Richard D - Expert Witness Network
... Establishing a proven record of steadfast leadership, managerial and administrative skills; he has been principally involved in the planning, coordination and management of large scale and discreet security operations, both domestic and foreign, in the most hostile environs. Providing consistent, po ...
... Establishing a proven record of steadfast leadership, managerial and administrative skills; he has been principally involved in the planning, coordination and management of large scale and discreet security operations, both domestic and foreign, in the most hostile environs. Providing consistent, po ...
Orange Book Summary - UMBC Center for Information Security and
... System Evaluation Criteria, known as the Orange Book. Although originally written for military systems, the security classifications are now broadly used within the computer industry, You can get further information on the Orange Book and Rainbow Series by looking at the Orange Book Links page. Exam ...
... System Evaluation Criteria, known as the Orange Book. Although originally written for military systems, the security classifications are now broadly used within the computer industry, You can get further information on the Orange Book and Rainbow Series by looking at the Orange Book Links page. Exam ...
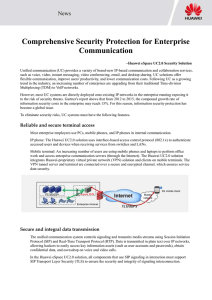
Comprehensive Security Protection for
... The Huawei UC2.0 solution offers end-to-end security protection that covers terminals (both fixed and mobile ones), networks, servers, and applications. The refined user behavior management function protects key information assets of an enterprise. This solution allows enterprises to enjoy efficient ...
... The Huawei UC2.0 solution offers end-to-end security protection that covers terminals (both fixed and mobile ones), networks, servers, and applications. The refined user behavior management function protects key information assets of an enterprise. This solution allows enterprises to enjoy efficient ...
PowerPoint Presentation - Lead
... • Is the process of preventing and detecting unauthorized use of your computer • Prevention measures help you to stop unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were succes ...
... • Is the process of preventing and detecting unauthorized use of your computer • Prevention measures help you to stop unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were succes ...
Computer Networking and Security
... The course provides an introduction to the computer hardware and software skills as well as introductory networking skills needed to help meet the growing demand for entry-level information and communication technology (ICT) professionals. The curriculum covers the fundamentals of PC technology and ...
... The course provides an introduction to the computer hardware and software skills as well as introductory networking skills needed to help meet the growing demand for entry-level information and communication technology (ICT) professionals. The curriculum covers the fundamentals of PC technology and ...
Orange
... Introduction This document is a summary of the US Department of Defense Trusted Computer System Evaluation Criteria, known as the Orange Book. Although originally written for military systems, the security classifications are now broadly used within the computer industry, You can get further informa ...
... Introduction This document is a summary of the US Department of Defense Trusted Computer System Evaluation Criteria, known as the Orange Book. Although originally written for military systems, the security classifications are now broadly used within the computer industry, You can get further informa ...
Test Bank for Crypto..
... 12. All the techniques for providing security have two components: a security- related transformation on the information to be sent and some secret information shared by the two principals. ...
... 12. All the techniques for providing security have two components: a security- related transformation on the information to be sent and some secret information shared by the two principals. ...
SECURITY
... “The problem is that security measures such as cryptography, secure kernels, Firewalls and everything else work much better in theory than they do in practice. In other words: Security flaws in the implementation are much more common and much more serious than security flaws in design. Design is ab ...
... “The problem is that security measures such as cryptography, secure kernels, Firewalls and everything else work much better in theory than they do in practice. In other words: Security flaws in the implementation are much more common and much more serious than security flaws in design. Design is ab ...
Access Control, Operations Security, and Computer Forensics
... • Terminal Access Controller Access Control System • Provides remote authentication and related services to authentication server in UNIX systems • User password administered in a central database rather than in individual routers • TACACS enabled network device prompts for user name and static pass ...
... • Terminal Access Controller Access Control System • Provides remote authentication and related services to authentication server in UNIX systems • User password administered in a central database rather than in individual routers • TACACS enabled network device prompts for user name and static pass ...
Factsheet - KFSensor
... to edit complex configuration files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networ ...
... to edit complex configuration files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networ ...
Computer Systems Security
... application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
... application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
Firewall
... • given system has identified a user • determine what resources they can access • general model is that of access matrix with – subject - active entity (user, process) – object - passive entity (file or resource) – access right – way object can be accessed ...
... • given system has identified a user • determine what resources they can access • general model is that of access matrix with – subject - active entity (user, process) – object - passive entity (file or resource) – access right – way object can be accessed ...
Data Mining
... Although data mining is a relatively new term, the technology is not. Businesses have used computer programs to sift through volumes of supermarket scanner data and analyse the market for years. However, continuous improvements in computer processing power, disk storage, and statistical software hav ...
... Although data mining is a relatively new term, the technology is not. Businesses have used computer programs to sift through volumes of supermarket scanner data and analyse the market for years. However, continuous improvements in computer processing power, disk storage, and statistical software hav ...
