* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 1. Introduction to Data Communications
Cyber-security regulation wikipedia , lookup
Disaster recovery plan wikipedia , lookup
Information security wikipedia , lookup
Access control wikipedia , lookup
Web of trust wikipedia , lookup
Deep packet inspection wikipedia , lookup
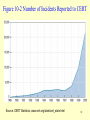
Cryptography wikipedia , lookup
History of cryptography wikipedia , lookup
Network tap wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Security-focused operating system wikipedia , lookup
Unix security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
Distributed firewall wikipedia , lookup
Chapter 10 Network Security Networking in the Internet Age by Alan Dennis 1 Copyright © 2002 John Wiley & Sons, Inc. Copyright John Wiley & Sons, Inc. All rights reserved. Reproduction or translation of this work beyond that named in Section 117 of the United States Copyright Act without the express written consent of the copyright owner is unlawful. Requests for further information should be addressed to the Permissions Department, John Wiley & Sons, Inc. Adopters of the textbook are granted permission to make back-up copies for their own use only, to make copies for distribution to students of the course the textbook is used in, and to modify this material to best suit their instructional needs. Under no circumstances can copies be made for resale. The Publisher assumes no responsibility for errors, omissions, or damages, caused by the use of these programs or from the use of the information contained herein. 2 Chapter 10. Learning Objectives • Be familiar with the major threats to network security • Be familiar with how to conduct a risk assessment • Understand how to prevent, detect, and correct disruptions, destruction, and disaster • Understand how to prevent, detect, and correct unauthorized access 3 Chapter 10. Outline • Introduction – Why networks need security – Types of Security Threats – Network Controls • Risk Assessment – Develop a Control Spreadsheet – Identify and Document the Controls – Evaluate the Network’s Security • Controlling Disruption, Destruction and Disaster – Preventing Disruption, Destruction and Disaster – Detecting Disruption, Destruction and Disaster – Correcting Disruption, Destruction and Disaster • Controlling Unauthorized Access – Preventing Unauthorized Access – Detecting Unauthorized Access – Correcting Unauthorized Access 4 Introduction 5 Introduction • Security is a major networking concern. 90% of the respondents to the 2000 Computer Security Institute/FBI Computer Crime and Security Survey reported security breaches in the last 12 months. • Information Week estimates the annual cost of security losses worldwide at $1.6 trillion. • It means more than preventing a hacker from breaking into your computer, it also includes being able to recover from temporary service problems, or from natural disasters (Figure 10-1). 6 Figure 10-1 Threats to Network Security 7 Types of Security Threats • Disruptions are the loss or reduction in network service. • Some disruptions may also be caused by or result in the destruction of data. • Natural (or manmade) disasters may occur that destroy host computers or large sections of the network. • Unauthorized access is often viewed as hackers gaining access to organizational data files and resources. However, most unauthorized access incidents involve employees. 8 Security Problems Are Growing • The Computer Emergency Response Team (CERT) at Carnegie Mellon University was established with USDoD support in 1988 after a computer virus shut down 10% of the computers on the Internet (Figure 10-2). • In 1989, CERT responded to 137 incidents. • In 2000, CERT responded to 21,756 incidents. • By this count, security incidents are growing at a rate of 100% per year. • Breaking into a computer in the U.S. is now a federal crime. 9 Figure 10-2 Number of Incidents Reported to CERT Source: CERT Statistics, www.cert.org/stats/cert_stats.html 10 Network Controls • Developing a secure network means developing mechanisms that reduce or eliminate the threats to network security, called controls. • There are three types of controls: – Preventative controls - mitigate or stop a person from acting or an event from occurring (e.g. passwords). – Detective controls - reveal or discover unwanted events (e.g., auditing software). – Corrective controls - rectify an unwanted event or a trespass (e.g., reinitiating a network circuit). 