Building Capatilities for Incident Handling and Response
... An organization or team that provides, to a defined constituency, services and support for both preventing and responding to computer security incidents ...
... An organization or team that provides, to a defined constituency, services and support for both preventing and responding to computer security incidents ...
3 Responding to Incidents
... This document applies to Strategic Situational Awareness (SSAW) system activities processing Department of Defense (DoD) information and information protected under the Privacy Act of ...
... This document applies to Strategic Situational Awareness (SSAW) system activities processing Department of Defense (DoD) information and information protected under the Privacy Act of ...
11 Secure electronic communication
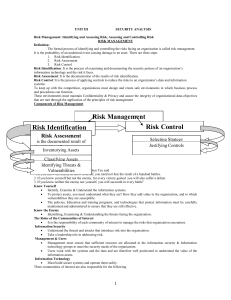
... 1 Computer and information security checklist This checklist provides a record of the 12 basic computer and information security categories that should be undertaken. The checklist is a guide only and does not describe the complete list of security activities that should be undertaken. Details of t ...
... 1 Computer and information security checklist This checklist provides a record of the 12 basic computer and information security categories that should be undertaken. The checklist is a guide only and does not describe the complete list of security activities that should be undertaken. Details of t ...
ra-5 vulnerability scanning control
... comment. These changes address two issues. One involves the need to confirm the linkage of the scanning process with other related processes such as configuration management, patch management, and change management. This would ensure, for instance, that a new component could not be introduced into t ...
... comment. These changes address two issues. One involves the need to confirm the linkage of the scanning process with other related processes such as configuration management, patch management, and change management. This would ensure, for instance, that a new component could not be introduced into t ...
IT2042-UNIT3-Notes
... roles and have correspondingly greater authority and accountability, and other staff who have assignments without special privileges. Nonemployees include contractors and consultants, members of other organizations with which the organization has a trust relationship, and strangers. Procedures fall ...
... roles and have correspondingly greater authority and accountability, and other staff who have assignments without special privileges. Nonemployees include contractors and consultants, members of other organizations with which the organization has a trust relationship, and strangers. Procedures fall ...
Best Practices for Victim Response and Reporting of Cyber Incidents
... source of the threat. A cyber incident is not the time to be creating emergency procedures or considering for the first time how best to respond. The plan should be “actionable.” It should provide specific, concrete procedures to follow in the event of a cyber incident. At a minimum, the procedures ...
... source of the threat. A cyber incident is not the time to be creating emergency procedures or considering for the first time how best to respond. The plan should be “actionable.” It should provide specific, concrete procedures to follow in the event of a cyber incident. At a minimum, the procedures ...
guidance - Public Intelligence
... source of the threat. A cyber incident is not the time to be creating emergency procedures or considering for the first time how best to respond. The plan should be “actionable.” It should provide specific, concrete procedures to follow in the event of a cyber incident. At a minimum, the procedures ...
... source of the threat. A cyber incident is not the time to be creating emergency procedures or considering for the first time how best to respond. The plan should be “actionable.” It should provide specific, concrete procedures to follow in the event of a cyber incident. At a minimum, the procedures ...
Data and Database Administration
... updates Transaction log – record of essential data for each transaction processed against the database Database change log – images of updated data – Before-image – copy before modification – After-image – copy after modification ...
... updates Transaction log – record of essential data for each transaction processed against the database Database change log – images of updated data – Before-image – copy before modification – After-image – copy after modification ...
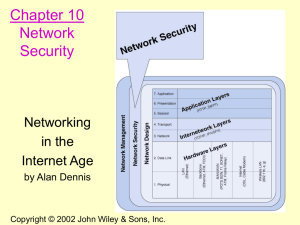
Chapter 1. Introduction to Data Communications
... Preventing Natural Disasters • Disasters are different from disruptions since the entire site can be destroyed. • The best solution is to have a completely redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult ...
... Preventing Natural Disasters • Disasters are different from disruptions since the entire site can be destroyed. • The best solution is to have a completely redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult ...
Security Policies, Standards, and Planning
... a. The policy should begin with a clear statement of purpose. The introductory section should outline the scope and applicability of the policy. b. What does this policy address? c. Who is responsible and accountable for policy implementation? d. What technologies and issues does the policy document ...
... a. The policy should begin with a clear statement of purpose. The introductory section should outline the scope and applicability of the policy. b. What does this policy address? c. Who is responsible and accountable for policy implementation? d. What technologies and issues does the policy document ...
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 1. Describe authentication process to network devices for users. 2. Discuss the need for authentication and non-repudiation of information (e.g., PKI). 3. Describe the steps to achieve authentication and confidentiality. 4. Provide for user authentication (e.g., assign passwords and access level). 5 ...
