Ecommerce: Security and Control
... – because it use Mathematics to calculate the key. Public key cryptography uses two keys, rather than one – hence, sometimes referred to asymmetric. Symmetric encryption is still in use, and will continue to be This is because of the computational overhead associated with public key encryption ...
... – because it use Mathematics to calculate the key. Public key cryptography uses two keys, rather than one – hence, sometimes referred to asymmetric. Symmetric encryption is still in use, and will continue to be This is because of the computational overhead associated with public key encryption ...
Chapter 8: Network Security
... anyone can encrypt messages for the owner; that key is called the public key. Obviously, for such a scheme to work it must not be possible to deduce the private key from the public key. Consequently any participant can get the public key and send an encrypted message to the owner of the keys, and on ...
... anyone can encrypt messages for the owner; that key is called the public key. Obviously, for such a scheme to work it must not be possible to deduce the private key from the public key. Consequently any participant can get the public key and send an encrypted message to the owner of the keys, and on ...
Direct Deposit Authorization Form - A
... I hereby authorize A-Beautiful Pools, Inc. to initiate automatic deposits to my account at the financial institution named below. I also authorize A-Beautiful Pools, Inc. to make withdrawals from this account in the event that a credit entry is made in error. Further, I agree not to hold A-Beautiful ...
... I hereby authorize A-Beautiful Pools, Inc. to initiate automatic deposits to my account at the financial institution named below. I also authorize A-Beautiful Pools, Inc. to make withdrawals from this account in the event that a credit entry is made in error. Further, I agree not to hold A-Beautiful ...
Blue Border - Courant Institute of Mathematical Sciences
... “New function” description: log(257)*64*16 ≈ 8192 bits and it's much faster! ...
... “New function” description: log(257)*64*16 ≈ 8192 bits and it's much faster! ...
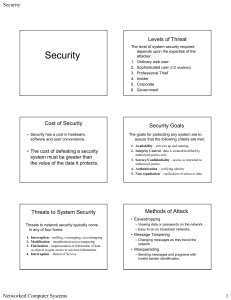
Security - The University of Texas at Dallas
... and send it to the Certificate Authority. They will investigate your identity to varying degrees, create a certificate that includes a hash encrypted with their private key, ...
... and send it to the Certificate Authority. They will investigate your identity to varying degrees, create a certificate that includes a hash encrypted with their private key, ...
Required Tasks and Exercises
... of referencing the voltage on the pin. The convention is to call the higher level of voltage HIGH and lower voltage LOW states. To make it easier when there is a need to do arithmetic we call these states 0 and 1 instead of High and LOW ...
... of referencing the voltage on the pin. The convention is to call the higher level of voltage HIGH and lower voltage LOW states. To make it easier when there is a need to do arithmetic we call these states 0 and 1 instead of High and LOW ...
Lesson#8 - ecelabs
... of referencing the voltage on the pin. The convention is to call the higher level of voltage HIGH and lower voltage LOW states. To make it easier when there is a need to do arithmetic we call these states 0 and 1 instead of High and LOW ...
... of referencing the voltage on the pin. The convention is to call the higher level of voltage HIGH and lower voltage LOW states. To make it easier when there is a need to do arithmetic we call these states 0 and 1 instead of High and LOW ...
Slides on Security
... • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address ...
... • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address ...
Mod_7-Ch11
... – AES (Advanced Encryption Standard) • Keys can be 128, 192, or 256 bits • New standard ...
... – AES (Advanced Encryption Standard) • Keys can be 128, 192, or 256 bits • New standard ...
Java Security
... classes and interfaces for handling certification paths (also known as "certificate chains"). If the user does not have a trusted copy of the public key of the CA that signed the subject's public key certificate, then another public key certificate vouching for the signing CA is required. This logic ...
... classes and interfaces for handling certification paths (also known as "certificate chains"). If the user does not have a trusted copy of the public key of the CA that signed the subject's public key certificate, then another public key certificate vouching for the signing CA is required. This logic ...
Public-Key Cryptosystems Based on Hard Problems
... We have seen that, a secure channel is not needed to establish private communication. The users must share only his encryption key in the public le and he can receive secret message. Although, participants can also establish private communication over an insecure channel without the use of a public ...
... We have seen that, a secure channel is not needed to establish private communication. The users must share only his encryption key in the public le and he can receive secret message. Although, participants can also establish private communication over an insecure channel without the use of a public ...