11 Network Controls • It is not enough to just establish a series of controls; personnel need to be designated as responsible for network control and security. • This includes developing controls, ensuring that they are operating effectively, and updating or replacing controls. • Controls must also be periodically reviewed to: – ensure that the control is still present (verification) – determine if the control is working as specified (testing) 12 Risk Assessment 13 Risk Assessment • Risk assessment is the process of making a network more secure, by comparing each security threat with the control designed to reduce it. • One way to do this is by developing a control spreadsheet (Figure 10-3). • Network assets are listed down the side. • Threats are listed across the top of the spreadsheet. • The cells of the spreadsheet list the controls that are currently in use to address each threat. 14 Threats Assets (with Priority) Disruption, Destruction, Disaster Fire Flood Power Circuit Virus Loss Failure Unauthorized Access External Internal Eavesdrop Intruder Intruder (92) Mail Server (90) Web Server (90) DNS Server (50) Computers on 6th floor (50) 6th floor LAN circuits (80) Building A Backbone (70) Router in Building A (30) Network Software (100) Client Database (100) Financial Database (70) Network Technical staff Figure 10-3 Sample control spreadsheet with some assets and threats 15 Network Assets (Figure 10-4) • Network assets are the network components including hardware, software and data files. • The value of an asset is not simply its replacement cost, it also includes personnel time to replace the asset along with lost revenue due to the absence of the asset. • For example, lost sales because a web server is down. • Mission critical applications are also important assets. These are programs on an information system critical to business operations. 16 Hardware Servers, such as mail servers, web servers, DNS servers, DHCP servers, and LAN file servers Client computers Devices such as hubs, switches, and routers Circuits Locally operated circuits such LANs and backbones Contracted circuits such as MAN and WAN circuits Internet access circuits Network Software Server operating systems and system settings Applications software such as mail server and web server software Client Software Operating systems and system settings Application software such as word processors Organizational Data Databases with organizational records Mission critical applications For example, for an Internet bank, the Web site is mission critical Figure 10-4 Types of Assets 17 Security Threats • A network security threat is any potentially adverse occurrence that can harm or interrupt the systems using the network, or cause a monetary loss to an organization. • Once the threats are identified they are then ranked according to their occurrence. • Figure 10-5 summarizes the most common threats to security. • For example, the average cost to clean up a virus that slips through a security system and infects an average number of computers is $150,000/virus. 18 Figure 10-5 Common Security Threats 19 Identifying and Documenting Controls • Once the specific network threats and controls have been identified, you can begin working on the network controls. • Each network component should be considered along with the specific threats to it. • Controls to address those threats are then listed in terms of how each control will prevent, detect and/or correct that threat. 20 Threats (92) Mail Server Disruption, Destruction, Disaster Fire Flood Power Circuit Virus Loss Failure 1,2 1,3 4 5, 6 7, 8 Unauthorized Access External Internal Eavesdrop Intruder Intruder 9, 10, 11 9, 10 (90) Web Server 1,2 1,3 4 5, 6 7, 8 9, 10, 11 9, 10 (90) DNS Server 1,2 1,3 4 5, 6 7, 8 9, 10, 11 9, 10 (50) Computers on 6th floor 1,2 1,3 7, 8 10, 11 10 (50) 6th floor LAN circuits 1,2 1,3 (80) Building A Backbone 1,2 1,3 (70) Router in Building A 1,2 1,3 9 9 Assets (w/ priority) 6 (30) Network Software 7, 8 9, 10, 11 9, 10 (100) Client Database 7, 8 9, 10, 11 9, 10 (100) Financial Database 7, 8 9, 10, 11 9, 10 (70) Network Technical staff 1 1 Figure 10-6 Sample control spreadsheet listing assets, threats, and controls 21 Figure 10-6 (cont.) Sample control spreadsheet list of controls Controls 1. Disaster Recovery Plan 2. Halon fire system in server room. Sprinklers in rest of building 3. Not on or below ground level 4. Uninterruptible Power Supply (UPS) on all major network servers 5. Contract guarantees from inter-exchange carriers 6. Extra backbone fiber cable laid in different conduits 7. Virus checking software present on the network 8. Extensive user training on viruses and reminders in monthly newsletter 9. Strong password software 10. Extensive user training on password security and reminders in monthly newsletter 11. Application Layer firewall 22 Evaluate the Network’s Security • The last step in designing a control spreadsheet is evaluating the adequacy of the controls and the degree of risk associated with each threat. • Based on this, priorities can be decided on for dealing with threats to network security. • The assessment can be done by the network manager, but it is better done by a team of experts chosen for their in-depth knowledge about the network and environment being reviewed. 