CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
Protection Mechanisms
... – Many can be configured to notify administrators via email and numerical or text paging – Like firewall systems, require complex configurations to provide the level of detection and response desired – Either network based to protect network information assets, or host based to protect server or hos ...
... – Many can be configured to notify administrators via email and numerical or text paging – Like firewall systems, require complex configurations to provide the level of detection and response desired – Either network based to protect network information assets, or host based to protect server or hos ...
Defense In Depth
... Skilled attackers study the company and it’s network to discover every entry point to the network. These entry points may be from the Internet, a company intranet, an extranet, dial-in modems, or even the front door of the building. Once all entry points are identified, the attacker will determine t ...
... Skilled attackers study the company and it’s network to discover every entry point to the network. These entry points may be from the Internet, a company intranet, an extranet, dial-in modems, or even the front door of the building. Once all entry points are identified, the attacker will determine t ...
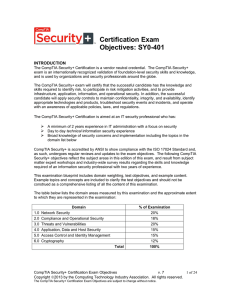
Certification Exam Objectives: SY0-401
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
Document
... Hacker/Cracker Operation Stages Discovery Exploitation Cover up Backdoor/Trojan ...
... Hacker/Cracker Operation Stages Discovery Exploitation Cover up Backdoor/Trojan ...
Slides on Security
... • Cryptography in general represents the process of encrypting a plain-text message into an unreadable cipher so that it can be sent through a network to be decrypted/deciphered by the intended recipient. • Cryptography is an important tool for security. Key Plaintext ...
... • Cryptography in general represents the process of encrypting a plain-text message into an unreadable cipher so that it can be sent through a network to be decrypted/deciphered by the intended recipient. • Cryptography is an important tool for security. Key Plaintext ...
Fujitsu`s Security Technology Based on Practical Knowledge
... and enterprises are faced with an ever-growing need to protect themselves against cyber-attacks, which continue each day to become technically more sophisticated. Measures against these attacks should aim to not only prevent malicious intrusions, but also implement possible countermeasures in case s ...
... and enterprises are faced with an ever-growing need to protect themselves against cyber-attacks, which continue each day to become technically more sophisticated. Measures against these attacks should aim to not only prevent malicious intrusions, but also implement possible countermeasures in case s ...
document
... The cost to an organization of traditional leased lines may be reasonable at first but can increase exponentially as the organization grows. A company with two branch offices, for example, can deploy just one dedicated lineto connect the two locations. If a third branch office needs to come online, ...
... The cost to an organization of traditional leased lines may be reasonable at first but can increase exponentially as the organization grows. A company with two branch offices, for example, can deploy just one dedicated lineto connect the two locations. If a third branch office needs to come online, ...
Oracle9i Security
... Oracle9iAS JAAS Oracle9iAS Single Sign-On Oracle Label Security (2000) Virtual Private Database (1998) Enterprise User Security Oracle Internet Directory Database Encryption API ...
... Oracle9iAS JAAS Oracle9iAS Single Sign-On Oracle Label Security (2000) Virtual Private Database (1998) Enterprise User Security Oracle Internet Directory Database Encryption API ...
Practice Questions with Solutions
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
Course Name : INFORMATION SECURITY
... 4. _______ is a popular session key creator protocol that requires an authentication server and a ticket-granting server a. KDC b. Kerberos ...
... 4. _______ is a popular session key creator protocol that requires an authentication server and a ticket-granting server a. KDC b. Kerberos ...
Securing IT Assets with Linux
... • It's much simpler to create malicious code if you only have to worry about one flavor of operating system or mail client or office suite, especially one that facilitates programmatic access either through built-in mechanisms (e.g. macros) or inherent security flaws (e.g. buffer overflows). • It is ...
... • It's much simpler to create malicious code if you only have to worry about one flavor of operating system or mail client or office suite, especially one that facilitates programmatic access either through built-in mechanisms (e.g. macros) or inherent security flaws (e.g. buffer overflows). • It is ...
Seminole County Public Schools: Transforming Education with
... An agile, future-ready platform Becoming a premier educational system and a national model of excellence takes both dedication and technology. NetApp FAS8040HA storage and AltaVault backup-to-cloud solutions are doing their part, providing nonstop data access and fast application response to keep ov ...
... An agile, future-ready platform Becoming a premier educational system and a national model of excellence takes both dedication and technology. NetApp FAS8040HA storage and AltaVault backup-to-cloud solutions are doing their part, providing nonstop data access and fast application response to keep ov ...
Security management
... social engineering is when one person tricks another person into sharing confidential information by posing as someone authorized to have access to that information ...
... social engineering is when one person tricks another person into sharing confidential information by posing as someone authorized to have access to that information ...
