AdvancedSQLInjection
... • Should significantly reduces the risk for non application-specific components in the database, and to some extent reduces the risk to application data integrity. Does not affect the risk for application ...
... • Should significantly reduces the risk for non application-specific components in the database, and to some extent reduces the risk to application data integrity. Does not affect the risk for application ...
NEXEDGE Digital Systems
... System can automatically put calls in a queue when all Traffic Channels are busy Calls are processed when a traffic channel becomes available ...
... System can automatically put calls in a queue when all Traffic Channels are busy Calls are processed when a traffic channel becomes available ...
Datasäkerhet/Data security EDA625 – Lect2 CRYPTOGRAPHY
... LTH Electrical and Information Technology - Datasäkerhet EDA625 ...
... LTH Electrical and Information Technology - Datasäkerhet EDA625 ...
WWW Tutorial
... autonomously, routing or delivering datagrams without any coordination from the sender. ...
... autonomously, routing or delivering datagrams without any coordination from the sender. ...
Princeton International School of Mathematics and Science
... PHYSICIAN and PARENTAL PRESCRIPTION MEDICATION AUTHORIZATION FORM ...
... PHYSICIAN and PARENTAL PRESCRIPTION MEDICATION AUTHORIZATION FORM ...
Immunosuppressive Drugs
... The dosage, frequency and route of administration conform to generally accepted medical practice and is medically necessary to prevent or treat the rejection of an organ transplant. If the prescribed drug is parenteral azathioprine (J7501) or methylprednisolone (J2920, J2930), medical records co ...
... The dosage, frequency and route of administration conform to generally accepted medical practice and is medically necessary to prevent or treat the rejection of an organ transplant. If the prescribed drug is parenteral azathioprine (J7501) or methylprednisolone (J2920, J2930), medical records co ...
CIS 5357 - FSU Computer Science
... 27 = 7, 28 = 3, 29 = 6, 210 = 1 (mod 11) • 32 = 9, 33 = 5, 34 = 4, 35 = 1 (mod 11) • The residue (2 mod 11) can create all non-zero residues mod 11 via exponentiation. It is called a generator. • The residue (3 mod 11) does not have the same property. ...
... 27 = 7, 28 = 3, 29 = 6, 210 = 1 (mod 11) • 32 = 9, 33 = 5, 34 = 4, 35 = 1 (mod 11) • The residue (2 mod 11) can create all non-zero residues mod 11 via exponentiation. It is called a generator. • The residue (3 mod 11) does not have the same property. ...
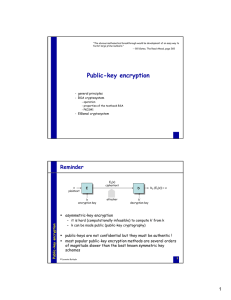
Public-key encryption
... “The obvious mathematical breakthrough would be development of an easy way to factor large prime numbers.” -- Bill Gates, The Road Ahead, page 265 ...
... “The obvious mathematical breakthrough would be development of an easy way to factor large prime numbers.” -- Bill Gates, The Road Ahead, page 265 ...
Chapter 5 - IIS Windows Server
... Cisco IOS IPS Solution Benefits • Uses the underlying routing infrastructure to provide an additional layer of security with investment protection • Attacks can be effectively mitigated to deny malicious traffic from both inside and outside the network • Provides threat protection at all entry poin ...
... Cisco IOS IPS Solution Benefits • Uses the underlying routing infrastructure to provide an additional layer of security with investment protection • Attacks can be effectively mitigated to deny malicious traffic from both inside and outside the network • Provides threat protection at all entry poin ...
The Message Brief
... Strategic communicators look for the key factor or the single most important fact in a health problem or situation that, if addressed in the communication effort, will most likely lead to the desired behavior change. The key fact may be an obstacle or an opportunity. Selection of the single most imp ...
... Strategic communicators look for the key factor or the single most important fact in a health problem or situation that, if addressed in the communication effort, will most likely lead to the desired behavior change. The key fact may be an obstacle or an opportunity. Selection of the single most imp ...
Solo-Tuned Pt II - Gateway Harmonica Club
... STAFF NOTATION As in the Part I course, this course is based on the use of staff notation, the most widely understood system of written symbols used by musicians of Western Civilization over a period of many centuries. This system uses symbols such as these . . . ...
... STAFF NOTATION As in the Part I course, this course is based on the use of staff notation, the most widely understood system of written symbols used by musicians of Western Civilization over a period of many centuries. This system uses symbols such as these . . . ...
STD Group Project – Human Behavior 2
... 4. Significance of Issue to the Public: Why is this issue important to the public? Required components of the project: 1.Turn in a written description of the PSA, answering questions 1-4, plus any other information and research about the issue, or the population the PSA addresses or serves. 2. Creat ...
... 4. Significance of Issue to the Public: Why is this issue important to the public? Required components of the project: 1.Turn in a written description of the PSA, answering questions 1-4, plus any other information and research about the issue, or the population the PSA addresses or serves. 2. Creat ...