23 Controlling Disruption, Destruction and Disaster 24 Preventing Disruption, Destruction and Disaster • Preventing disruptions, destructions and disasters mean addressing a variety of threats including: – – – – – Creating network redundancy “Preventing” natural disasters Preventing theft Preventing computer virus attacks Preventing denial-of-service attacks 25 Network Redundancy • The key to in preventing or reducing disruption, destruction and disaster - is redundancy. • Examples of components that provide redundancy include: – – – – Uninterruptible power supplies (UPS) Fault-tolerant servers Disk mirroring Disk duplexing • Redundancy can be built into other network components as well. 26 Preventing Natural Disasters • Disasters are different from disruptions since the entire site can be destroyed. • The best solution is to have a completely redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult. The most fundamental principle is to decentralize the network resources. • Other steps depend on the type of disaster to be prevented. 27 Preventing Theft • Equipment theft can also be a problem if precautions against it are not taken. • Industry sources indicate that about $1 billion is lost each year to theft of computers and related equipment. • For this reason, security plans should include an evaluation of ways to prevent equipment theft. 28 Preventing Computer Viruses • Special attention must be paid to preventing viruses that attach themselves to other programs and spread when the programs are executed. • Macroviruses attach themselves to documents and become active when the files are opened are also common. Anti-virus software packages are available to check disks and files to ensure that they are virus-free. • Incoming e-mail messages are the most common source of viruses. Attachments to incoming e-mail should be routinely checked for viruses. • The use of filtering programs that ‘clean’ incoming e-mail is also becoming common. 29 Worms • A worm is a special type of virus that spreads itself without human intervention. • Most viruses attach themselves to other programs but a worm copies itself from computer to computer. • Worms spread when the install themselves on a computer and then send copies to other computer, such as by e-mail or by using a security hole in the target computer’s operating system. 30 Detecting Disruption, Destruction & Disaster • One function of network monitoring software is to alert network managers to problems so that these can be corrected. • Detecting minor disruptions can be more difficult. • The network should also routinely log fault information to enable network managers to recognize minor service problems. • In addition, there should be a clear procedure by which network users can report problems. 31 Disaster Recovery Plans (DRP) • The goal of the disaster recovery plan (DRP) is to plan responses to possible disasters, providing for partial or complete recovery of all data, application software, network components, and physical facilities. • Critical to the DRP are backup and recovery controls that enable an organization to recover its data and restart its application software should some part of the network fail. • The DRP should also address what to do in a variety of situations, such as, if the main database is destroyed or if the data center is destroyed. 32 Elements of a Disaster Recovery Plan (see Figure 10-7) • • • • • • • • • Names of responsible individuals Staff assignments and responsibilities List of priorities of “fix-firsts” Location of alternative facilities. Recovery procedures for data communications facilities, servers and application systems. Actions to be taken under various contingencies. Manual processes. Updating and Testing procedures. Safe storage of data, software and the disaster recovery plan itself. 33 Two-Level Disaster Recovery Plans • Most large organizations have a two-level disaster recovery plan. • Level 1: When they build networks they build enough capacity and have enough spare equipment to recover from a minor disaster, such as loss of a major server or portion of the network. • Level 2: most large organizations rely on professional disaster recovery firms to provide second level support for major disasters. 34 Disaster Recovery Firms • Many large organizations outsource their disaster recovery efforts to disaster recovery firms. • Disaster recovery firms offer a range of services from secure storage for backups, to a complete networked data center that clients can use should their network be destroyed by some disaster. • Full services are not cheap, but may be worthwhile when millions of dollars of lost revenue may be at stake. 35 Controlling Unauthorized Access 36 Preventing Intruder Access • Four types of intruders attempt to gain unauthorized access to computer networks. 