IPSec
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
... IPSec is an abbreviation for IP security, which is used to transfer data securely over unprotected networks like “Internet”. It acts at the networks layer and is part of IPv6. The protocol/process is as follows : Sender encrypts packets before sending them on the network. Receiver authenti ...
Slide 1
... competitiveness, high demands on user adaptivity, Thus, the complexity of securing such Web applications has increased significantly ...
... competitiveness, high demands on user adaptivity, Thus, the complexity of securing such Web applications has increased significantly ...
Network Security Overview
... breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability. (It can be either intentional or unintentional) Attack: An assault on system security that derives from an intelligent threat; that is, an intelligent act that is a deliberate attempt (especial ...
... breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability. (It can be either intentional or unintentional) Attack: An assault on system security that derives from an intelligent threat; that is, an intelligent act that is a deliberate attempt (especial ...
XML: Part - Houston Community College System
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...
... who they claim to be – The message was not altered – It cannot be denied the message was sent Security+ Guide to Network Security Fundamentals, 2e ...
Threats To Windows Users and Countermeasures
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
SSH - Information Services and Technology
... SSH1 was released to the public as free software with access to the source code. By the end of the year, an estimated 20,000 users in 50 countries used SSH1. ...
... SSH1 was released to the public as free software with access to the source code. By the end of the year, an estimated 20,000 users in 50 countries used SSH1. ...
Information Security Attack Tree Modeling for Enhancing Student Learning
... [G1, G21, G31, G41, G51], [G1, G21, G32, G41, G51], [G1, G21, G31, G42, G51], [G1, G21, G32, G42, G51], [G1, G22, G31, G41, G51], [G1, G22, G32, G41, G51], [G1, G22, G31, G42, G51], [G1, G22, G32, G42, G51], [G1, G23, G31, G41, G51], [G1, G23, G32, G41, G51], [G1, G23, G31, G42, G51], [G1, G23, G32, ...
... [G1, G21, G31, G41, G51], [G1, G21, G32, G41, G51], [G1, G21, G31, G42, G51], [G1, G21, G32, G42, G51], [G1, G22, G31, G41, G51], [G1, G22, G32, G41, G51], [G1, G22, G31, G42, G51], [G1, G22, G32, G42, G51], [G1, G23, G31, G41, G51], [G1, G23, G32, G41, G51], [G1, G23, G31, G42, G51], [G1, G23, G32, ...
What Cyber Criminals Know Most People Don`t?
... managing and responding to incidents as quickly as possible ...
... managing and responding to incidents as quickly as possible ...
Next-Generation Secure Computing Base
The Next-Generation Secure Computing Base (NGSCB) (codenamed Palladium and also known as Trusted Windows) is a cancelled software architecture designed by Microsoft which aimed to provide users of the Windows operating system with better privacy, security, and system integrity. NGSCB was the result of years of research and development within Microsoft to create a secure computing solution that equaled the security of closed architecture platforms, such as set-top boxes, while simultaneously preserving the backward compatibility, openness, and flexibility of the Windows operating system. The primary stated objective with NGSCB was to ""protect software from software.""Part of the Trustworthy Computing initiative when unveiled in 2002, NGSCB was expected to be integrated with the Windows Vista operating system, then known by its codename ""Longhorn."" NGSCB relied on hardware designed by members of the Trusted Computing Group to produce a parallel operation environment hosted by a new kernel called the ""Nexus"" that existed alongside Windows and provide new applications with features such as hardware-based process isolation, data encryption based on integrity measurements, authentication of a local or remote machine or software configuration, and encrypted paths for user authentication and graphics output. NGSCB would also facilitate the creation and distribution of rights management policies pertaining to the use of information.The technology was the subject of much controversy during its development, with critics contending that it could be used to impose restrictions on users, enforce vendor lock-in, and undermine fair use rights and open-source software. NGSCB was first demonstrated by Microsoft in 2003 at the Windows Hardware Engineering Conference before undergoing a revision in 2004 that would enable applications written prior to its development to benefit from its functionality. In 2005, reports stated that Microsoft would scale back its plans so that the company could ship its Windows Vista operating system by its target date of 2006. Development of NGSCB spanned almost a decade before its cancellation, one of the lengthiest development periods of a feature intended for the operating system.NGSCB differed from the technologies that Microsoft billed as pillars of Windows Vista during its development—Windows Presentation Foundation, Windows Communication Foundation, and WinFS—in that it was not built upon and did not prioritize .NET managed code during its development. While the technology has not fully materialized, aspects of NGSCB have emerged in Microsoft's BitLocker full disk encryption feature, which can optionally use the Trusted Platform Module to validate the integrity of boot and system files prior to operating system startup; the Measured Boot feature in Windows 8, the certificate attestation features in Windows 8.1, and the Device Guard feature of Windows 10.