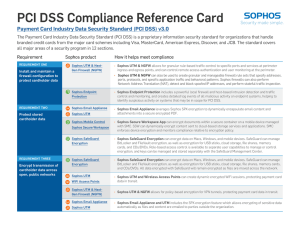
PCI DSS Compliance Reference Card
... ÌÌ Sophos UTM and Wireless Access Points can manage all authentication and access monitoring from clients for access to the payment card environment, with logging of all access attempts. ...
... ÌÌ Sophos UTM and Wireless Access Points can manage all authentication and access monitoring from clients for access to the payment card environment, with logging of all access attempts. ...
Chapter16-PresentationDistilled
... When better authentication confidence is required, more than one authentication factor should be considered ...
... When better authentication confidence is required, more than one authentication factor should be considered ...
Exam Topics in This Chapter
... Version 1.0: No technical content; the appendix was a placeholder to inform readers to check the website for future updates. Version 2.0: Added the following. ...
... Version 1.0: No technical content; the appendix was a placeholder to inform readers to check the website for future updates. Version 2.0: Added the following. ...
PPT - Communications
... • MIB is a text file that describes managed objects using the syntax of ASN.1 (Abstract Syntax Notation 1) • ASN.1 is a formal language for describing data and its properties • In Linux, MIB files are in the directory /usr/share/snmp/mibs – Multiple MIB files – MIB-II (defined in RFC 1213) defines t ...
... • MIB is a text file that describes managed objects using the syntax of ASN.1 (Abstract Syntax Notation 1) • ASN.1 is a formal language for describing data and its properties • In Linux, MIB files are in the directory /usr/share/snmp/mibs – Multiple MIB files – MIB-II (defined in RFC 1213) defines t ...
PDF - Complete Book (2.17 MB)
... comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no guarantee that interference will not ...
... comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no guarantee that interference will not ...
Nortel Secure Network Access 2.0 802.1X
... and the Network Access Protection (NAP) concurrently. These components interoperate, allowing customers to enforce security policies for network access using both NSNA and NAP. This architecture allows deployment of NAP clients with or without a Windows 2008 Server based Network Policy Server (NPS) ...
... and the Network Access Protection (NAP) concurrently. These components interoperate, allowing customers to enforce security policies for network access using both NSNA and NAP. This architecture allows deployment of NAP clients with or without a Windows 2008 Server based Network Policy Server (NPS) ...
IPSec
... • A combination of characters entered at each endpoint of the IPSec connection • Authentication – Both endpoints know the same secret, and no one else has been told – Advantage • Simplicity • Authentication occurs as long as the preshared key is typed in correctly on each device ...
... • A combination of characters entered at each endpoint of the IPSec connection • Authentication – Both endpoints know the same secret, and no one else has been told – Advantage • Simplicity • Authentication occurs as long as the preshared key is typed in correctly on each device ...
Chapter 9 - EECS People Web Server
... whether an attack has occurred These systems yield many more false-positive readings than do host-based IDSs, because they are attempting to read the network activity pattern to determine what is normal and what is not Management of Information Security, 2nd ed. - Chapter 9 ...
... whether an attack has occurred These systems yield many more false-positive readings than do host-based IDSs, because they are attempting to read the network activity pattern to determine what is normal and what is not Management of Information Security, 2nd ed. - Chapter 9 ...
SNMP Simple Network Management Protocol - CS-UCY
... PDU type, e.g.: 32: SNMPv1 Get 64: SNMPv2 Get Unique ID to match requests with replies Sequence of name-value pairs ...
... PDU type, e.g.: 32: SNMPv1 Get 64: SNMPv2 Get Unique ID to match requests with replies Sequence of name-value pairs ...
Remote Access—Attack Vectors
... Another recent vulnerability in this area is related to clientless VPN products. These devices retrieve content from different sites and then serve the data so it appears to be from the SSL VPN. This circumvents same-origin restrictions. A same-origin policy is designed to enforce trust domains and ...
... Another recent vulnerability in this area is related to clientless VPN products. These devices retrieve content from different sites and then serve the data so it appears to be from the SSL VPN. This circumvents same-origin restrictions. A same-origin policy is designed to enforce trust domains and ...
Using RADIUS Protocol with Check Point Security
... Document PN: 007-012883-001, Rev. A, Copyright © 2015 SafeNet, Inc., All rights reserved. ...
... Document PN: 007-012883-001, Rev. A, Copyright © 2015 SafeNet, Inc., All rights reserved. ...