XML Security Standards — Overview for the Non - Events
... Security element in SOAP header Can contain Tokens, Token References, Timestamp, Signatures, Encryptions Physical order of elements determines processing order of signatures and encryptions Signed and encrypted data can appear anywhere in envelope A toolkit, not a protocol ...
... Security element in SOAP header Can contain Tokens, Token References, Timestamp, Signatures, Encryptions Physical order of elements determines processing order of signatures and encryptions Signed and encrypted data can appear anywhere in envelope A toolkit, not a protocol ...
ASSUMPTION OF RISK AND RELEASE OF CLAIMS
... representatives, to assume all the risks and responsibilities of my travel to and attendance at ______________________________. I have been fully and completely apprised of the actual and potential risks inherent in this activity. These include the risk of property damage or loss, personal injury or ...
... representatives, to assume all the risks and responsibilities of my travel to and attendance at ______________________________. I have been fully and completely apprised of the actual and potential risks inherent in this activity. These include the risk of property damage or loss, personal injury or ...
Chapter X Slides
... Availability/Protection from Denial-of Service The VoIP service should be available to users at ...
... Availability/Protection from Denial-of Service The VoIP service should be available to users at ...
Three challenges with secret key encryption
... used for data confidentiality because of their performance constraints. Public key encryption algorithms are typically used in applications involving authentication using digital signatures and key management. Some of the common public key algorithms are RonRivest, Adi Shamir, Adi Shamir, and Leonar ...
... used for data confidentiality because of their performance constraints. Public key encryption algorithms are typically used in applications involving authentication using digital signatures and key management. Some of the common public key algorithms are RonRivest, Adi Shamir, Adi Shamir, and Leonar ...
part2
... • Set s = x(1)+ y(1) < t=x(2)+y(2), k = x(2)-x(1) • See ( π(s+1),π(s+2),..,π(t) ) and transform k smallest entries to 0 and others to 1. • (0011010101) 0: horizontal, 1:vertical move • The set of such zigzag paths satisfy the axioms. • If π is a low-discrepancy sequence, digital lines are almost s ...
... • Set s = x(1)+ y(1) < t=x(2)+y(2), k = x(2)-x(1) • See ( π(s+1),π(s+2),..,π(t) ) and transform k smallest entries to 0 and others to 1. • (0011010101) 0: horizontal, 1:vertical move • The set of such zigzag paths satisfy the axioms. • If π is a low-discrepancy sequence, digital lines are almost s ...
Secure Email
... the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Security experts claim users encrypt only about one ...
... the message) and authentication (the recipient can be assured of the identity of the sender). The technical capabilities for these functions has been known for many years, but they have only been applied to Internet mail recently. – Reality Check: Security experts claim users encrypt only about one ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Digital Certificates Transport encrypted codes (public and private keys) through the firewall from one host to another Help ensure identity of the individual who owns the digital certificate Provide another layer of security in firewall ...
... Digital Certificates Transport encrypted codes (public and private keys) through the firewall from one host to another Help ensure identity of the individual who owns the digital certificate Provide another layer of security in firewall ...
Security
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
... receiver with a key can decipher the content A single (symmetric) secret key is used to encrypt and decrypt Requires the communication of the key between sender and receiver! Basis of nuclear war-head command and control security ...
The Mathematics Behind the Birthday Attack
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
... I have presented to you how message integrity is maintained in a nutshell (actually the above is a very basic model and there is more but delving too deep into different types of Message Authentication Codes would be a digression). An important concept here is that when a tag is generated, it involve ...
Authorization for Electronic Funds Transfer IMPORTANT
... After completing, please print the form for your dated signature. 2.) When returning the form, please include a blank, voided check or deposit slip. The paperwork can then be submitted by: a. Mailing to Catholic Financial Life at the above address. b. Faxing to: (414) 223-3201. c. Emailing to servic ...
... After completing, please print the form for your dated signature. 2.) When returning the form, please include a blank, voided check or deposit slip. The paperwork can then be submitted by: a. Mailing to Catholic Financial Life at the above address. b. Faxing to: (414) 223-3201. c. Emailing to servic ...
FTAA Joint Public-Private Sector Committee of Experts
... the transformation of data in order to hide its information content, establish its authenticity, prevent its undetected modification, its repudiation and unauthorized use. It can be used to protect the confidentiality of data whether in storage or in transit. A variety of applications have been deve ...
... the transformation of data in order to hide its information content, establish its authenticity, prevent its undetected modification, its repudiation and unauthorized use. It can be used to protect the confidentiality of data whether in storage or in transit. A variety of applications have been deve ...