Network Security
... • About 20% of the respondents hired reformed hackers or ethical hackers as consultants. • Only 2.6% of the respondents reported computer network attacks to law enforcements. • The mostly used prevention tool was patching (79.5%) the holes as they were released by manufacturers of hardware and softw ...
... • About 20% of the respondents hired reformed hackers or ethical hackers as consultants. • Only 2.6% of the respondents reported computer network attacks to law enforcements. • The mostly used prevention tool was patching (79.5%) the holes as they were released by manufacturers of hardware and softw ...
NITC yearly Work Plan FY2065/66
... Can disrupt not only the lives of individuals, but also the storage, transmission, and use of information Include fire, flood, earthquake, and lightning as well as volcanic eruption and insect infestation Since it is not possible to avoid many of these threats, management must implement controls ...
... Can disrupt not only the lives of individuals, but also the storage, transmission, and use of information Include fire, flood, earthquake, and lightning as well as volcanic eruption and insect infestation Since it is not possible to avoid many of these threats, management must implement controls ...
ppt
... • How do we do VOs with two port internet? • Will we see our networks become ‘campus phone switch’ of the 2010s ...
... • How do we do VOs with two port internet? • Will we see our networks become ‘campus phone switch’ of the 2010s ...
Preparing for MHRA Inspection
... If not, ensure other means but do not rely on a single backup source (such as one external hard drive) Ensure backup drives are encrypted or locked away in fireproof safe Create a backup policy so you can retrieve not just “last night’s backup” but the week or month before if ...
... If not, ensure other means but do not rely on a single backup source (such as one external hard drive) Ensure backup drives are encrypted or locked away in fireproof safe Create a backup policy so you can retrieve not just “last night’s backup” but the week or month before if ...
Visualization
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
Chapter 5 - Department of Computer Science and Information Systems
... buried within the media they are manipulating Although active content gives life to static Web pages it also introduces unique challenges for protecting the client ...
... buried within the media they are manipulating Although active content gives life to static Web pages it also introduces unique challenges for protecting the client ...
E-Commerce and Bank Security
... Prevent unauthorized access while allowing authorized user to connect ...
... Prevent unauthorized access while allowing authorized user to connect ...
PSWG Closed Door Proposal - Western Electricity Coordinating
... the public disclosure of information identified in Section 7.6.1 of the Bylaws”; including: “to receive and discuss any information that is privileged, trade secret, cyber security, critical energy infrastructure information (as defined by the FERC), protected from public disclosure by law or that t ...
... the public disclosure of information identified in Section 7.6.1 of the Bylaws”; including: “to receive and discuss any information that is privileged, trade secret, cyber security, critical energy infrastructure information (as defined by the FERC), protected from public disclosure by law or that t ...
Vulnerability analysis consists of several steps: Defining and
... Assigning relative levels of importance to the resources Identifying potential threats to each resource Developing a strategy to deal with the most serious potential problems first Defining and implementing ways to minimize the consequences if an attack occurs. (© TechTarget) Nessus - Nessus ...
... Assigning relative levels of importance to the resources Identifying potential threats to each resource Developing a strategy to deal with the most serious potential problems first Defining and implementing ways to minimize the consequences if an attack occurs. (© TechTarget) Nessus - Nessus ...
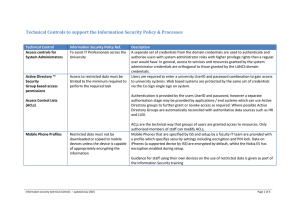
Technical Controls to support the Information
... When sending email; copying data onto, for example, CDs, laptops, phones or USB sticks; or when working outside the confines of the University you must secure information appropriately. When working with restricted information away from the University you must always use a secure mechanism such as V ...
... When sending email; copying data onto, for example, CDs, laptops, phones or USB sticks; or when working outside the confines of the University you must secure information appropriately. When working with restricted information away from the University you must always use a secure mechanism such as V ...
Something Security
... • Common critiques: (i) over-extended definitions ‘meaningless’ and/or ‘too complicated’ (eg for comparative risk assessment, executive handling); (ii) critique of ‘securitization’ • BUT: - main risks for West objectively moving down the spectrum; non-securitizing can also mean ignoring/downplaying ...
... • Common critiques: (i) over-extended definitions ‘meaningless’ and/or ‘too complicated’ (eg for comparative risk assessment, executive handling); (ii) critique of ‘securitization’ • BUT: - main risks for West objectively moving down the spectrum; non-securitizing can also mean ignoring/downplaying ...
Chapter 2: Attackers and Their Attacks
... disinformation and propaganda Deny service to legitimate computer users Commit unauthorized intrusions into systems and networks that result in critical infrastructure outages and corruption of vital data ...
... disinformation and propaganda Deny service to legitimate computer users Commit unauthorized intrusions into systems and networks that result in critical infrastructure outages and corruption of vital data ...
Certifications authenticate Blancco´s high standards
... TÜV-SÜD also endorses Blancco for storage media, noting that it is “appropriate to safely and irrecoverably erase the data on all popular types of hard drives.” The Norwegian National Security Authority The Norwegian National Security Authority (NSM) approved Blancco HMG Software for the erasure of ...
... TÜV-SÜD also endorses Blancco for storage media, noting that it is “appropriate to safely and irrecoverably erase the data on all popular types of hard drives.” The Norwegian National Security Authority The Norwegian National Security Authority (NSM) approved Blancco HMG Software for the erasure of ...
September 9 - fog.ccsf.edu
... • A graphical system for controlling a computer. The icons/images on the screen represent programs and files. • A mouse is usually used with a GUI to create a point and click navigation system. • Different from a command line interface. ...
... • A graphical system for controlling a computer. The icons/images on the screen represent programs and files. • A mouse is usually used with a GUI to create a point and click navigation system. • Different from a command line interface. ...
CH01-Testbank-NetSec5e
... 5. __________ is the use of mathematical algorithms to transform data into a form that is not readily intelligible, in which the transformation and subsequent recovery of the data depend on an algorithm and zero or more encryption keys. 6. Student grade information is an asset whose confidentialit ...
... 5. __________ is the use of mathematical algorithms to transform data into a form that is not readily intelligible, in which the transformation and subsequent recovery of the data depend on an algorithm and zero or more encryption keys. 6. Student grade information is an asset whose confidentialit ...
ppt
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...
Covert channel
... Yiqi Dai, Department of Computer Science and Technology, Tsinghua University, Beijing 10084, China ...
... Yiqi Dai, Department of Computer Science and Technology, Tsinghua University, Beijing 10084, China ...
50 Word Company Description 100 Word
... Townsend Security, the encryption company, builds data protection solutions for compliance. Rely on our encryption, key management, tokenization, and logging solutions to protect your sensitive data from loss, theft and abuse whether it rests within, or is transmitted outside, of your organization. ...
... Townsend Security, the encryption company, builds data protection solutions for compliance. Rely on our encryption, key management, tokenization, and logging solutions to protect your sensitive data from loss, theft and abuse whether it rests within, or is transmitted outside, of your organization. ...
Presentation Prepared By: Raghda Zahran
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
Mullvad Barnprogram
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
The Role of Security in an Introductory Course
... • What do we teach? • When do we teach it? • Who do we teach it to? ...
... • What do we teach? • When do we teach it? • Who do we teach it to? ...