Internet History
... Stand alone computers Need for sharing resources Physical vs. Virtual access Security issues Centralized vs. Decentralized communication Circuit switched Packet switched ...
... Stand alone computers Need for sharing resources Physical vs. Virtual access Security issues Centralized vs. Decentralized communication Circuit switched Packet switched ...
Secure Group Communications in Wireless Sensor Networks
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
... Its long-term goal is to acquire and save Internet topological data over a long period of time. This data has been used in the study of routing problems and changes, DDoS attacks, and graph theory. IPSonar inject small non-intrusive measurement packets ...
the importance of securing workstations
... employees to store as little as possible on their own workstations might have a small positive effect, but such efforts can be obstructed by real-world needs, as well as by the fact that an attacker is likely to gain access to the same centralized resources as the owner of a compromised machine. IT ...
... employees to store as little as possible on their own workstations might have a small positive effect, but such efforts can be obstructed by real-world needs, as well as by the fact that an attacker is likely to gain access to the same centralized resources as the owner of a compromised machine. IT ...
Securing a Host Computer
... Operating Systems With built-in security features, operating systems play a key role in Host Security. Operating systems allow you to create and set passwords for user accounts. The operating system has a system administrator account that a user/owner can use to manage access permissions, passwo ...
... Operating Systems With built-in security features, operating systems play a key role in Host Security. Operating systems allow you to create and set passwords for user accounts. The operating system has a system administrator account that a user/owner can use to manage access permissions, passwo ...
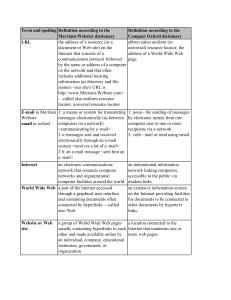
Table 9.1 Spelling and definitions.pdf
... 1: noun - the sending of messages by electronic means from one computer user to one or more recipients via a network. 2: verb - mail or send using email. ...
... 1: noun - the sending of messages by electronic means from one computer user to one or more recipients via a network. 2: verb - mail or send using email. ...
Tech Vision 2035 - Cyber law and regulatory strategies
... SERIOUS HINDERING WITHOUT RIGHT OF THE FUNCTIONING OF A COMPUTER SYSTEM BY INPUTTING, TRANSMITTING, ...
... SERIOUS HINDERING WITHOUT RIGHT OF THE FUNCTIONING OF A COMPUTER SYSTEM BY INPUTTING, TRANSMITTING, ...
Social engineering - Information Systems
... right to obtain about others and how the information can be used ...
... right to obtain about others and how the information can be used ...
Document
... Use a network, or bot-net, of compromised, remotely controlled systems to coordinate attacks and to distribute phishing schemes, spam, and malware attacks. The services of these networks are sometimes made available on underground markets. ...
... Use a network, or bot-net, of compromised, remotely controlled systems to coordinate attacks and to distribute phishing schemes, spam, and malware attacks. The services of these networks are sometimes made available on underground markets. ...
Chapter 1 Study Outline
... B. Information security involves identifying the threats and vulnerabilities of the organization and managing them appropriately. C. Implementing a proper information security system is not a one-time activity. It requires a constant vigilance against new security threats that might arise. D. The ne ...
... B. Information security involves identifying the threats and vulnerabilities of the organization and managing them appropriately. C. Implementing a proper information security system is not a one-time activity. It requires a constant vigilance against new security threats that might arise. D. The ne ...
Basic Networking Terminology
... 2. A network device that forwards data packets from one network to another 4. a system designed to prevent unauthorized access to or from a private network 6. a network that spans a relatively large geographical area and typically consists of two or more local-area networks 7. The amount of data tha ...
... 2. A network device that forwards data packets from one network to another 4. a system designed to prevent unauthorized access to or from a private network 6. a network that spans a relatively large geographical area and typically consists of two or more local-area networks 7. The amount of data tha ...
Information manager\ manager responsible for designing and
... Browser\ software supporting the graphics and linking capabilities necessary to navigate the world wide web. Search engine\ tool that searches web pages containing the use's search terms and then displays that math. Intranet\ private network of internal web sites and other sources of information ava ...
... Browser\ software supporting the graphics and linking capabilities necessary to navigate the world wide web. Search engine\ tool that searches web pages containing the use's search terms and then displays that math. Intranet\ private network of internal web sites and other sources of information ava ...
Chapter 14 Network Security - Northern Arizona University
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
Chapter 14 Network Security
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
... • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by th ...
Emerging Threats to Business Security
... legislation in Europe and the United States, the danger to businesses in terms of liability for data theft/loss will remain high for the foreseeable future. The various versions of "Storm Worm" still present the biggest single threat for the beginning of 2008, while the Zlob Trojan family is also be ...