Charles Whitfield Jr
... Monitoring the network’s performance, operating and maintaining a diagnostic modem network and performing first level corrective maintenance for related communication hardware and software problems. ...
... Monitoring the network’s performance, operating and maintaining a diagnostic modem network and performing first level corrective maintenance for related communication hardware and software problems. ...
mathe_CoDesignForSecureEmbeddedSystems_TrustApril06Poster
... A DSML Example with the Security Extension AADL with RBAC and Partitioning Architectural Analysis and Design Language (AADL) • Standard by SAE Aerospace (AS5506) • Developed to model embedded systems with challenging resource constraints ...
... A DSML Example with the Security Extension AADL with RBAC and Partitioning Architectural Analysis and Design Language (AADL) • Standard by SAE Aerospace (AS5506) • Developed to model embedded systems with challenging resource constraints ...
Hostile Scripts (Zararlı Kod Parçacıkları)
... anywhere to run an executable program on your server and even send their own programs to run on your server. An open window like this on a server is not the safest thing to have, and security issues are involved. CGI scripts present security problems to cyberspace in several ways including and follo ...
... anywhere to run an executable program on your server and even send their own programs to run on your server. An open window like this on a server is not the safest thing to have, and security issues are involved. CGI scripts present security problems to cyberspace in several ways including and follo ...
How Client/Server Networks Work
... here’s a good chance the office computer you use to access data and files, send e-mail, access the Internet, and print out reports is a small piece of a larger puzzle known as a network. Whether it involves two computers connected by a cable or hundreds of computers linked by telephone lines, networ ...
... here’s a good chance the office computer you use to access data and files, send e-mail, access the Internet, and print out reports is a small piece of a larger puzzle known as a network. Whether it involves two computers connected by a cable or hundreds of computers linked by telephone lines, networ ...
Cradlepoint 4G LTE Parallel Networking
... Save time and reduce scope: Parallel networks reduce the amount of time and expertise needed to segment networks based on application, and limit the effort required for maintaining PCI Compliance on the network used for transmitting cardholder data. Limit risk: If an employee device or third-party n ...
... Save time and reduce scope: Parallel networks reduce the amount of time and expertise needed to segment networks based on application, and limit the effort required for maintaining PCI Compliance on the network used for transmitting cardholder data. Limit risk: If an employee device or third-party n ...
Jaden Terry CIS 280 Final Network Security From browsing the
... others that hackers use today. There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed thr ...
... others that hackers use today. There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed thr ...
Cybersecurity and Information Assurance PPT
... • Physical security awareness training (training for suspicious activities) ...
... • Physical security awareness training (training for suspicious activities) ...
1 *Programming .12 †*Software systems analysis and design
... algorithms, integrated development environments, software engineering Class algorithms discussed solely from a theoretical perspective, without regard to computer implementation, in 518.1. Class a specific application of programming within computer science with the application in 005.4–005.8 or 006, ...
... algorithms, integrated development environments, software engineering Class algorithms discussed solely from a theoretical perspective, without regard to computer implementation, in 518.1. Class a specific application of programming within computer science with the application in 005.4–005.8 or 006, ...
SNT Introduces Cyber Warfare Communications Effects Solution for
... digital replicas of physical networks in virtual space – indistinguishable from a real network. SVNs are based on emulation, which enables them able to interoperate with applications, devices, management tools, threats, and people – at real time speed. In contrast to widely used simulation systems, ...
... digital replicas of physical networks in virtual space – indistinguishable from a real network. SVNs are based on emulation, which enables them able to interoperate with applications, devices, management tools, threats, and people – at real time speed. In contrast to widely used simulation systems, ...
Cisco Discovery 1 Module 08 Quiz Picture Descriptions
... Data loss Identity theft Information theft Data manipulation Disruption of service. ...
... Data loss Identity theft Information theft Data manipulation Disruption of service. ...
Computer security - University of London International Programmes
... Units 2 to 5 contain the core computer security theory of this module In Unit 2 you are introduced to the fundamental design principles of computer security. These will be referred to throughout the rest of this module. Unit 3 investigates the important topic of access control. You will be introduce ...
... Units 2 to 5 contain the core computer security theory of this module In Unit 2 you are introduced to the fundamental design principles of computer security. These will be referred to throughout the rest of this module. Unit 3 investigates the important topic of access control. You will be introduce ...
Cybersecurity for Asset Managers: Shielding Your Firm
... prevent and recover from an attack. To become more cyber resilient, firms should not only incorporate perimeter security, but also implement business risk/reward decision making, cyber risk management and control techniques throughout their business processes. They should also secure buy-in from the ...
... prevent and recover from an attack. To become more cyber resilient, firms should not only incorporate perimeter security, but also implement business risk/reward decision making, cyber risk management and control techniques throughout their business processes. They should also secure buy-in from the ...