1. Casual hackers who only have limited knowledge of computer security. 2. Security experts whose motivation is the thrill of the hunt. 3. Professional hackers who break into corporate or government computers for specific purposes. 4. Organization employees who have legitimate access to the network but who gain access to information they are not authorized to use. 37 Preventing Unauthorized Access • A proactive approach that includes routinely testing your security systems is key to preventing unauthorized access. • Access related security issues include: – – – – – – – Security policies User profiles Physical security Dial-in security Firewalls Network address translation Encryption 38 Developing a Security Policy • The security policy should clearly define the important network components to be safeguarded along with controls needed to do that (Figure 10-8). • The most common way for a hacker to break into a system is through “social engineering” (breaking security simply by asking how). 39 Elements of a Security Policy (see Figure 10-8) • • • • • • • • Names of responsible individuals. Incident reporting system and response team. Risk assessment with priorities. Controls on access points to prevent or deter unauthorized external access. Controls within the network to ensure internal users cannot exceed their authorized access. An acceptable use policy. User training plan on security. Testing and updating plans. 40 User Profiles and Forms of Access • The limits of what users have access to on a network are determined by user profiles assigned to each user account by the net manager. • The profile specifies access details such as what data and network resources a user can access and the type of access (e.g., read, write, create, delete). • Most access is still password based, that is, users gain access based on something they know. • Many systems require users to enter a password in conjunction with something they have, such as a smart card. ATM cards work in this way. • In high-security applications, users may be required to present something they are, such as a finger, hand or the retina of their eye for scanning by a biometric system. 41 User Profiles: Managing User Access • User profiles can limit the allowable log-in days, time of day, physical locations, and the allowable number of incorrect log-in attempts. • Creating accounts and profiles is simple, as they are created when new personnel arrive. • One security problem is often created because network managers forget to remove user accounts when someone leaves an organization. 42 Managing Users • It is important to screen and classify both users and data (need to know). • The effect of any security software packages that restrict or control access to files, records, or data items should also be reviewed. • Adequate user training on network security should be provided through self-teaching manuals, newsletters, policy statements, and short courses. • A well publicized security campaign can also help deter potential intruders. 43 Physical Security • Physical security means implementing access controls so only authorized personnel have access to areas where network equipment is located. • Each network component should have its own level of physical security. • Two important areas of concern are network cabling and network devices. • Network cables should be secured behind walls. • Network devices such as hubs and switches should be secured in locked wiring closets. 44 Dial-In Security • Any organization that permits staff members to access its networks via dial-in modems opens itself to a broader range of intruders. • One strategy is to routinely change modem numbers. • Another strategy is to use call-back modems & automatic number identification (ANI) so only users dialing in from authorized locations are granted access. • One-time passwords provide a strategy for traveling employees who can’t use call-back modems and automatic number identification. 45 Firewalls • Firewalls are used to prevent intruders on the Internet from making unauthorized access and denial of service attacks to your network. • A firewall is a router, gateway, or special purpose computer that examines packets flowing into and out of the organization’s network (usually via the Internet or corporate Intranet), restricting access to that network. • The two main types of firewalls are packet level firewalls and application-level firewalls. 46 Fig. 10-9 Using a firewall to protect networks. 47 Packet Filters • A packet-level firewall (or packet filter) examines the source and destination address of packets that pass through it, only allowing packets that have acceptable addresses to pass. • Since each packet is examined separately, the firewall can’t understand what the sender’s goal is. • Packet filters may be vulnerable to IP spoofing, accomplished by changing the source address on incoming packets from their real address to an address inside the organization’s network. • While packet filters have strengthened their security since the first cases of IP spoofing, IP spoofing remains a problem. 