Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
Attacks and Mitigations
... – payload : malicious code carried by attack vectors -- spyware, Trojan-horses, dialers, destructive code and other malware. Some attacks deliver multiple payloads (warheads). – For example, worms attack through the network connection to get in. That's just the first step. Worms usually carry an ins ...
... – payload : malicious code carried by attack vectors -- spyware, Trojan-horses, dialers, destructive code and other malware. Some attacks deliver multiple payloads (warheads). – For example, worms attack through the network connection to get in. That's just the first step. Worms usually carry an ins ...
AccessControlSimulation
... audits, along with a lack of fully effective compensating and mitigating controls, impair IRS's ability to ensure that its financial and taxpayer information is secure from internal threats. This reduces IRS's assurance that its financial statements and other financial information are fairly present ...
... audits, along with a lack of fully effective compensating and mitigating controls, impair IRS's ability to ensure that its financial and taxpayer information is secure from internal threats. This reduces IRS's assurance that its financial statements and other financial information are fairly present ...
Network and Systems Security
... Agree a Network Architecture that would reduce the exposure of Networked systems and provide Inherent containment measures Establish a Computer Incident Response Team to handle incidents in a structured and coordinated way Raise awareness of Security issues. Security is not someone else’s problem it ...
... Agree a Network Architecture that would reduce the exposure of Networked systems and provide Inherent containment measures Establish a Computer Incident Response Team to handle incidents in a structured and coordinated way Raise awareness of Security issues. Security is not someone else’s problem it ...
Determined Human Adversaries: Mitigations
... Preferably, plan to involve Microsoft CSS Sec as soon as possible ...
... Preferably, plan to involve Microsoft CSS Sec as soon as possible ...
Phishing and whaling – Don`t get hooked!
... Another week and another article in the news media of an organisation fooled in transferring money to a fraudster. The article contained the following description of the common modus operandi: “Emails which appeared to be from a company or organisation's CEO or managing director were sent to the CFO ...
... Another week and another article in the news media of an organisation fooled in transferring money to a fraudster. The article contained the following description of the common modus operandi: “Emails which appeared to be from a company or organisation's CEO or managing director were sent to the CFO ...
download
... Data warehousing – large scale database technology for organizing and storing vast quantities of data, enabling data mining analysis Decision support system (DSSs) – Computer systems used to evaluate alternative decision choises Enterprise resource planning system (ERPs) – Systems designed to provid ...
... Data warehousing – large scale database technology for organizing and storing vast quantities of data, enabling data mining analysis Decision support system (DSSs) – Computer systems used to evaluate alternative decision choises Enterprise resource planning system (ERPs) – Systems designed to provid ...
Malicious Cryptography : Exposing Cryptovirology
... Foreword Terms such as cryptovirology, malware, kleptogram, or kleptography may be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” b ...
... Foreword Terms such as cryptovirology, malware, kleptogram, or kleptography may be unfamiliar to the reader, but the basic concepts associated with them certainly are familiar. Everyone knows—often from sad experience—about viruses, Trojan horses, and worms and many have had a password “harvested” b ...
Foundations of Information Security Webcast
... – All access to systems – All intrusion attempts – Financial transactions – Access to sensitive data Uses – Digital forensics – Monitoring of security – Improving performance ...
... – All access to systems – All intrusion attempts – Financial transactions – Access to sensitive data Uses – Digital forensics – Monitoring of security – Improving performance ...
Foundations of Information Security Webcast - ABA
... – All access to systems – All intrusion attempts – Financial transactions – Access to sensitive data Uses – Digital forensics – Monitoring of security – Improving performance ...
... – All access to systems – All intrusion attempts – Financial transactions – Access to sensitive data Uses – Digital forensics – Monitoring of security – Improving performance ...
Click here to access the presentation.
... Visualization tools are the fundamental user interface and must facilitate “ease of use”, reduce FSR dependencies, and accelerate training times ...
... Visualization tools are the fundamental user interface and must facilitate “ease of use”, reduce FSR dependencies, and accelerate training times ...
Video-surveillance Citizen Network
... The professional point-to-multipoint ARBA Pro solution by Albentia Systems was selected because it has been specially designed for video-surveillance and security applications. It is a solution with extraordinary spectral efficiency, QoS and powerful security mechanisms which, combined with the robu ...
... The professional point-to-multipoint ARBA Pro solution by Albentia Systems was selected because it has been specially designed for video-surveillance and security applications. It is a solution with extraordinary spectral efficiency, QoS and powerful security mechanisms which, combined with the robu ...
The Advanced Penetration Testing Boot Camp
... “The worst case scenario that I can think of, which is 100 percent possible with these devices, would be to load a compromised firmware update onto a programmer and … the compromised programmer would then infect the next pacemaker or ICD [implantable cardioverter-defibrillators] and then each would ...
... “The worst case scenario that I can think of, which is 100 percent possible with these devices, would be to load a compromised firmware update onto a programmer and … the compromised programmer would then infect the next pacemaker or ICD [implantable cardioverter-defibrillators] and then each would ...
Understanding Internetworking Infrastructure
... Hacker: An outside person who has penetrated a computer system, usually with no criminal intent. Cracker: A malicious hacker. Social engineering: Getting around security systems by tricking computer users into revealing sensitive information or gaining unauthorized access privileges. Cybercrimes: Il ...
... Hacker: An outside person who has penetrated a computer system, usually with no criminal intent. Cracker: A malicious hacker. Social engineering: Getting around security systems by tricking computer users into revealing sensitive information or gaining unauthorized access privileges. Cybercrimes: Il ...
Countering Evolving Threats in Distributed Applications
... Signatures: Phishing • Next for phishing attacks • Phishing specific features are created – Word features determined using word frequency counting – Based on common phishing features, e.g., # links, # image tags – Sentiment analysis for determining words conveying sense of change and urgency that at ...
... Signatures: Phishing • Next for phishing attacks • Phishing specific features are created – Word features determined using word frequency counting – Based on common phishing features, e.g., # links, # image tags – Sentiment analysis for determining words conveying sense of change and urgency that at ...
Principles of Computer Security
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
Security Introduction PowerPoint
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
SAFEnet Becomes First PACS Platform to
... DIACAP certification will allow MonDyn to further generate new business from DoD clients and continue to support its current Defense Department customers with Unified Security and Identity Management solutions across the globe. MonDyn’s SAFEnet Unified Command and Control Platform has been selected ...
... DIACAP certification will allow MonDyn to further generate new business from DoD clients and continue to support its current Defense Department customers with Unified Security and Identity Management solutions across the globe. MonDyn’s SAFEnet Unified Command and Control Platform has been selected ...
Introduction (Powerpoint)
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
... Detection (and correction) of intentional and accidental modifications of data in a computer system Various examples of modification ...
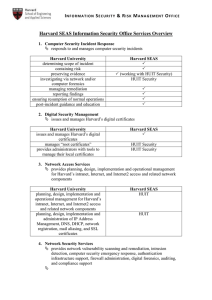
Harvard SEAS Information Security Office Services Overview
... Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers that exhibit characteristics consistent with infection by spyware, trojan horse or o ...
... Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers that exhibit characteristics consistent with infection by spyware, trojan horse or o ...
Secure Streaming Media
... storage devices such as a personal video recorder or at any point in the distribution chain without any change to software or hardware of third parties. such as proxies, NATs, firewalls, caches, storage devices, and client hardware/software processes. ...
... storage devices such as a personal video recorder or at any point in the distribution chain without any change to software or hardware of third parties. such as proxies, NATs, firewalls, caches, storage devices, and client hardware/software processes. ...