... legislation in Europe and the United States, the danger to businesses in terms of liability for data theft/loss will remain high for the foreseeable future. The various versions of "Storm Worm" still present the biggest single threat for the beginning of 2008, while the Zlob Trojan family is also be ...
Intelligence and Security Informatics (ISI) is the study of the
... Intelligence and Security Informatics (ISI) is the study of the development and use of advanced information systems and technologies for national, international, and societal security-related applications. ISI topics include ISI data management, data and text mining for ISI applications, terrorism i ...
... Intelligence and Security Informatics (ISI) is the study of the development and use of advanced information systems and technologies for national, international, and societal security-related applications. ISI topics include ISI data management, data and text mining for ISI applications, terrorism i ...
National Initiative For Cybersecurity Education (NICE)
... information to both reduce fraud and enhance the user experiences Daon o Demonstrates how senior citizens and all consumers can benefit from a digitally connected, consumer friendly ecosystem with multiple parties online Resilient Network Systems o Demonstrates that sensitive health and educatio ...
... information to both reduce fraud and enhance the user experiences Daon o Demonstrates how senior citizens and all consumers can benefit from a digitally connected, consumer friendly ecosystem with multiple parties online Resilient Network Systems o Demonstrates that sensitive health and educatio ...
PPT
... Key Establishment Each Sensor node establishes three kinds of keys: a NodeBase key that can be used for communication with the base station, pair-wise keys for immediate communication with neighbors and a group key that allows secure one to many communications. These keys provide flexibility in the ...
... Key Establishment Each Sensor node establishes three kinds of keys: a NodeBase key that can be used for communication with the base station, pair-wise keys for immediate communication with neighbors and a group key that allows secure one to many communications. These keys provide flexibility in the ...
Computer Science 9616a, Fall 2011 Project Description Your project
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
chapter 3
... Prolexic: ‘itsoknoproblembro’ DDoS attacks are highly sophisticated. Experts from Prolexic Technologies claim a new type of distributed denial-of-service (DDoS) attack has not only increased in size, but also reached a new level of sophistication. DDoS attacks have recently caused a lot of problems ...
... Prolexic: ‘itsoknoproblembro’ DDoS attacks are highly sophisticated. Experts from Prolexic Technologies claim a new type of distributed denial-of-service (DDoS) attack has not only increased in size, but also reached a new level of sophistication. DDoS attacks have recently caused a lot of problems ...
The Top Ten of Security
... – The “reading room” for SANS, a large computer security training organization. ...
... – The “reading room” for SANS, a large computer security training organization. ...
Click Here
... from being termed cutting edge to becoming obsolete. There is technology in everything and everywhere. Information Technology has a profound influence on all branches of science, engineering, management as well. This event includes oral or poster presentation of research papers grouped into parallel ...
... from being termed cutting edge to becoming obsolete. There is technology in everything and everywhere. Information Technology has a profound influence on all branches of science, engineering, management as well. This event includes oral or poster presentation of research papers grouped into parallel ...
C.2. Vulnerabilities
... in The Atlantic, he carefully avoids revealing anything he thinks might be sensitive. The disk contained more than 1,000 documents, many of them encrypted with relatively weak encryption. Cullison found draft mission plans and white papers setting forth ideological and philosophical arguments for th ...
... in The Atlantic, he carefully avoids revealing anything he thinks might be sensitive. The disk contained more than 1,000 documents, many of them encrypted with relatively weak encryption. Cullison found draft mission plans and white papers setting forth ideological and philosophical arguments for th ...
coms3995 - Computer Science, Columbia University
... – Causes of security failures (stack attacks, information leakage, privilege escalation, denial-of-service, social engineering, ...) – Isolation and defense-in-depth – Authentication, authorization and non-repudiation – Core concepts of encryption and hashing – Introduction to public key cryptograph ...
... – Causes of security failures (stack attacks, information leakage, privilege escalation, denial-of-service, social engineering, ...) – Isolation and defense-in-depth – Authentication, authorization and non-repudiation – Core concepts of encryption and hashing – Introduction to public key cryptograph ...
Network security - Pravin Shetty > Resume
... Internetwork security is not simple as it might first appear. In developing a particular security measure one has to consider potential countermeasures. Because of the countermeasures the problem itself becomes complex. Once you have designed the security measure, it is necessary to decide where to ...
... Internetwork security is not simple as it might first appear. In developing a particular security measure one has to consider potential countermeasures. Because of the countermeasures the problem itself becomes complex. Once you have designed the security measure, it is necessary to decide where to ...