48 Application-Level Firewalls • An application-level firewall or application gateway acts as an intermediate host computer, separating a private network from the rest of the Internet, but it works on specific applications, such as Web site access. • The application gateway acts as an intermediary between the outside client making the request and the destination server responding to that request, hiding individual computers on the network behind the firewall. • Because of the increased complexity of what they do, application level firewalls require more processing power than packet filters which can impact network performance. 49 Network Address Translation • Network address translation (NAT) is used to shield a private network from outside interference. • An NAT proxy server uses an address table, translating network addresses inside the organization into aliases for use on the Internet. So, internal IP addresses remain hidden. • Many organizations combine NAT proxy servers, packet filters and application gateways, maintaining their online resources in a “DMZ network” between the two (Figure 10-10). 50 Fig. 10-10 Typical network design using firewalls. 51 Security Holes • Security holes are made by flaws in network software that permit unintended access to the network. Operating systems often contain security holes, the details of which can be highly technical. • Once discovered, knowledge about the security hole may be quickly circulated on the Internet. • A race can then begin between hackers attempting to break into networks through the security hole and security teams working to produce a patch to eliminate the security hole. 52 Encryption • Encryption systems include 4 main components: – Plaintext: the unencrypted message – An encryption algorithm: that works like the locking mechanism to a safe – A key that works like the safe’s combination – Ciphertext is produced from the plaintext message by the encryption function. – Decryption is the same process in reverse (like a modulation/demodulation), but it doesn’t always use the same key or algorithm. Plaintext results from decryption. 53 Encryption Techniques • There are three important encryption techniques now in use: – Symmetric or private key encryption – Asymmetric or public key encryption – Digital signatures, which are based on a variation of public key encryption. 54 Symmetric Encryption • Symmetric or private key encryption, uses the same algorithm and key to both encrypt and decrypt a message. • Historically, this is the most common encryption technique. • Since the key must be distributed, however, it is vulnerable to interception. This is an important weakness of symmetric key encryption. 55 Symmetric Encryption • Strong encryption doesn’t only depend on keeping the algorithm secret, it also depends on the length of the key. • A common way to break encryption is by “brute force”, meaning trying all possible combinations until the correct key is found. • Since longer keys have more possible combinations, they are more difficult to crack. 56 Data Encryption Standard (DES) • DES is a symmetric encryption algorithm developed by IBM and maintained by the National Institute of Standards and Technology. • A 56-bit version of DES is commonly used, but can be broken by brute force. • Other symmetric encryption techniques include: – RC4 uses a 40 bit key, but can use up to 256 bits. – Triple DES (3DES) uses DES three times, effectively giving it a 168 bit key. – Advanced Encryption Standard (AES), designed to replace DES uses 128, 192 and 256 bit keys. 57 Encryption: a “dual use” technology • The U.S. government limits the export of encryption techniques since they can also be used for military purposes. • The limit is 56 bit keys, based on the DES technique were developed in the 1970s. • US policy is the focus of an ongoing policy debate between security agencies and the software industry. 58 Asymmetric or Public Key Encryption • A second popular technique is asymmetric or public key encryption (PKE). • PKE is called asymmetric since it uses two different “one way” keys: – a public key used to encrypt messages, and – a private key used to decrypt them. • PKE greatly reduces the key management problem since the private key is never distributed. • The most popular form of PKE is called RSA named after the initials of its inventors. 59 Public Key Encryption (Figure 10-11) • Public key encryption works as follows: – B (the message recipient) makes his/her public key widely available (say through the Internet). – A (the sender) then uses B’s public key to encrypt the message to be sent to B. – B then uses the B’s own private key to decrypt the message. • No security hole is created by distributing the public key, since B’s private key has never been distributed. 