6.1. Elliptic Curve Cryptography
... www.chetanasprojects.com end uses the receiver to measure the polarisation. According to the laws of quantum mechanics, the receiver can distinguish between rectilinear polarisations (0 and 90), or it can quickly be reconfigured to discriminate between diagonal polarisations (45 and 135); it can nev ...
... www.chetanasprojects.com end uses the receiver to measure the polarisation. According to the laws of quantum mechanics, the receiver can distinguish between rectilinear polarisations (0 and 90), or it can quickly be reconfigured to discriminate between diagonal polarisations (45 and 135); it can nev ...
Internet Control Message Protocol
... The Internet Control Message Protocol (ICMP) was developed for this task. ICMP is an error-reporting system. It is an integral part of IP and must be included in every IP implementation. This provides for consistent, understandable error messages and signals across the different versions of IP and d ...
... The Internet Control Message Protocol (ICMP) was developed for this task. ICMP is an error-reporting system. It is an integral part of IP and must be included in every IP implementation. This provides for consistent, understandable error messages and signals across the different versions of IP and d ...
PK b
... assuming the PEKS is semantically secure against an adaptive chosen message attack.(once can send a bit?) Building non-interactive public-key searchable encryption is at least as hard as building an IBE system. ...
... assuming the PEKS is semantically secure against an adaptive chosen message attack.(once can send a bit?) Building non-interactive public-key searchable encryption is at least as hard as building an IBE system. ...
Preparing E-mails Using E-mail Etiquette
... Avoid using the reply to all function as this sends your response to all recipients of the email. ...
... Avoid using the reply to all function as this sends your response to all recipients of the email. ...
離散對數密碼系統 - 國立交通大學資訊工程學系NCTU Department of
... Algorithms for Discrete Logarithm • Shanks’ algorithm (1972) – Compute L1 = {(i, gmi), i = 0, 1, …, m-1} L2 = {(i, ag-i), i = 0, 1, …, m-1} – where m = ceiling((p-1) ½) Sort L1 and L2 with respect to the 2nd coordinate. – Find the same 2nd coordinate from L1 and L2, say, (q, gmq), (r, ag-r), to get ...
... Algorithms for Discrete Logarithm • Shanks’ algorithm (1972) – Compute L1 = {(i, gmi), i = 0, 1, …, m-1} L2 = {(i, ag-i), i = 0, 1, …, m-1} – where m = ceiling((p-1) ½) Sort L1 and L2 with respect to the 2nd coordinate. – Find the same 2nd coordinate from L1 and L2, say, (q, gmq), (r, ag-r), to get ...
Will Eno`s Wakey, Wakey
... third and last play, which, I’ve only directed some short plays and it was a long time ago. But the Signature Residency–and also Jim Houghton was a guy who really did this–the whole place makes you feel like you can do just a little more than you think you can, or that you should at least try. I re ...
... third and last play, which, I’ve only directed some short plays and it was a long time ago. But the Signature Residency–and also Jim Houghton was a guy who really did this–the whole place makes you feel like you can do just a little more than you think you can, or that you should at least try. I re ...
Apply encryption to network and system security
... unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be applied to data in storage (file systems, media, etc) or in transit via network or Internet connections. Encryption can be useful to achieve appropriate ...
... unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be applied to data in storage (file systems, media, etc) or in transit via network or Internet connections. Encryption can be useful to achieve appropriate ...
A Survey of BGP Security: Issues and Solutions
... ▫ Message Authentication Codes Ensures Message Integrity and Authentication Requires Shared Secret ...
... ▫ Message Authentication Codes Ensures Message Integrity and Authentication Requires Shared Secret ...
On Designatedly Verified (Non-interactive) Watermarking Schemes
... problem. Our scheme is based on oblivious decision proof [10] mentioned above. We consider the following scenario. An image selling vendor might embed undeniable signature into his images and only allow the paying customers to verify the authentication of the images. If the vendor watermarked a imag ...
... problem. Our scheme is based on oblivious decision proof [10] mentioned above. We consider the following scenario. An image selling vendor might embed undeniable signature into his images and only allow the paying customers to verify the authentication of the images. If the vendor watermarked a imag ...
Devireddy
... TKIP resolves the key reuse in WEP by providing 128 bit “temporal key” in a dynamic way for securing data. It uses the same RC4 algorithm as WEP does and it is not considered as a long term solution. ...
... TKIP resolves the key reuse in WEP by providing 128 bit “temporal key” in a dynamic way for securing data. It uses the same RC4 algorithm as WEP does and it is not considered as a long term solution. ...
Cryptographic hashing - comp
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...
... Consider a message m is split into blocks m1, m2, …, mk without padding and hashed to a value h(m). Choose a message m’ that splits into the block m1, m2, …, mk, mk+1 (the first k blocks are identical to m’s). Therefore, h(m) is the intermediate hash value after k blocks in the computation of h(m’). ...