MA-ILT-Lesson-v4.2
... EIGRP is a classless, advanced distance vector routing protocol that runs the DUAL algorithm. EIGRP requires you to configure an autonomous system number that must match on all routers to exchange routes. EIGRP is capable of load balancing across unequal-cost paths. EIGRP supports MD5 authen ...
... EIGRP is a classless, advanced distance vector routing protocol that runs the DUAL algorithm. EIGRP requires you to configure an autonomous system number that must match on all routers to exchange routes. EIGRP is capable of load balancing across unequal-cost paths. EIGRP supports MD5 authen ...
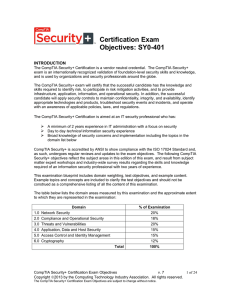
CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
Certification Exam Objectives: SY0-401
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
Iris Scanning.pdf
... Working Taking Picture: Glance at the camera Near-infrared illumination that is very safe. Creating an iris code: The picture of eye is processed by software that localizes the inner and outer boundaries of the iris ...
... Working Taking Picture: Glance at the camera Near-infrared illumination that is very safe. Creating an iris code: The picture of eye is processed by software that localizes the inner and outer boundaries of the iris ...
Cardenas_Claudia_WorkShopSlides
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
... In terms of the PHY layer most of these attacks can be counteracted by using different signals and proper configuration of the protocol. Some of MAC flaws have been fixed by the enhanced security of IEEE 802.16e but not all of them. The lack of encryption of MAC management messages that can affect t ...
wireless-mod8-Security
... settings, to authenticate and attempt to communicate with an access point. Open Authentication is the default setting. Shared Key Authentication—Allows your client adapter to communicate only with access points that have the same WEP key. This option is available only if Use Static WEP Keys is selec ...
... settings, to authenticate and attempt to communicate with an access point. Open Authentication is the default setting. Shared Key Authentication—Allows your client adapter to communicate only with access points that have the same WEP key. This option is available only if Use Static WEP Keys is selec ...
GSI Credential Management with MyProxy
... – Confidentiality: Solution using proxy encryption techniques whereby the plaintext is not exposed at list server; instead, list server simply transforms encrypted messages – Integrity and authentication: Solution using digital signatures where certificate validation is provided by list server – Ant ...
... – Confidentiality: Solution using proxy encryption techniques whereby the plaintext is not exposed at list server; instead, list server simply transforms encrypted messages – Integrity and authentication: Solution using digital signatures where certificate validation is provided by list server – Ant ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... A security association is simply the bundle of algorithms and parameters (such as keys) that is being used to encrypt and authenticate a particular flow in one direction. IPsec supports two encryption modes: Transport and ...
... A security association is simply the bundle of algorithms and parameters (such as keys) that is being used to encrypt and authenticate a particular flow in one direction. IPsec supports two encryption modes: Transport and ...
gisfi_sp_201212337
... This report introduces the subject of the “Security in Mobile Communication Systems” that is of paramount importance in the times of evolving technologies that also is challenged by threats and attacks on them. It provides an overview of the security implementations/architectures provided in the var ...
... This report introduces the subject of the “Security in Mobile Communication Systems” that is of paramount importance in the times of evolving technologies that also is challenged by threats and attacks on them. It provides an overview of the security implementations/architectures provided in the var ...
CIS Cisco IOS 15 Benchmark
... SB Products Provided As Is. CIS is providing the SB Products “as is” and “as available” without: (1) any representations, warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the secur ...
... SB Products Provided As Is. CIS is providing the SB Products “as is” and “as available” without: (1) any representations, warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the secur ...
SAML Whitepaper
... The current SAML specification defines 2 bindings: the web browser single signon binding and the SOAP binding. The ‘web browser single sign-on’ binding enables single sign-on between organizations’ web systems by creating standard ways for web session systems to communicate about web user authentica ...
... The current SAML specification defines 2 bindings: the web browser single signon binding and the SOAP binding. The ‘web browser single sign-on’ binding enables single sign-on between organizations’ web systems by creating standard ways for web session systems to communicate about web user authentica ...
Authentication
.png?width=300)
Authentication (from Greek: αὐθεντικός authentikos, ""real, genuine,"" from αὐθέντης authentes, ""author"") is the act of confirming the truth of an attribute of a single piece of data (a datum) claimed true by an entity. In contrast with identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the validity of a Website with a digital certificate, tracing the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, authentication often involves verifying the validity of at least one form of identification.