60 Figure 10-11 Public Key Encryption 61 Digital Signatures (see Figure 10-12) • PKE also permits authentication (digital signatures), which essentially uses PKE in reverse. The digital signature, is a small part of the message, and includes the name of the sender and other key contents. • The digital signature in the outgoing message is encrypted using the sender’s private key • The digital signature is then decrypted using the sender’s public key thus providing evidence that the message originated from the sender. • Digital signatures and public key encryption combine to provide secure and authenticated message transmission (see Figure 10-12). 62 Figure 10-12 Digital Signatures 63 Certificate Authorities (CA) • One problem with digital signatures involves verifying that the person sending the message is really who he or she says they are. • A certificate authority (CA) is a trusted organization that can vouch for the authenticity of the person of organization using authentication. • The CA sends out a digital certificate verifying the identity of a digital signature’s source. • For higher level security certification, the CA requires that a unique “fingerprint” (key) be issued by the CA for every message sent by the user. 64 Other Encryption Techniques: PGP • Pretty Good Privacy (PGP) is a PKE freeware package developed by Phil Zimmerman often used to encrypt e-mail. • PGP users make their public keys available by posting them on Web pages. • Anyone wishing to send an encrypted message to that person, simply cuts and pastes the public key from the Web page into the PGP software. The PGP software then encrypts and sends the message using that key. • PGP servers are also available that allow you to search for someone’s public key. 65 Other Encryption Techniques: SSL • Secure Sockets Layer (SSL) is a technique used on the Web that operates between the application and transport layers. • SSL combines symmetric encryption with digital signatures. SSL has four steps: – Negotiation: browser and server first agree on the encryption technique they will use (e.g., RC4, DES). – Authentication: the server authenticates itself by sending its digital signature to the browser. – Symmetric Key Exchange: browser and server exchange sym. keys used to encrypt outgoing messages. – Sym. Key Encryption w/ Dig. Signatures: encrypted messages are then sent that include digital signatures. 66 Other Encryption Techniques: IPSec • The IP Security Protocol (IPSec) technique works between the transport and network layers. • First, sender and receiver exchange two numbers using Internet Key Exchange (IKE). These are combined to create encryption keys, which are then exchanged. • Next, sender and receiver negotiate the encryption technique to be used, such as DES or 3DES. • Sender and receiver then begin transmitting data. • IPSec transmits using either transport mode, in which only the IP payload is encrypted, or tunnel mode, in which the entire IP packet is encrypted. 67 Detecting Unauthorized Access • Since unauthorized access can not always be prevented, managers need to try to detect when it has occurred. This is done using one of three types of Intrusion Detection Systems (IDSs): – Network-based IDSs install IDS sensors on network circuits and monitor packets – Host-based IDSs monitor all activity on the server as well as incoming server traffic – Application-based IDSs are a special form of host-based IDSs that monitor just one application, such as a Web server. 68 Detecting Intrusions • Intrusion detection systems use two main techniques to determine if an intrusion is in progress: • Misuse detection compares monitored activities with signatures of known attacks. If an attack is recognized the IDS issues an alert. • Anomaly detection operates in stable computing environments and looks for major deviations from the “normal” parameters of network operation. When one is detected, (e.g., a large number of failed logins), an alert is issued. • IDSs are often used in conjunction with firewalls and other security tools (See Figure 10-13). 69 Figure 10-13 Intrusion Detection System 70 Correcting Unauthorized Access • Once an unauthorized access is detected, the first step is to identify where the security breach occurred and fix it so that it will not reoccur. • In order to deter such break-ins, there has been a stiffening of computer security laws and in the legal interpretation of other laws that pertain to computer networks. • Many organizations have also taken their own steps to detect or deter intruders such by using entrapment techniques that lure hackers to a server with fake information and may even have special software to track the hacker’s origin. 71 End of Chapter 10 72