... 1. Describe authentication process to network devices for users. 2. Discuss the need for authentication and non-repudiation of information (e.g., PKI). 3. Describe the steps to achieve authentication and confidentiality. 4. Provide for user authentication (e.g., assign passwords and access level). 5 ...
Chp. 8 - Cisco Networking Academy
... Telnet servers –the Secure Shell (SSH) protocol allows for authentication and encryption of a remote management connection FTP servers - FTP can use SSL to securely exchange authentication and data. Some versions of FTP can also use SSH. File servers - In most cases, file server protocols do not off ...
... Telnet servers –the Secure Shell (SSH) protocol allows for authentication and encryption of a remote management connection FTP servers - FTP can use SSL to securely exchange authentication and data. Some versions of FTP can also use SSH. File servers - In most cases, file server protocols do not off ...
What is Beta Testing? - KV Institute of Management and Information
... intercepted and read by outsiders during transmission over the public ...
... intercepted and read by outsiders during transmission over the public ...
Network Flow Analysis in Information Security Strategy
... This material has been approved for public release and unlimited distribution except as restricted below. This material may be reproduced in its entirety, without modification, and freely distributed in written or electronic form without requesting formal permission. Permission is required for any o ...
... This material has been approved for public release and unlimited distribution except as restricted below. This material may be reproduced in its entirety, without modification, and freely distributed in written or electronic form without requesting formal permission. Permission is required for any o ...
Confidentiality
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...
... The five main phases of an information security plan are as follows; 2.1 Inspection - The most important tasks in developing an Information Security Plan are identifying the key corporate functions, the capabilities they need, when they need those capabilities, and how they interact with other funct ...
Slide 1
... • Cold backup – database is shut down during backup • Hot backup – selected portion is shut down and backed up at a given time • Backups stored in secure, off-site location ...
... • Cold backup – database is shut down during backup • Hot backup – selected portion is shut down and backed up at a given time • Backups stored in secure, off-site location ...
Power Point Slides - Organization of American States
... •Tabletop CM exercises (TTX): designed to promote preparedness for natural or man-made disasters •Based on a bio-incident scenario which takes place at an airport. Three Stages. Debriefs include recommendations for strengthening CIP and resilience •Partners: PAHO; Interpol; UN; US DHHS; FEMA; CDC •T ...
... •Tabletop CM exercises (TTX): designed to promote preparedness for natural or man-made disasters •Based on a bio-incident scenario which takes place at an airport. Three Stages. Debriefs include recommendations for strengthening CIP and resilience •Partners: PAHO; Interpol; UN; US DHHS; FEMA; CDC •T ...
Practice Questions with Solutions
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
Insider Threat and the Dark Web: Cyber Response Mini
... Crisis Management Executive that has a broad enterprise view of the organization and capable of making critical decisions while understanding impacts to the entire business. A dedicated Crisis Management Executive will result in incident management teams that are effective and not paralyzed with det ...
... Crisis Management Executive that has a broad enterprise view of the organization and capable of making critical decisions while understanding impacts to the entire business. A dedicated Crisis Management Executive will result in incident management teams that are effective and not paralyzed with det ...
Change Control Management
... Privileges of System Administrators • These individuals are assigned to ensure that the system is functioning properly for system users. • The two primary activities of administrator tasks are maintenance and monitoring. • System components requiring regular maintenance and monitoring include works ...
... Privileges of System Administrators • These individuals are assigned to ensure that the system is functioning properly for system users. • The two primary activities of administrator tasks are maintenance and monitoring. • System components requiring regular maintenance and monitoring include works ...
Incident Handling Applied Risk Management September 2002
... • Human Resources – When suspicion points internally • Law enforcement liaisons – When your event proves to be the tip of the iceberg ...
... • Human Resources – When suspicion points internally • Law enforcement liaisons – When your event proves to be the tip of the iceberg ...
Network Management Session 1 Network Basics
... Wise to check all event logs regularly – take time/trouble to find out that those ...
... Wise to check all event logs regularly – take time/trouble to find out that those ...
Springfield Data Center Program Alignment
... operations and provides for Confidentiality, Integrity, and Availability based on certain predefined criteria. ...
... operations and provides for Confidentiality, Integrity, and Availability based on certain predefined criteria. ...
Disaster recovery plan

A disaster recovery plan (DRP) is a documented process or set of procedures to recover and protect a business IT infrastructure in the event of a disaster. Such a plan, ordinarily documented in written form, specifies procedures an organization is to follow in the event of a disaster. It is ""a comprehensive statement of consistent actions to be taken before, during and after a disaster."" The disaster could be natural, environmental or man-made. Man-made disasters could be intentional (for example, an act of a terrorist) or unintentional (that is, accidental, such as the breakage of a man-made dam).Given organizations' increasing dependency on information technology to run their operations, a disaster recovery plan, sometimes erroneously called a Continuity of Operations Plan (COOP), is increasingly associated with the recovery of information technology data, assets, and facilities.